Manufacturing Part Number AD171-9603A June
HP bh5700 Atca 14-Slot Blade Server Ethernet Switch Blade
Ethernet Switch Blade Users Guide Release 3.2.2j
Legal Notices
About the Ethernet Switch Blade Manual
Table of Contents
Specifying Source and Destination IP Addresses
Ethernet Switch Blade Users Guide Release 3.2.2j
100
Network File System NFS Client Configuration
Network Time Protocol NTP Client Configuration
Combining Queuing Disciplines
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
Table of Figures
Fabric Switch Elements
Init Script Flow
Index of Tables
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
High Performance Embedded Switching
Overview of the Ethernet Switch Blade
Powerful CarrierClass Features
OpenArchitect Switch Management
Extensible Customization of Routing Policies
Ethernet Port Layout
Base switch Quick Reference
Ethernet Switch Blade Port Configuration
Fabric Switch Quick Reference
Inter-switch Link ISL
OpenArchitect Software Structure
OpenArchitect Switch Environment
Ethernet Switch Blade Users Guide Release 3.2.2j
OpenArchitect Software Structure
Connecting the Cables
Port Cabling and LED Indicators
Connecting to the Console Port
Console Port Cabling
LED Reference
Out of Band Ports OOB Ports
LED Reference
Ethernet Switch Blade Users Guide Release 3.2.2j
Surviving Partner
High Availability Networking
Zlmd
Switch Replacement and Reconfiguration
Example HA Switch Configuration
Modifying zsp.conf on the Base switch
Siblingaddresses zhp1 = 10.0.0.30, 10.0.0.31 netmask
#vrrpmode blockcrossconnect
Siblingaddresses zhp1=10.0.0.30master, 10.0.0.31 netmask
You will see output similar to this
Modifying zspvlan.conf on the Fabric Switch
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
# zre names cannot be mixed on the same line
ARP
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
Configuring Surviving Partner
Central Authority
Secondary
Can be modified to
Two switches, two consoles
Fabric Switch Configuration
Connecting to the Fabric Switch Console
OpenArchitect Configuration Procedure
Example Configuration Scripts
Default Configuration Scripts
Changing the Shell Prompt
Tagging and Untagging VLANs
Overview of OpenArchitect Vlan Interfaces
Address. The S50layer2 script does the following
Switch Port Interfaces
Reboot the switch
Using the S50layer2 Script
Rapid Spanning Tree
Create a bridge device from the zhp device
To Enable Rapid Spanning Tree
Port Path Cost
Layer 3 Switch Configuration
Usr/sbin/zl3d zhp0..47
Layer 3 Routing Protocols with GateD
Using the S55gatedRip1 Script
Sets the RIP1 protocol to open
Defines the netmask used in the interface
Or for RIP2
To Modify the GateD Scripts
Egress Queues
Class of Service COS
Ingress Classification
Or for Ospf
Scheduling
Marking and Re-marking
Running zfilterd
Ztmd Explained
Restrictions on Implementation
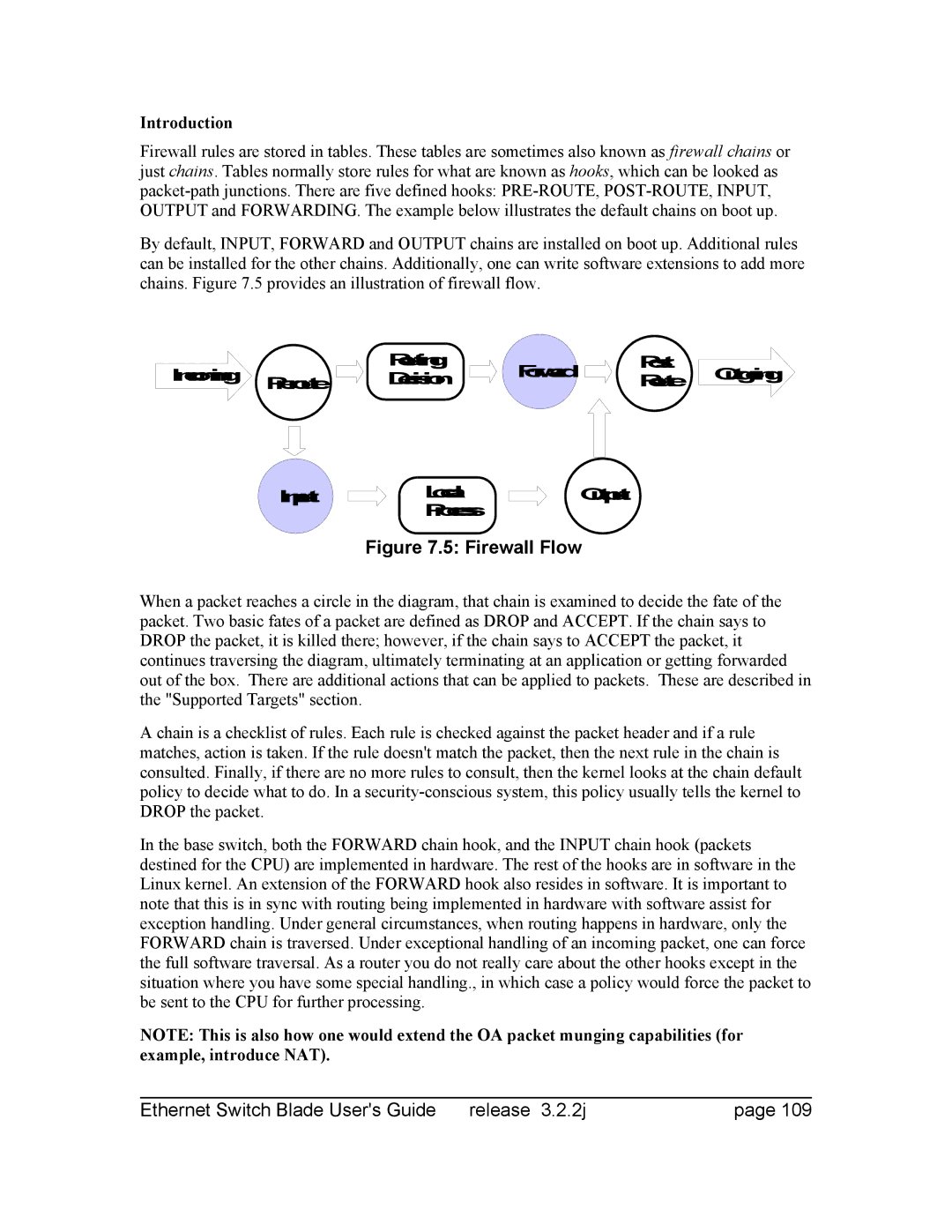
Introduction
Iptables and filtering
Packet Walk
Firewall Flow
Specifying Source and Destination IP Addresses
Filter Rules Specifications
Specifying Protocol
Specifying an Icmp Message Type
Specifying an Interface
Specifying TCP flags
Filter Rule Targets
Supported Targets
Options with any of these Zaction parameters
Extensions to the default matches
Zaction Examples
Send all tcp packets arriving on zhp5 out port
Fifo Queues pfifo and bfifo disciplines
Forwarding Chain supports all of them
