Iolan SDS/SCS/STS/MDC
EN 55022 1998, Class A, Note
Table of Contents
Getting to Know Your Iolan
Power Supply Specifications
WebManager
Powering Up the Iolan
Introduction Configuration Methods Overview
Easy Config Wizard DeviceManager
Menu
Command Line Interface
IOLAN+ Interface
Configuration Files
Setting Up the Serial Ports Setting Up Users
Using DeviceManager to Connect to the Iolan
Using WebManager to Connect to the Iolan
Managing the Iolan
Introduction IP Settings
Advanced
Serial Port Profiles 116
Introduction 113 Serial Ports
UDP Sockets Profile 142
Port Buffering
Control Signal I/O Profile 169
Advanced 197
Introduction 201 User Settings 202
Adding/Editing Users 203
223
Introduction 213 Authentication
226
Keys and Certificates 242
Services 240
Introduction 245 Settings 246
231
Modbus Slave
Channels
Snmp Traps 289
Modbus I/O Access 278
Accessing I/O Data Via TruePort 285
TruePort I/O 283
Management 302
Introduction 295 Option Card Settings
296
Introduction 299 Alerts
Channels 316
Serial Port Power Control 315
Introduction 319 Managing Configuration Files
Introduction 313 RPS Control
329
323
326
327
Introduction 347
Configuring Modbus 333
Configuring PPP Dial On Demand 337 Setting Up Printers 338
Configuring a Virtual Private Network 340
Serial Pinouts 363
EIA-232 Cabling Diagrams 371
Introduction 359 Valid SSL/TLS Ciphers
361
Introduction 391 TruePort
Wiring I/O Diagrams 385
Decoder 393
API I/O Access Over TruePort 392
Communication Issues 410
Host Problems 411
415
Models 415 IPv6 Issues 416 Contacting Technical Support 417
Index
Documentation
Preface
About This Book
Intended Audience
Online Help
Typeface Conventions
About the Iolan
Introduction
Iolan Family Models
Hardware
Iolan Features
Software
Ldap
Security
What’s Included
Connectivity
Introduction
Iolan Components
Desktop Models
Power Supply Specifications
Available Accessories
Power Over Ethernet PoE Models
Medical Unit Models
Rack Mount Models except Electric Utility models
Electric Utility models
Overview
Getting to Know Your Iolan
Iolan Model LED Label Green light
Port
Port
End View
Top View
Console Port/LED View
Rack Mount
Serial/Ethernet View
Medical Unit
Power/Ethernet View
Serial View
Front LED/Console portView
Back Serial/Ethernet/power View
Console Mode
Console/Serial Switch
Serial Mode
Dedicated Console Port
Powering Up the Iolan
Desktop/Rack Mount Models excluding Electric Utility models
Left VDC + Right
Models
Secondary back-up Supply
DC Power Models excluding Electric Utility models
Earthing Wire
Primary Supply
Disconnecting 48V Power Supplies from the Iolan
Grounding
Wiring
Terminal # Description Usage
Wiring up an HV unit
Wiring up a DHV unit
Wiring up a the Fail-Safe Relay
Powering Up the Iolan
