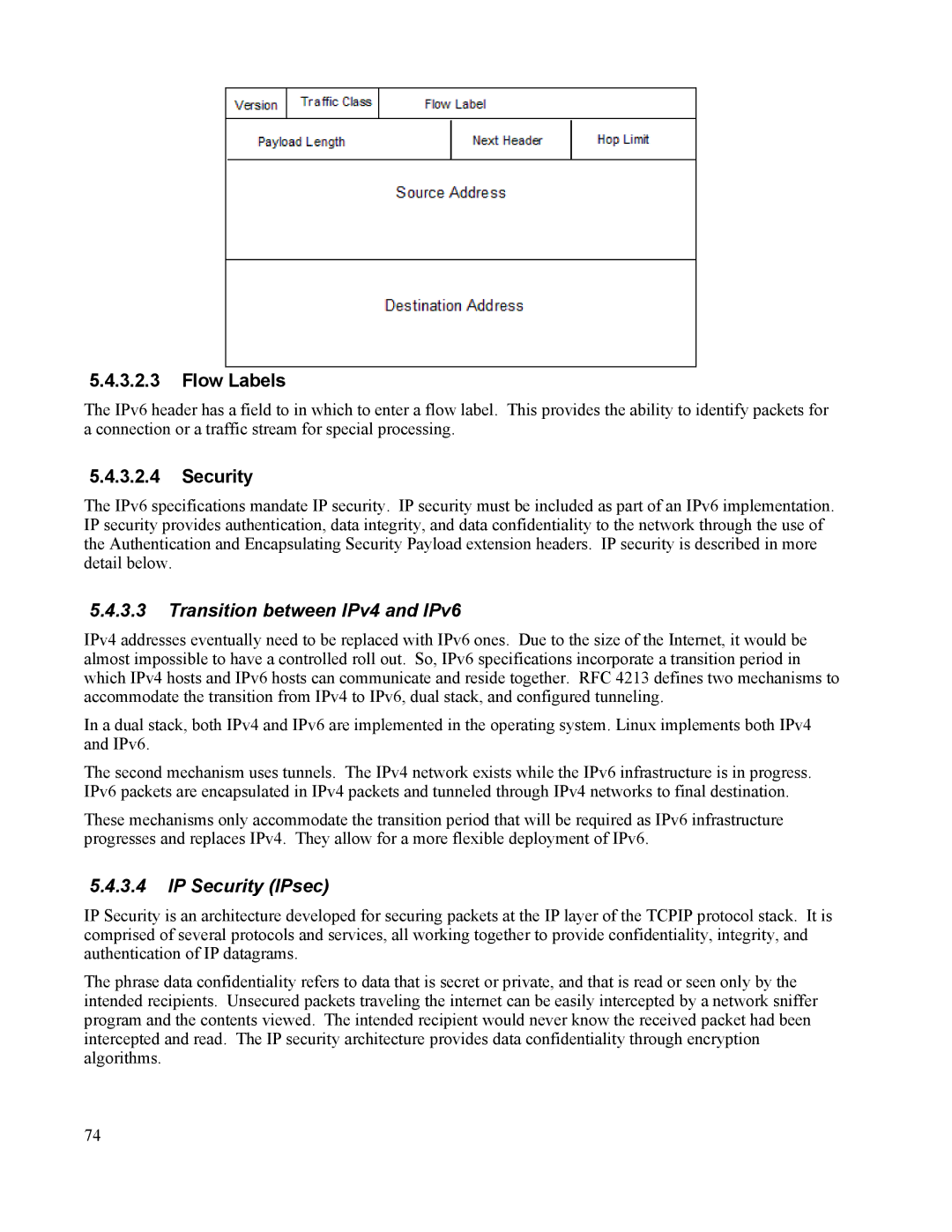
5.4.3.2.3Flow Labels
The IPv6 header has a field to in which to enter a flow label. This provides the ability to identify packets for a connection or a traffic stream for special processing.
5.4.3.2.4Security
The IPv6 specifications mandate IP security. IP security must be included as part of an IPv6 implementation. IP security provides authentication, data integrity, and data confidentiality to the network through the use of the Authentication and Encapsulating Security Payload extension headers. IP security is described in more detail below.
5.4.3.3Transition between IPv4 and IPv6
IPv4 addresses eventually need to be replaced with IPv6 ones. Due to the size of the Internet, it would be almost impossible to have a controlled roll out. So, IPv6 specifications incorporate a transition period in which IPv4 hosts and IPv6 hosts can communicate and reside together. RFC 4213 defines two mechanisms to accommodate the transition from IPv4 to IPv6, dual stack, and configured tunneling.
In a dual stack, both IPv4 and IPv6 are implemented in the operating system. Linux implements both IPv4 and IPv6.
The second mechanism uses tunnels. The IPv4 network exists while the IPv6 infrastructure is in progress. IPv6 packets are encapsulated in IPv4 packets and tunneled through IPv4 networks to final destination.
These mechanisms only accommodate the transition period that will be required as IPv6 infrastructure progresses and replaces IPv4. They allow for a more flexible deployment of IPv6.
5.4.3.4IP Security (IPsec)
IP Security is an architecture developed for securing packets at the IP layer of the TCPIP protocol stack. It is comprised of several protocols and services, all working together to provide confidentiality, integrity, and authentication of IP datagrams.
The phrase data confidentiality refers to data that is secret or private, and that is read or seen only by the intended recipients. Unsecured packets traveling the internet can be easily intercepted by a network sniffer program and the contents viewed. The intended recipient would never know the received packet had been intercepted and read. The IP security architecture provides data confidentiality through encryption algorithms.
74