Output should display the following
Root
Handle
Pfifo limit
Prio and WRR queues
Ethernet Switch Blade Users Guide Release 3.2.2j
Combining Queuing Disciplines
U32 Filter
Handle Semantics
Cops Common Open Policy Service
OpenArchitect PEP
Protocol Architecture
Sample configuration file is listed below
Using pepd
Setting the Root Password
Fabric Switch Administration
Adding Additional Users
Name Service Resolution
Setting up a Default Route
Network Time Protocol NTP Client Configuration
Network File System NFS Client Configuration
Removing the # sign
NFS Server Configuration
Connecting to the Switch Using Tftp
Connecting to the Switch Using FTP
Tftpd Server Configuration
Supported Mibs
Snmp Agent
Supported MIBs
Supported Traps
Supported Traps
Snmp and OpenArchitect Interface Definitions
OpenArchitect, defines three types of devices
Link and Snmp Status
Snmp Configuration
IfStackTable Entries
Snmp Applications
Port Mirroring
Response
You can alter this behavior by specifying
Link Event Monitoring
Link and LED Control
To check the status of a link
To check the status of all links
Overview of the OpenArchitect switch boot process
Fabric Switch Maintenance
Boot Flow Chart
Recovering from a System Failure
Modifying Files and Updating the Switch
System Boots with a Console Cable
Saving Changes
Booting with the -ioption
Booting the Duplicate Flash Image
System Hangs During Boot
Reboot the system
Upgrading the OpenArchitect Image
Upgrading or Adding Files
Upgrading the Switch Driver
Excluding Saving Files to Flash
Image file will be something named similar to the following
Using apt-get
Connecting to the Base Switch Console
Base Switch Configuration
OpenArchitect Configuration Procedure
Example Configuration Scripts
Default Configuration Scripts
Changing the Shell Prompt
Files into flash for reloading
Overview of OpenArchitect Vlan Interfaces
Multiple VLANs
Linux
Then, bring up the interface with ifconfig1M
Rapid Spanning Tree
Layer 3 Switch Configuration
Zconfig zhp1 vlan2=zre5..8 zconfig zre5..8=untag2
Layer 3 Switch
Using the S50multivlan Script
Layer 3 Switch Using Multiple VLANs
Multiple Vlan Configuration
10.0.0.42-10.0.3.42, assigns the netmask and brings them up
Layer 3 Routing Protocols with GateD
Shuts off sending and receiving packets from all interfaces
To Modify the GateD Scripts
Egress Queues
Class of Service COS
Ingress Classification
Marking and Re-marking
Zcos
Scheduling
Restrictions on Implementation
Running zfilterd
Output Port
Field values
Action that will take place. For example, the rules
Iptables and filtering
Firewall Flow
Specifying Source and Destination IP Addresses
Icmp-type ping
Zaction
Strict Priority Qdisc
Tc Traffic Control
These are described in the Linux packet filtering Howto at
Znyx Forwarding Chain supports all of them
Weighted Round Robin Qdisc
Fifo Qdiscs
Using Filters to Direct Packets to a COS Queue
Protocol ip
Protocol all
Protocol arp
Matching Specific Ingress Ports
Advanced Filtering Policing
Examples
Policing Actions
Spanning tree Bpdu packets go in COS queue 6, no limit
82+
U32 match selectors used in filters
To mirror only in-profile packets to port 3, use
U Match Selectors
Match selectors
Ztmd zqosd
Ethernet Switch Blade Users Guide Release 3.2.2j
U32 Filter
Cops Common Open Policy Service
Protocol Architecture
OpenArchitect PEP
Using pepd
