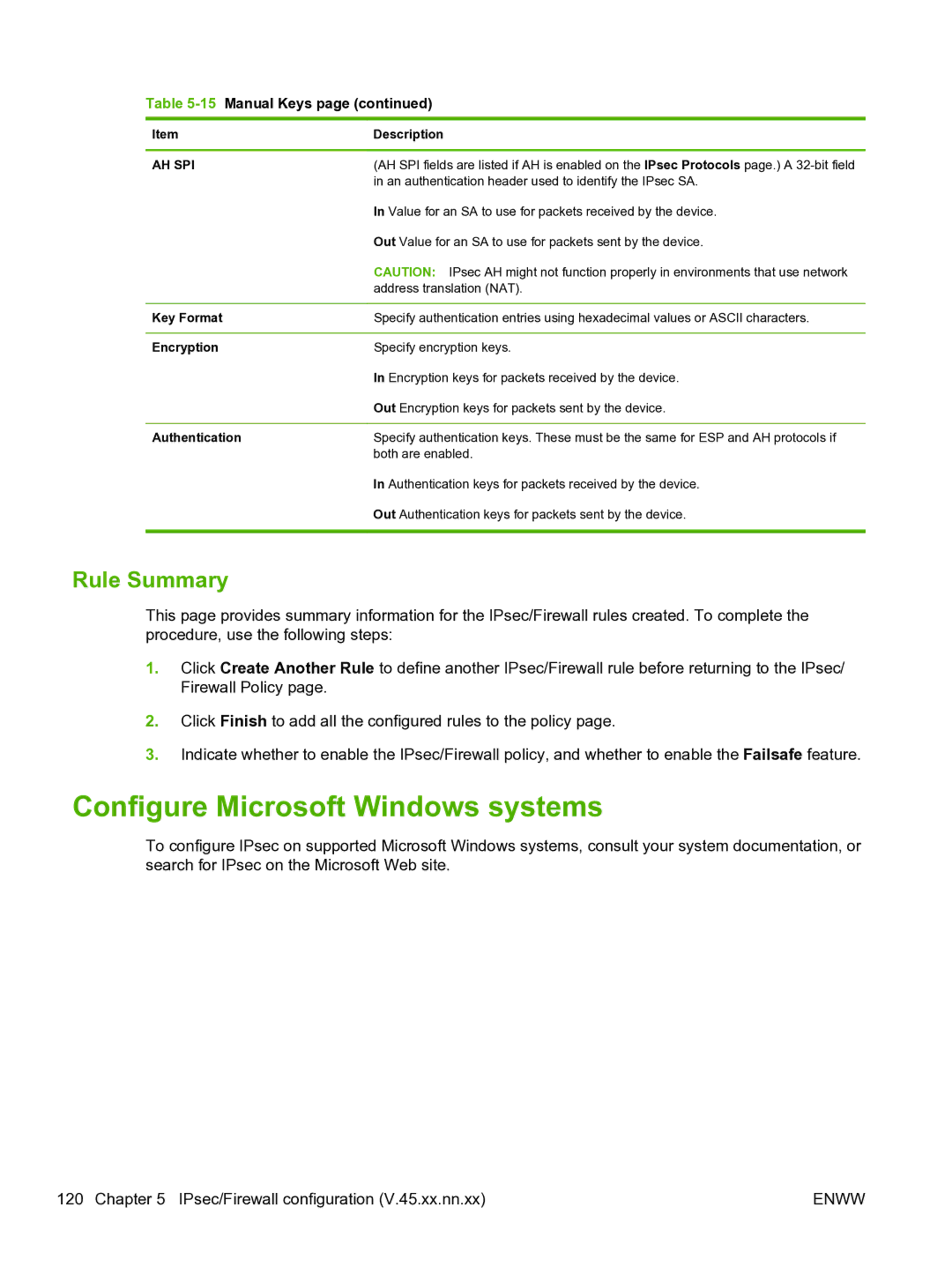
Table 5-15 Manual Keys page (continued)
Item | Description |
|
|
AH SPI | (AH SPI fields are listed if AH is enabled on the IPsec Protocols page.) A |
| in an authentication header used to identify the IPsec SA. |
| In Value for an SA to use for packets received by the device. |
| Out Value for an SA to use for packets sent by the device. |
| CAUTION: IPsec AH might not function properly in environments that use network |
| address translation (NAT). |
|
|
Key Format | Specify authentication entries using hexadecimal values or ASCII characters. |
|
|
Encryption | Specify encryption keys. |
| In Encryption keys for packets received by the device. |
| Out Encryption keys for packets sent by the device. |
|
|
Authentication | Specify authentication keys. These must be the same for ESP and AH protocols if |
| both are enabled. |
| In Authentication keys for packets received by the device. |
| Out Authentication keys for packets sent by the device. |
|
|
Rule Summary
This page provides summary information for the IPsec/Firewall rules created. To complete the procedure, use the following steps:
1.Click Create Another Rule to define another IPsec/Firewall rule before returning to the IPsec/ Firewall Policy page.
2.Click Finish to add all the configured rules to the policy page.
3.Indicate whether to enable the IPsec/Firewall policy, and whether to enable the Failsafe feature.
Configure Microsoft Windows systems
To configure IPsec on supported Microsoft Windows systems, consult your system documentation, or search for IPsec on the Microsoft Web site.
120 Chapter 5 IPsec/Firewall configuration (V.45.xx.nn.xx) | ENWW |