Configuration Methods Chapter
Configures an IP Address
Configuration Methods Overview
Requires a Configured IP Address
Easy Config Wizard
DeviceManager
Access Platforms
Features
Connecting to the Iolan Using DeviceManager
DeviceManager
Navigating the Options
Using DeviceManager
WebManager
Downloading the Configuration
Iolan
Connecting to the Iolan Using WebManager
Using WebManager
Connecting to the Iolan Using the CLI
Command Line Interface
Through the Network
Through the Serial Port
Using the CLI
Connecting to the Iolan Using the Menu
Menu
Using the Menu
Using DHCP/BOOTP
Connecting to the Iolan Using DHCP/BOOTP
TACACS+ Securid
DHCP/BOOTP Parameters
Snmp
Connecting to the Iolan Using Snmp
Using the Snmp MIB
Using the IOLAN+ Interface
Connecting to the Iolan to Use the IOLAN+ Interface
IOLAN+ Interface
Changes to the IOLAN+ Interface
REMOTE-ADMIN
Opt HEX Rlogin/Telnet
Remote Access Systems Screen
Name Wchiewsds2 Debug mode IP address
IOLAN+ Interface
Getting Started
Easy Configuration Wizard
Setting Up the Network
Using a Direct Serial Connection to Specify an IP Address
Using a Direct Serial Connection to Enable BOOTP/DHCP
For an IPv6 Network
Using ARP-Ping
Setting Up the Serial Ports
Setting Up the Serial Ports
Setting Up Users
Setting Up Users
Using DeviceManager WebManager
DeviceManager
Navigating DeviceManager/WebManager
EasyPort Web
WebManager
Starting a New Session
Using DeviceManager to Connect to the Iolan
Assigning a Temporary IP Address to a New Iolan
Logging in to the Iolan
Adding/Deleting IOLANs Manually
Logging into the Iolan
Using WebManager to Connect to the Iolan
Configuration Files
Creating a New Iolan Configuration in DeviceManager
Importing an Existing Configuration File
Opening an Existing Configuration File
Managing the Iolan
Network Settings
Field Descriptions
IP Settings
IPv4 Settings
Overview
IPv6 Settings
Field Format IPv6 address
Field Format IPv6 address DSN Server
Adding/Editing a Custom IPv6 Address
Prefix Bits Range Default
Server Name.Domain Prefix.Domain Name
Advanced
Configuration
Default 100 ms
Default 200 ms
Default Disabled Advertise DHCPv6
IP Filtering Data Options
Advanced
Host Table
Functionality
Domain Name
Adding/Editing a Host
Host Name
Fully Qualified
Route List
IPv4 Subnet Mask
Default Default
Adding/Editing Routes
Type
DNS/WINS
Editing/Adding DNS/WINS Servers
RIP
Password
Ethernet Mode
Default None
Authentication
Key
Dynamic DNS
Overview Functionality
End Time
System Type
Account Settings
Default Dynamic
User Name
Cipher Suite Field Descriptions
Adding/Editing a Cipher Suite
Validation Criteria Field Descriptions
Common Name
IPv6 Tunnels
Mode
Default Manual
Adding/Editing an IPv6 Tunnel
Name