Pepid
Where
Setting the Root Password
Base Switch Administration
Adding Additional Users
Name Service Resolution
Setting up a Default Route
Network File System NFS Client Configuration
Connecting to the Switch Using FTP
NFS Server Configuration
Tftpd Server Configuration
Connecting to the Switch Using Tftp
Snmp Agent
Supported Mibs
Snmp and OpenArchitect Interface Definitions
Snmp Configuration
Physical Link Status on Base Switch
Snmp Applications
Port Mirroring
Link Event Monitoring
Link and LED Control
Overview of the OpenArchitect switch boot process
Base Switch Maintenance
Booting up Process Flow
Recovering from a System Failure
Modifying Files and Updating the Switch
System Boots with a Console Cable
Saving Changes
∙ Reboot the system
Booting with the -i option
Booting the Duplicate Flash Image
System Hangs During Boot
Upgrading the OpenArchitect Image
Upgrading or Adding Files
Upgrading the Switch Driver
Using apt-get
Ethernet Interfaces
Base Interface Hub System
Management Interfaces
Console port. An RS-232 to RJ-45 adapter is required
Fabric Interface Hub System
Base Interface Out-of-Band Ethernet Connection
Fabric Interface Serial Ports
Fabric Interface Out of Band Ethernet Connection
Ethernet Switch Blade Activation States
Diagnosing a Failed Ethernet Switch Blade Activation
FRU State HotSwap Healthy Solution LED Status
Verifying Communications Between the ShMM and Switch
Accessing the ShMM
FRU State HotSwap Healthy Solution
Troubleshooting States
Checking the ekey Status From the Shelf Manager
Analyzing Mstate information for the switch
Clia board -v
Troubleshooting a Failed OpenArchitect Load
OpenArchitect Boot Process
Recovering from a System Failure
Properly attach the console cable
Booting Without the Overlay File
Booting the Duplicate Flash Image
Ethernet Switch Blade Backplane Interfaces zre Ports
Network Configuration Problems
Interface Overview
Physical Interfaces
Port, Layer 2 Switching, single Vlan
Default Base Interface Configuration
Additional Interfaces
Default Base Interface Network Diagram
Default Fabric Interface Configuration
Linux Networking Environment Interfaces
Ifconfig Default Screen Output for the Base Interface
Problem Solution
Configuration Troubleshooting
Determining ekey status for a specific slot
Auto Enable Internal Fault
Link Port Status Link Speed Pause Faults
1000fd Disable External Fault
Zre
Link Status for a single port
Querying Base Interface ekey Status
Example Output
Link Status for a range of ports
Querying Fabric Interface ekey Status
Ethernet Switch Blade Users Guide Release 3.2.2j
Connecting to Devices with Fixed Port Speeds
Network Connectivity Troubleshooting No Connection
External Fault LED
Diminished Network Throughput
Network Tests
Ping Test
Traceroute Test
Isolating Hardware Failures
Switch Chip U59
Isolation Transformer Zone 3 Atca Connector Switch Chip U60
Isolation Transformer
ZMC Daughter Board Inside View
Hardware Subsystem
Testing the FlashROMs
Link Status for a single port
Testing the Switch Fabric
Link Status for a range of ports
Testing the onboard RAM
Testing the Control Processor
INT FLT LED activity
Hardware Fault
Ethernet Switch Blade Users Guide Release 3.2.2j
Spontaneous Failover Activity
High Availability Troubleshooting
Unexpected Fail-back Activity
Checking the switch firmware version
Switch Firmware Overview
