The transport layer consists of the TCP, UDP and similar protocols.
The application layer consists of all the various application clients and servers, such as the Samba file and print server, the Apache web server, and others. Some of the
Network devices form the bottom layer of the protocol stack. They use a
Output interfaces receive packets from the network layer, perform error checks, and then send the packets out over the physical medium. The main functionality of IP is routing:
•It checks incoming packets to see if they are for the host computer or if they need to be forwarded.
•It defragments packets if necessary and delivers them to the transport protocols.
•It has a dynamic database of routes for outgoing packets
•It addresses and fragments them if necessary before sending them down to the link layer.
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the most commonly used transport layer protocols. UDP simply provides a framework for addressing packets to ports within a computer, whereas TCP allows more complex
Moving up the transport layer, next is the INET (for internet) layer, which forms the intermediate layer between the transport layer and application sockets. The INET layer implements the sockets owned by the applications. All
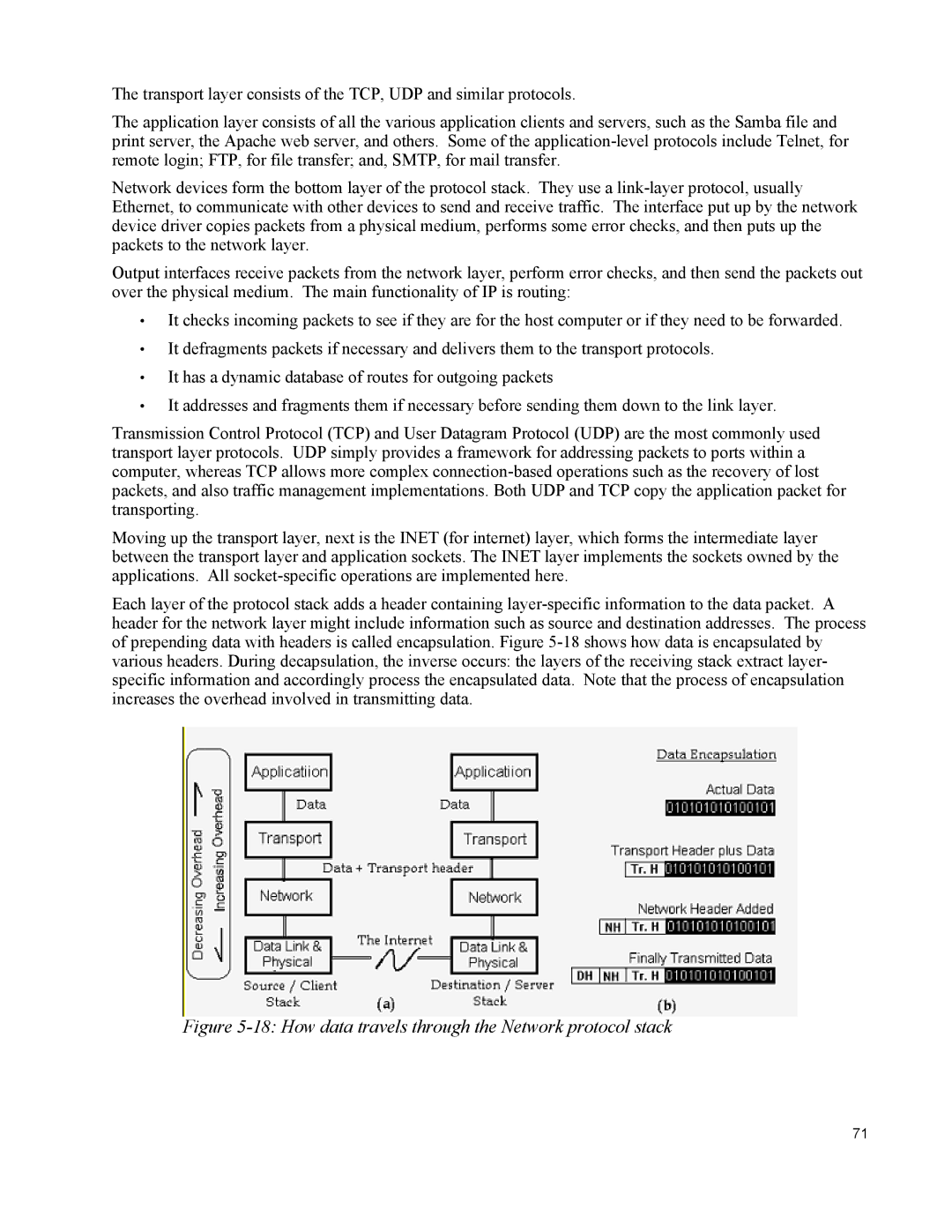
Each layer of the protocol stack adds a header containing
Figure 5-18: How data travels through the Network protocol stack
71