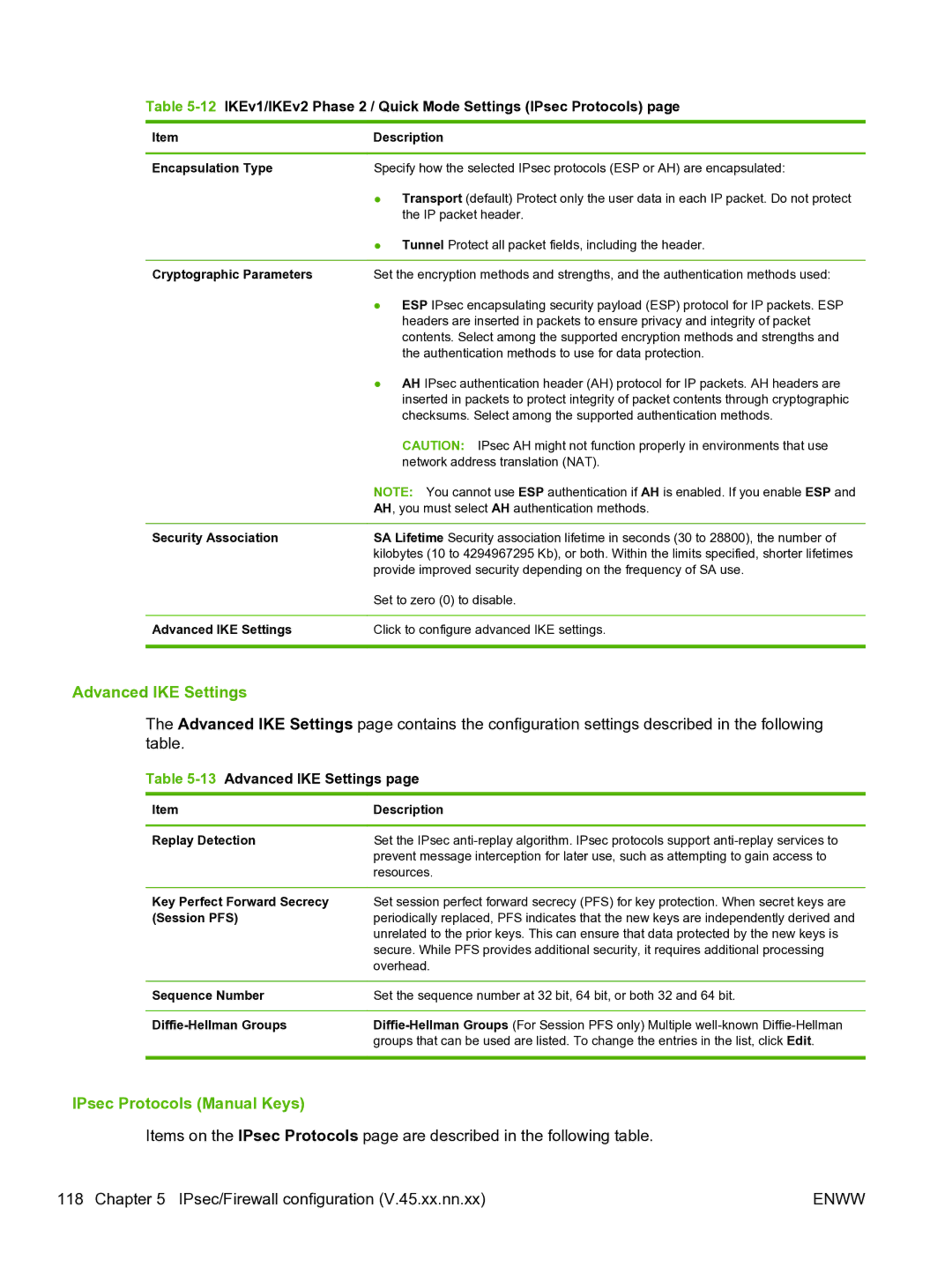
Table 5-12 IKEv1/IKEv2 Phase 2 / Quick Mode Settings (IPsec Protocols) page
Item | Description | |
|
| |
Encapsulation Type | Specify how the selected IPsec protocols (ESP or AH) are encapsulated: | |
| ● | Transport (default) Protect only the user data in each IP packet. Do not protect |
|
| the IP packet header. |
| ● | Tunnel Protect all packet fields, including the header. |
|
| |
Cryptographic Parameters | Set the encryption methods and strengths, and the authentication methods used: | |
| ● | ESP IPsec encapsulating security payload (ESP) protocol for IP packets. ESP |
|
| headers are inserted in packets to ensure privacy and integrity of packet |
|
| contents. Select among the supported encryption methods and strengths and |
|
| the authentication methods to use for data protection. |
| ● | AH IPsec authentication header (AH) protocol for IP packets. AH headers are |
|
| inserted in packets to protect integrity of packet contents through cryptographic |
|
| checksums. Select among the supported authentication methods. |
|
| CAUTION: IPsec AH might not function properly in environments that use |
|
| network address translation (NAT). |
| NOTE: You cannot use ESP authentication if AH is enabled. If you enable ESP and | |
| AH, you must select AH authentication methods. | |
|
| |
Security Association | SA Lifetime Security association lifetime in seconds (30 to 28800), the number of | |
| kilobytes (10 to 4294967295 Kb), or both. Within the limits specified, shorter lifetimes | |
| provide improved security depending on the frequency of SA use. | |
| Set to zero (0) to disable. | |
|
| |
Advanced IKE Settings | Click to configure advanced IKE settings. | |
|
|
|
Advanced IKE Settings
The Advanced IKE Settings page contains the configuration settings described in the following table.
Table 5-13 Advanced IKE Settings page
Item | Description |
|
|
Replay Detection | Set the IPsec |
| prevent message interception for later use, such as attempting to gain access to |
| resources. |
|
|
Key Perfect Forward Secrecy | Set session perfect forward secrecy (PFS) for key protection. When secret keys are |
(Session PFS) | periodically replaced, PFS indicates that the new keys are independently derived and |
| unrelated to the prior keys. This can ensure that data protected by the new keys is |
| secure. While PFS provides additional security, it requires additional processing |
| overhead. |
|
|
Sequence Number | Set the sequence number at 32 bit, 64 bit, or both 32 and 64 bit. |
|
|
| |
| groups that can be used are listed. To change the entries in the list, click Edit. |
|
|
IPsec Protocols (Manual Keys)
Items on the IPsec Protocols page are described in the following table.
118 Chapter 5 IPsec/Firewall configuration (V.45.xx.nn.xx) | ENWW |