112 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Functionality
Serial Ports
Editing a Serial Port
Copying a Serial Port
Serial Port Profiles
Resetting a Serial Port
Common Tabs
Hardware Tab Field Descriptions
Flow Control Default Enabled Enable Outbound
Default Full
Default Auto Flow Control
Enable Inbound
Email Alert Tab Field Descriptions
Packet Forwarding Tab Field Descriptions
Packet Size
Enable Trigger1
Enable Trigger2
Packet Definition
Trigger
Default Trigger
EOF1 Character
EOF2 Character
Default Client
SSL/TLS Settings Tab Field Descriptions
124 Iolan SDS/SCS/STS/MDC User’s Guide, Version
125
126 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Protocol
Default Telnet
Console Management Profile
General Tab Field Descriptions
Advanced Tab Field Descriptions
Idle Timeout
Enable Microsoft
Administrator
Support Default Disabled Multisessions
Modem
TruePort Profile
Phone
Multiple Hosts
System Default Enabled Host Name
Connect to remote
Connect to
Adding/Editing a Multihost Entry
Adding/Editing Additional TruePort Hosts
133
Day Motd Default Disabled Enable TCP
Signals high
When
Session Timeout
Enable Data
Logging
TCP Sockets Profile
Connection Workstation/Server on the network Default Enabled
Received on the serial port
Initiate Connection
Adding/Editing Additional Hosts
139
Day Motd Default Disabled Enable Data
141
UDP Sockets Profile
UDP port
Start IP Address
Default 0 zero
Terminal Profile
Direction
145
VT320 specifically supporting VT320-7
Default Dumb
VT100
TVI925
Is received
Default Disabled Protocol
Data Range
149
Login Settings
User Service Settings
Erase
Telnet Settings
Interrupt
Quit
User is only prompted for a password
Rlogin Settings
Escape
SSH Settings
Arcfour
Slip Settings
RSA authentication for the SSH session
Authentication for the SSH session
VJ Compression
Routing
PPP Settings
IPv6 Remote
Default Chap
None
Remote User
Default 3 seconds
Remote Password
Configure Req
Timeout
Address/Control
Default 1 minute
Roaming Callback
Challenge Interval
Printer Profile
Client Iolan Tunnel
Serial Tunneling Profile
Serial Server Tunnel
Serial
Act As Tunnel
Client Default Disabled Host Name
Virtual Modem Profile
165
DCD
AT Command
DTR Signal Acts as RTS Signal Always On RTS Signal Acts as
Response Delay
Phone Number to Host Mapping
Host IP Address
Control Signal I/O Profile
VModem Phone Number Entry
Phone Number
Latch
Input Signal Field Descriptions
Invert Signal
Description
Syslog
Auto Clear Mode
Mode Default Disabled
Manual Clear
Failsafe Action
Output Signal Field Descriptions
Modbus Gateway Profile
Advanced Slave
Settings Button UID Range
Destination Slave
IP Mappings
Default 1000 ms
Default 30 ms
Advanced Field Descriptions
Modbus Slave IP Settings Field Descriptions
UID End
