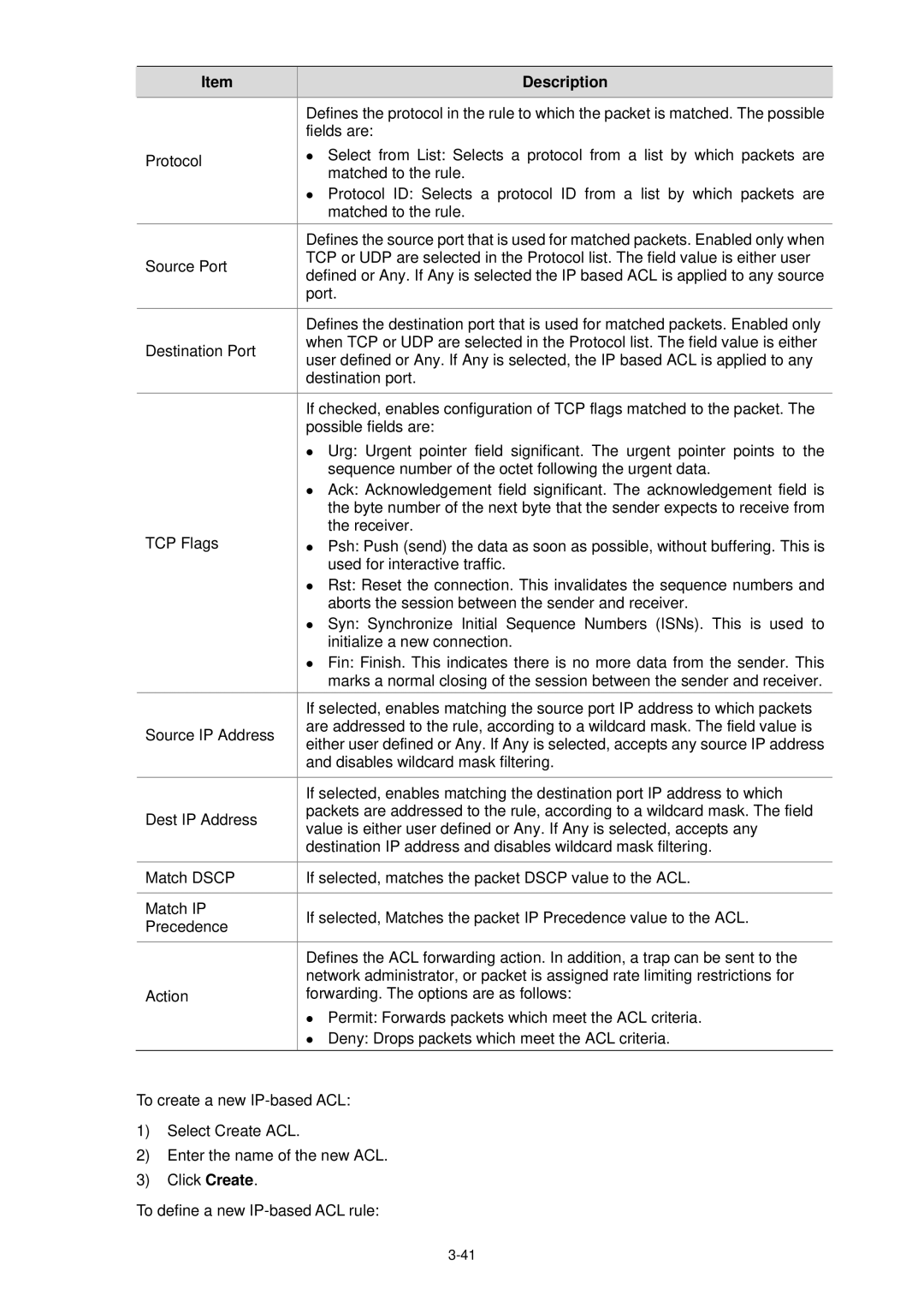
| Item |
|
| Description |
|
|
| Defines the protocol in the rule to which the packet is matched. The possible | |
|
|
| fields are: | |
| Protocol |
| z Select from List: Selects a protocol from a list by which packets are | |
|
|
| matched to the rule. | |
|
|
|
| |
|
|
| z | Protocol ID: Selects a protocol ID from a list by which packets are |
|
|
|
| matched to the rule. |
|
|
| Defines the source port that is used for matched packets. Enabled only when | |
| Source Port |
| TCP or UDP are selected in the Protocol list. The field value is either user | |
|
| defined or Any. If Any is selected the IP based ACL is applied to any source | ||
|
|
| ||
|
|
| port. | |
|
|
|
| |
|
|
| Defines the destination port that is used for matched packets. Enabled only | |
| Destination Port |
| when TCP or UDP are selected in the Protocol list. The field value is either | |
|
| user defined or Any. If Any is selected, the IP based ACL is applied to any | ||
|
|
| ||
|
|
| destination port. | |
|
|
|
| |
|
|
| If checked, enables configuration of TCP flags matched to the packet. The | |
|
|
| possible fields are: | |
|
|
| z | Urg: Urgent pointer field significant. The urgent pointer points to the |
|
|
|
| sequence number of the octet following the urgent data. |
|
|
| z Ack: Acknowledgement field significant. The acknowledgement field is | |
|
|
|
| the byte number of the next byte that the sender expects to receive from |
| TCP Flags |
|
| the receiver. |
|
| z | Psh: Push (send) the data as soon as possible, without buffering. This is | |
|
|
|
| used for interactive traffic. |
|
|
| z Rst: Reset the connection. This invalidates the sequence numbers and | |
|
|
|
| aborts the session between the sender and receiver. |
|
|
| z | Syn: Synchronize Initial Sequence Numbers (ISNs). This is used to |
|
|
|
| initialize a new connection. |
|
|
| z Fin: Finish. This indicates there is no more data from the sender. This | |
|
|
|
| marks a normal closing of the session between the sender and receiver. |
|
|
| If selected, enables matching the source port IP address to which packets | |
| Source IP Address |
| are addressed to the rule, according to a wildcard mask. The field value is | |
|
| either user defined or Any. If Any is selected, accepts any source IP address | ||
|
|
| ||
|
|
| and disables wildcard mask filtering. | |
|
|
|
| |
|
|
| If selected, enables matching the destination port IP address to which | |
| Dest IP Address |
| packets are addressed to the rule, according to a wildcard mask. The field | |
|
| value is either user defined or Any. If Any is selected, accepts any | ||
|
|
| ||
|
|
| destination IP address and disables wildcard mask filtering. | |
|
|
| ||
| Match DSCP | If selected, matches the packet DSCP value to the ACL. | ||
|
|
|
|
|
| Match IP |
| If selected, Matches the packet IP Precedence value to the ACL. | |
| Precedence |
| ||
|
|
|
| |
|
|
|
| |
|
|
| Defines the ACL forwarding action. In addition, a trap can be sent to the | |
|
|
| network administrator, or packet is assigned rate limiting restrictions for | |
| Action |
| forwarding. The options are as follows: | |
|
|
| z Permit: Forwards packets which meet the ACL criteria. | |
|
|
| z Deny: Drops packets which meet the ACL criteria. | |
To create a new
1)Select Create ACL.
2)Enter the name of the new ACL.
3)Click Create.
To define a new