Source Address Functions
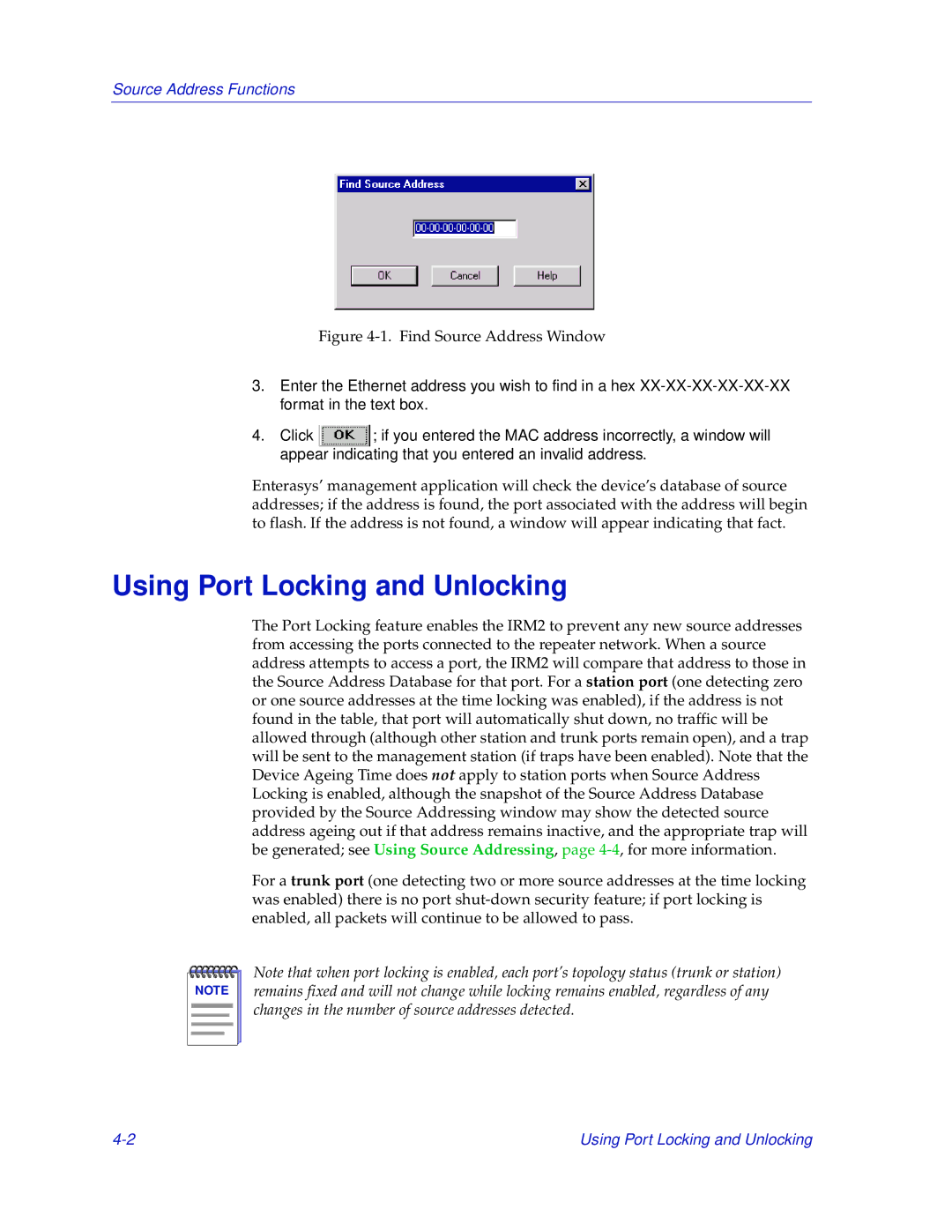
Figure 4-1. Find Source Address Window
3.Enter the Ethernet address you wish to find in a hex
4.Click ![]() ; if you entered the MAC address incorrectly, a window will appear indicating that you entered an invalid address.
; if you entered the MAC address incorrectly, a window will appear indicating that you entered an invalid address.
Enterasys’ management application will check the device’s database of source addresses; if the address is found, the port associated with the address will begin to flash. If the address is not found, a window will appear indicating that fact.
Using Port Locking and Unlocking
The Port Locking feature enables the IRM2 to prevent any new source addresses from accessing the ports connected to the repeater network. When a source address attempts to access a port, the IRM2 will compare that address to those in the Source Address Database for that port. For a station port (one detecting zero or one source addresses at the time locking was enabled), if the address is not found in the table, that port will automatically shut down, no traffic will be allowed through (although other station and trunk ports remain open), and a trap will be sent to the management station (if traps have been enabled). Note that the Device Ageing Time does not apply to station ports when Source Address Locking is enabled, although the snapshot of the Source Address Database provided by the Source Addressing window may show the detected source address ageing out if that address remains inactive, and the appropriate trap will be generated; see Using Source Addressing, page
For a trunk port (one detecting two or more source addresses at the time locking was enabled) there is no port
NOTE |
Note that when port locking is enabled, each port’s topology status (trunk or station) remains fixed and will not change while locking remains enabled, regardless of any changes in the number of source addresses detected.
Using Port Locking and Unlocking |