Following output is shown for the 3.0 Base Interface
Base Interface
Fabric Interface
BootLoader Firmware Upgrade
Updating the Switch Firmware
OpenArchitect Firmware Upgrade
Ipmc Firmware Upgrade
Restoring the Factory Default Configuration
Before Calling Support
ROM Devices in OpenArchitect
Appendix a Fabric Switch Command Man Pages
Vrrpconfig Configure and control the running vrrpd
Vrrpconfig
See Also
Vrrpd Virtual Router Redundancy Protocol Daemon
Vrrpd
Change the virtual MAC address from
Vrrpconfig
Zbootcfg
Zbootcfg -d 1
Zconfig Configures the OpenArchitect switch
Zconfig
Global Statement Syntax
Global Statements
Trunk Interface Statements
Trunk interface syntax
Examples of trunk interface statements
Zrl0=ip sourceaddress, ip destinationaddress Is the same as
This statement creates a trunk containing three ports
Teardown statement uses a colon instead of an equals sign
Examples of Network Interface Statements
Network interface actions may include
Examples of Port Interface Statements
Port Interface Statements
This statement is equivalent to the following three lines
Wildcards
This is equivalent to
Zl3d
Zcos
Zcos class of service queue control
Hostname
Prio RR WRR DRR port list
Zcos -n 50,50,50,50,75,75,75,75 zre0..19
Zdog
Options
Zfilterd
Zflash
Zbootcfg
Zl2, zl2mc, zl3host, zl3net, zvlan
Zl2 -m 00c095450000
Following command displays all entries of the zl2 table
Following command deletes the above entry
Zgvrpd
Zgvrpd -t zhp0
Zl2d
Zl2d Layer 2 daemon for the OpenArchitect switch
Start stop
Operations
Zl3d
Zl3d Layer 3 daemon for the OpenArchitect switch
Zl3d zhp1 zhp2 zhp3
Zlc − link and LED control
Zlc
To query the settings of a particular port
Ifconfig8
Zlmd − monitor link changes or hot swap events
Zlmd
Zlmd zre1..4=/usr/sbin/prtchange
Zlogrotate
To start zlogrotate with the default values
Zlogrotate − Rotates log files
Zmirror Set packet mirroring on an ingress or egress port
Zmirror
Zmirror is cumulative
Zmnt − Expands the read/write files onto the RAM disk
Zmnt
Restored overlay will be used upon the next reboot
Zpeer
On the fabric switch the following command would return
Peer is not properly functioning
Set debug level to level Display complete status of zpeer
Healthy state, the query will return the backup state
Be also reset
Zqosd
Ztmd, tc8, zfilterd
Zrc Packet rate control
Zrc
Zreg
Operands
Zrld Znyx redirector daemon
Zrld
Zsnoopd
Zsnoopd
Zspconfig configure and start surviving partner
Zspconfig
Configuration File
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
Rain link zhp1, zre1..4
Output Files
Zconfig, ifconfig, vrrpd, dhclient, dhcpd
Zstack
Zstack Configures the OpenArchitect switch stacking
Stack Port Association
Stack Creation
Stack Control Statements
Stack Configuration Statements
Are supported
Zre lists. Example of stack0..3 representing stacks 0, 1, 2
Switch Blade
Ztats − Display statistics and information about switch
Ztats
Zsync − Saves changes to the flash
Zsync
To zsync only the hosts file
Restored overlay will be loaded upon the next reboot
Ztmd
Zqosd, iptables8, tc8, zfilterd
Brctl8
Brctl Bridge and Spanning Tree Protocol administration
Brctl8 replaces the older brcfg tool
Setportprio bridge zre# priority
Zconfig, zl2d
Appendix B Base Switch Command Man Pages
= Master
Examples
Following options are supported by vrrpd
Lower Case ‘m’ the time is specified in milliseconds.
