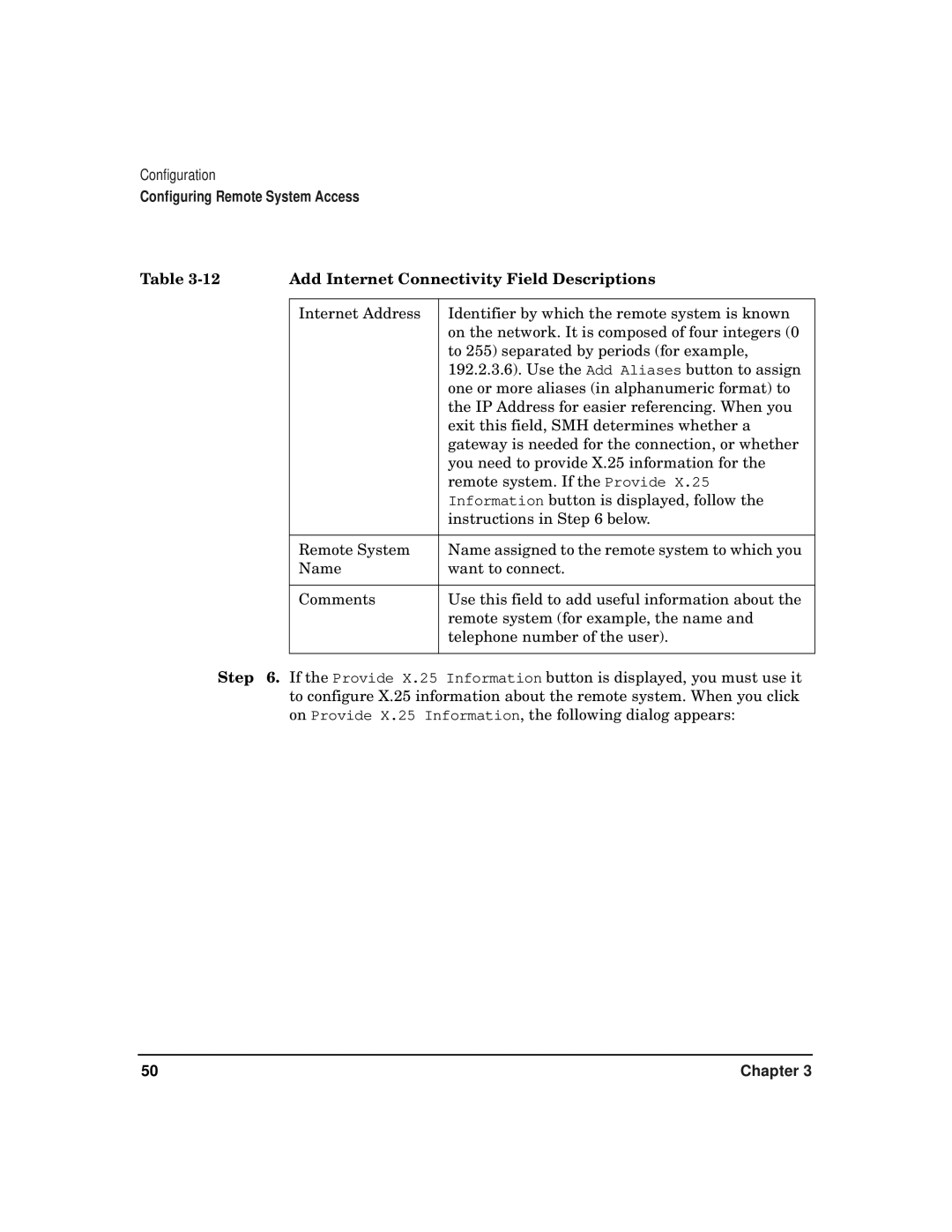
CommonIO Products specifications
HP CommonIO products, designed to enhance connectivity and interoperability across various platforms, are a significant innovation in the realm of information technology. They serve as a foundational layer in HP's offerings, bridging the gap between hardware components, software applications, and the overarching IT infrastructure.One of the most prominent features of HP CommonIO products is their robust compatibility with a wide range of devices. This versatility allows businesses to integrate different hardware systems effortlessly, facilitating seamless communication and data exchange. The products are built with an open architecture, ensuring that they can accommodate both legacy systems and the latest technological advancements.
Another key characteristic of HP CommonIO products is their high-performance data handling capabilities. Equipped with advanced data processing technologies, these products can manage large volumes of data efficiently, ensuring minimal latency and maximum throughput. This is particularly beneficial for critical applications that require real-time processing and rapid responses.
Security is a top priority in today’s digital landscape, and HP CommonIO products come with built-in security features. They support advanced encryption protocols and secure access controls, providing a secure framework for data transmission and safeguarding sensitive information. This level of security is essential for organizations that need to comply with stringent regulatory standards.
Additionally, HP CommonIO products are characterized by their user-friendly interfaces and management tools. Administrators can easily configure and monitor the systems, gaining insights into performance metrics and potential issues. This intuitive management simplifies operations and reduces the administrative overhead associated with IT maintenance.
The products also leverage cutting-edge technologies such as virtualization and cloud adaptations, allowing organizations to scale their resources according to demand. This flexibility is crucial for businesses aiming to optimize costs while meeting varying workloads effectively.
In summary, HP CommonIO products are designed to deliver enhanced connectivity, robust performance, and security, making them essential tools for modern IT environments. Their compatibility with diverse systems, high throughput capabilities, secure frameworks, and user-friendly management tools collectively contribute to their effectiveness in supporting organizations’ operational goals. As businesses continue to evolve, HP CommonIO products remain at the forefront, enabling efficient and secure IT infrastructures.