Chapter 6
Advanced Features
6.3 Extended Authentication (XAuth)
What is ... Extended Authentication, commonly referred to as the XAuth protocol, allows for performing extra user authentication. A typical practical example is the mixed use of IKE tunnel negotiation using preshared key as authentication method and on top of that doing Extended Authentication.
The VPN client functionality built in the SpeedTouch™ supports the (optional) use of XAuth. It acts as a XAuth client. In order to use this functionality, it needs to be connected to a remote IPSec gateway capable of handling the XAuth protocol.
The VPN server functionality built in the SpeedTouch™ also supports the use of
XAuth as an XAuth server. It uses an internal list of authorized users.
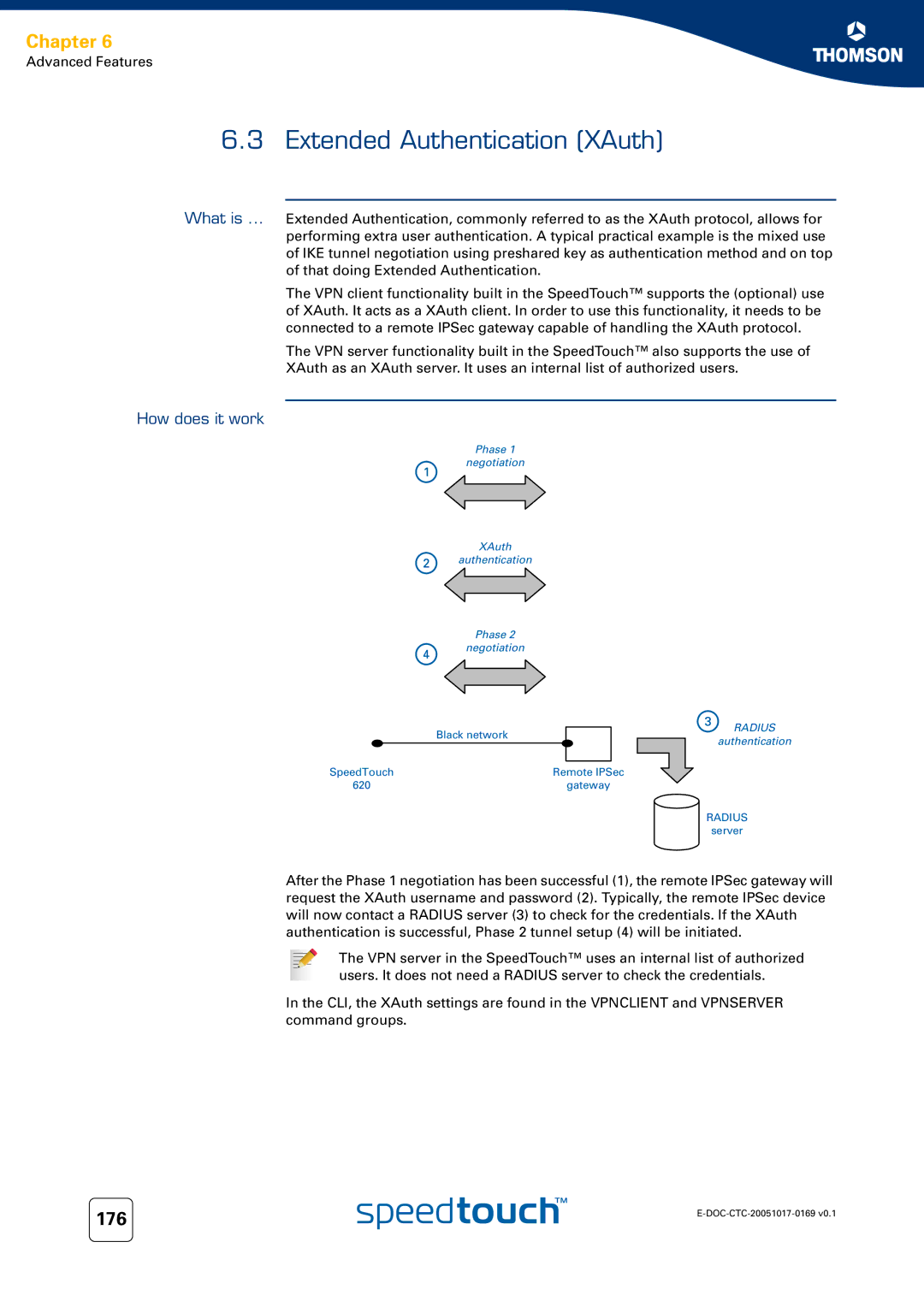
How does it work
Phase 1
negotiation
XAuth
authentication
Phase 2
negotiation
| Black network | RADIUS |
| authentication | |
|
| |
SpeedTouch |
| Remote IPSec |
620 |
| gateway |
|
| RADIUS |
|
| server |
After the Phase 1 negotiation has been successful (1), the remote IPSec gateway will request the XAuth username and password (2). Typically, the remote IPSec device will now contact a RADIUS server (3) to check for the credentials. If the XAuth authentication is successful, Phase 2 tunnel setup (4) will be initiated.
The VPN server in the SpeedTouch™ uses an internal list of authorized users. It does not need a RADIUS server to check the credentials.
In the CLI, the XAuth settings are found in the VPNCLIENT and VPNSERVER command groups.
176 | |
|