See Also
Specifies the ROM device from which to boot. The dev
Zbootcfg -d
ZhpN for example, zhp0
Trunk interface actions
Examples of trunk interface statements
Network interface actions may include
Zhp0 vlan100 = zre1,zre10,zre11,zre13
Tag are given the Vlan tag with the VID number 1, enter
This is equivalent to
See Also
Zcos
Limit on dynamic pool usage, in bytes, reset % port list
Prio RR WRR DRR port list
Examples
Zdog
Options
Zffpcounter
First example queries all FFP counter values
Now using zffpcounter to display
Next example clears all FFP counter values
Next example queries ports 2-7, 15,
Counter 19 Counter 20 Counter 21
Zfilterd -d level -p port -f -l -i pid -o pid
Zflash
Zbootcfg
Std 802.1D, 1998 Edition
Zgmrpd
Zgmrpd -t zhp0
Zgr
Following command displays all entries of the zl2 table
See Also
Level Sets the level of debugging output required by zgvrpd.
Enable Gvrp on the set
Start stop
Operations
Zl3d -h hostname -t msecs -b -e -l -n -d level iface
Zl3d zhp1 zhp2 zhp3
Zlc
Global Settings
Zlmd
Examples
Zlogrotate
Zmirror
Zmirror zre1 zre10 zmirror zre2 zre11
See Also
Expanded, or the file to which the tar image is saved
Restored overlay will be used upon the next reboot
Zpeer
Options
See Also
Zqosd
Ztmd, tc8, zfilterd
Number of packets per time period above which
Zreg
Echo 0x80000640 zreg -w
Zrld
Zsnoopd
No router multicast traffic. Default is 260 seconds
Zpeer peer state query
Time to wait in seconds before giving up on
Configuration File
Ethernet Switch Blade Users Guide Release 3.2.2j
Ethernet Switch Blade Users Guide Release 3.2.2j
RAINlink zhp1, zre1..4
Boardsynchronizationmode basic
Zconfig, ifconfig, vrrpd, dhclient, dhcpd, zpeer
Ethernet Switch Blade Users Guide Release 3.2.2j
Specifies the remote hostname to configure. By
Stack0 ppa0 local Stack1 ppa1 local
Stack Configuration Statements
Wildcards
See Also
Zsync
Files
Ztmd
Zqosd, iptables8, tc8, zfilterd
Important This option must only be executed by zl2d
Ethernet Switch Blade Users Guide Release 3.2.2j
Zconfig, zl2d
Appendix C Intelligent Platform Management Interface
ISwitch-ShMC Interaction
States
Peripheral Management Controller Functional Support
PMC Controller Support Command Code Sensor # Status
Table C.1. Ipmi M States
Table C.2 PMC Controller Support
Sensor Reading Example
Standard Ipmi Command GetSensorReading
Table C.3 GetSensorReading
Table C.4 GetSensorResonse
Standard Ipmi Response GetSensorReading
Structure of Standard Ipmi Responses From PMC to BMC
Structure of Standard Ipmi Commands From BMC to PMC
Field Replaceable Unit Inventory Device
Event Generator
Ipmb Event message format
Table C.8 Seeprom Space
Spare Seeprom Space Allocation
Ipmb Override Status Data
Table C.9. Ipmb Override Status Data
Dhcp
Index
NFS NTP
Tc 62
Ztmd 301 Zvlan 179 ZX4920.MIB 333