Chapter 1
IPSec: Concept for secure IP connections
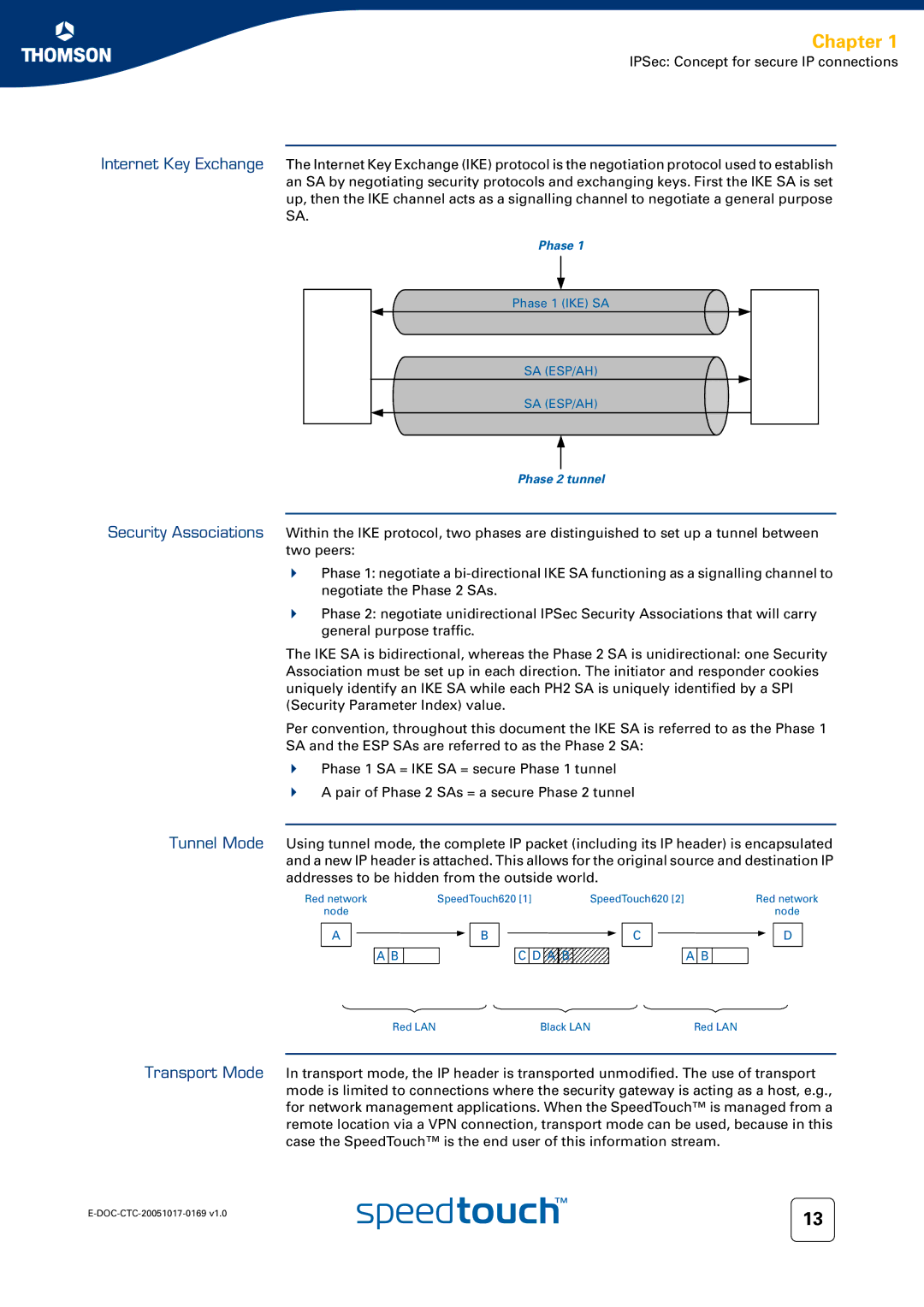
Internet Key Exchange The Internet Key Exchange (IKE) protocol is the negotiation protocol used to establish an SA by negotiating security protocols and exchanging keys. First the IKE SA is set up, then the IKE channel acts as a signalling channel to negotiate a general purpose SA.
Phase 1
Phase 1 (IKE) SA |
SA (ESP/AH) |
SA (ESP/AH) |
Security Associations
Tunnel Mode
Phase 2 tunnel
Within the IKE protocol, two phases are distinguished to set up a tunnel between two peers:
Phase 1: negotiate a
Phase 2: negotiate unidirectional IPSec Security Associations that will carry general purpose traffic.
The IKE SA is bidirectional, whereas the Phase 2 SA is unidirectional: one Security Association must be set up in each direction. The initiator and responder cookies uniquely identify an IKE SA while each PH2 SA is uniquely identified by a SPI (Security Parameter Index) value.
Per convention, throughout this document the IKE SA is referred to as the Phase 1 SA and the ESP SAs are referred to as the Phase 2 SA:
Phase 1 SA = IKE SA = secure Phase 1 tunnel
A pair of Phase 2 SAs = a secure Phase 2 tunnel
Using tunnel mode, the complete IP packet (including its IP header) is encapsulated and a new IP header is attached. This allows for the original source and destination IP addresses to be hidden from the outside world.
Red network | SpeedTouch620 [1] | SpeedTouch620 [2] | Red network | ||||||
| node |
|
|
|
|
|
| node | |
|
|
|
|
|
|
|
|
|
|
| A |
|
| B |
|
| C |
| D |
|
|
|
|
|
|
|
|
|
|
A B | C D A B | A B |
Red LAN | Black LAN | Red LAN |
Transport Mode In transport mode, the IP header is transported unmodified. The use of transport mode is limited to connections where the security gateway is acting as a host, e.g., for network management applications. When the SpeedTouch™ is managed from a remote location via a VPN connection, transport mode can be used, because in this case the SpeedTouch™ is the end user of this information stream.
13 | |
|