Chapter 4
Configuration via the Command Line Interface
4 Configuration via the Command Line Interface
In this chapter This chapter describes the basic configuration steps for building an operational IPSec via the Command Line Interface. Firstly, a reference network is proposed, that serves in examples throughout the chapter. Then an outline of the configuration procedure is presented. The individual steps are described in detail in the subsequent sections.
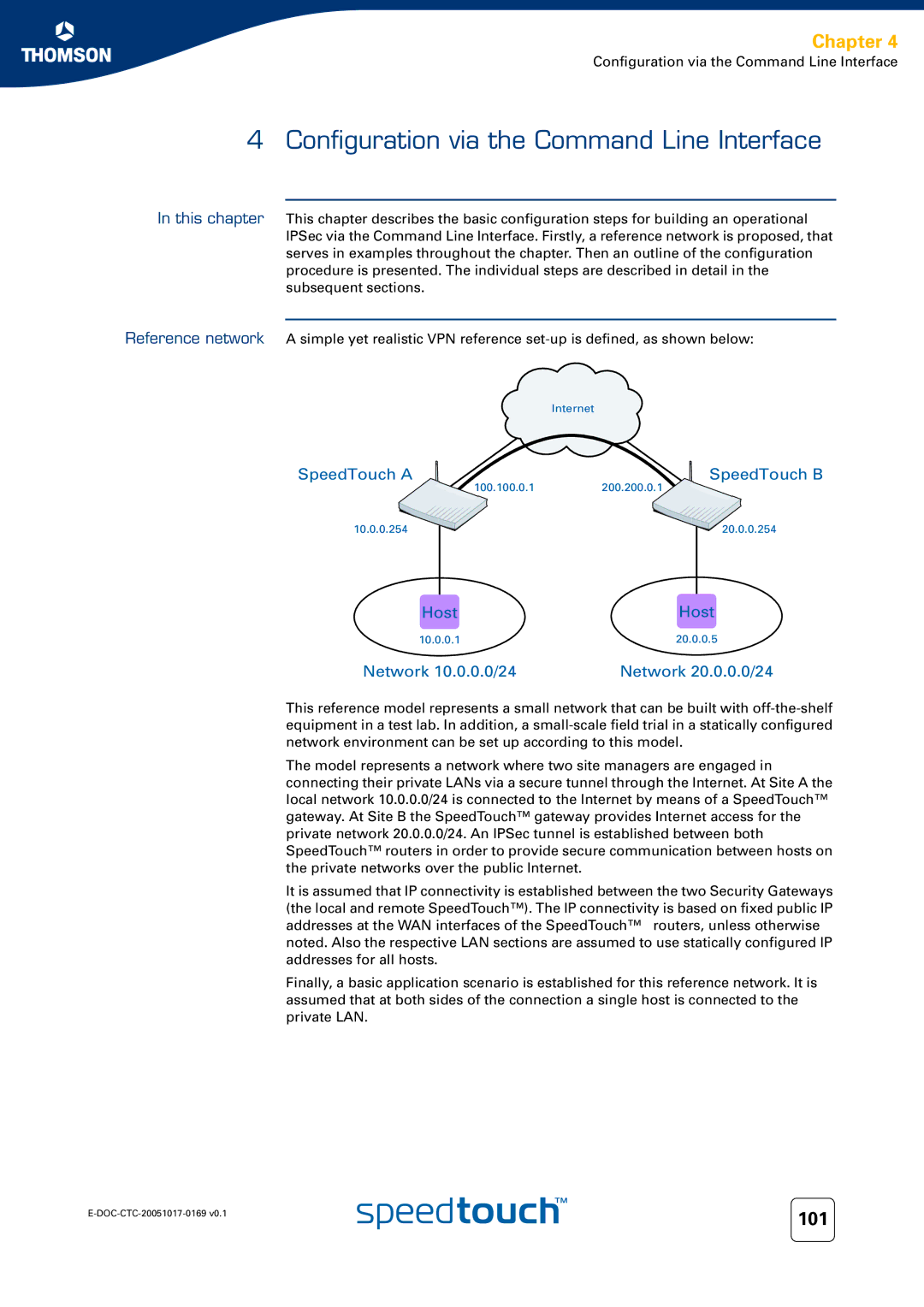
Reference network A simple yet realistic VPN reference
Internet
SpeedTouch A
100.100.0.1200.200.0.1
10.0.0.254
SpeedTouch B
20.0.0.254
Host | Host |
10.0.0.1 | 20.0.0.5 |
Network 10.0.0.0/24 | Network 20.0.0.0/24 |
This reference model represents a small network that can be built with
The model represents a network where two site managers are engaged in connecting their private LANs via a secure tunnel through the Internet. At Site A the local network 10.0.0.0/24 is connected to the Internet by means of a SpeedTouch™ gateway. At Site B the SpeedTouch™ gateway provides Internet access for the private network 20.0.0.0/24. An IPSec tunnel is established between both SpeedTouch™ routers in order to provide secure communication between hosts on the private networks over the public Internet.
It is assumed that IP connectivity is established between the two Security Gateways (the local and remote SpeedTouch™). The IP connectivity is based on fixed public IP addresses at the WAN interfaces of the SpeedTouch™ routers, unless otherwise noted. Also the respective LAN sections are assumed to use statically configured IP addresses for all hosts.
Finally, a basic application scenario is established for this reference network. It is assumed that at both sides of the connection a single host is connected to the private LAN.
101 | |
|