Adding/Editing Modbus Slave IP Settings
Default Host
UID Start
Data Options TCP or UDP
Modbus Slave Advanced Settings Field Descriptions
Default TCP
Range Default 50 ms
Power Management Profile
RPS Model
Editing Power Management Plug Settings Field Descriptions
Default RSP820
RPS Name
Data Options On, Off
Remote Access PPP Profile
Default State
Default Off
Dynamic DNS
Negotiate IP
IPv6 Global
Authentication Tab Field Descriptions
185
Dynamic DNS Field Descriptions
Enable Dynamic
DNS for this Serial Default Disabled Port Host
Account Settings
187
Enable Magic
Configure Request
Compression Default Enabled Enable Protocol
Enable VJ
MS Direct Host
Dial In/Out
MS Direct Guest
Remote Access Slip Profile
191
192 Iolan SDS/SCS/STS/MDC User’s Guide, Version
General Tab Field Description
Custom Application Profile
Local Port Buffering
Port Buffering
Keyboard Buttons Hot Keys Direction
Remote Port Buffers
Field Definitions
NFS Directory
Enable Port
Data Default Disabled Enable Key Stroke
NFS Host
Deny Multiple
Advanced Serial Settings Tab
Signals
Process Break
Session Escape
Default ~menu
Serial Port Menu
String
Adding/Editing a Modem
Modems Tab
Name Name of the modem
Field Definitions
TruePort Baud Rate Tab
Configuring Users
User Settings
General Tab
Adding/Editing Users
Default Normal
Host IP
Services Tab
Service
Default DSPrompt
Indentifier
IPv6 Interface
Advanced Tab
Default English
Sessions Tab
Connect
Session 1, 2, 3
Clustered Ports
Serial Port Access Tab
Serial Port Access
Allow Access to
212 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Authentication
Configuring Security
Method
Authentication
Method Default Local Secondary
Primary
Local
General Field Descriptions
Radius
NAS-Identifier
Authenticator response Default Enabled Retry
Address Default Enabled
Attributes Field Descriptions
KDC Port
Kerberos
Realm
KDC Domain
Base
Enable TLS
TLS Port
Primary Host Default None
Authentication Authorization Primary Host Secondary Host
Default None Authentication
Authorization Port Default Authentication
SecurID
NIS
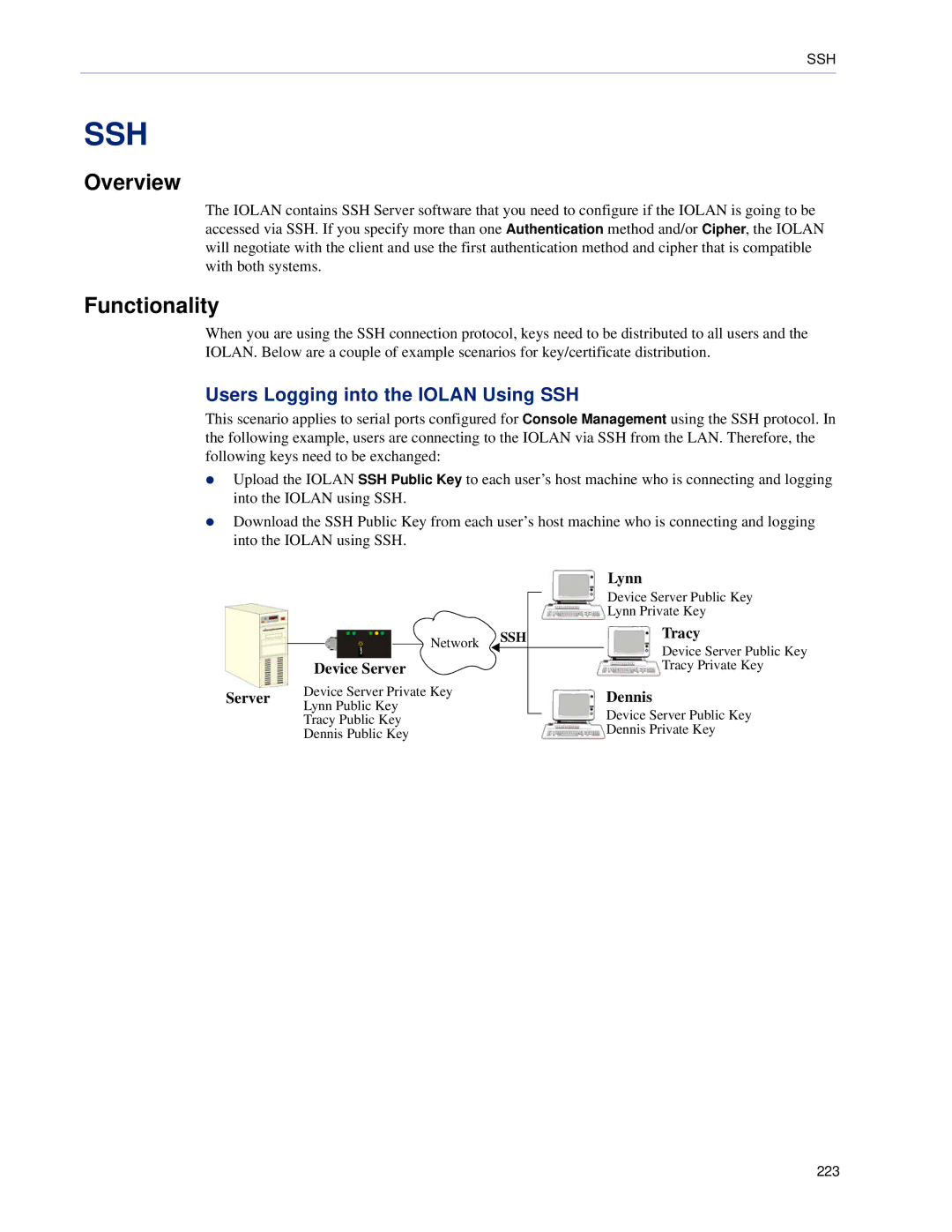
Tracy
Users Logging into the Iolan Using SSH
Device Server
Lynn
Lynn Sales Server
Users Passing Through the Iolan Using SSH Dir/Sil
HR Server
Allow SSH-1
Protocol Default Disabled
Interactive Default Enabled Password
Field Descriptions
Output Default Disabled
Enable Verbose
Break String
Button For a valid SSL/TLS connection
228 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Adding/Editing a Cipher
230 Iolan SDS/SCS/STS/MDC User’s Guide, Version
VPN
IPsec
IKE Phase 1 Proposals
ESP Phase 2 Proposals
Authentication Algorithms-MD5, SHA1, SHA2
Adding/Editing the IPsec Tunnel
Local Device
Default Left
Secret/Remote
Validation Criteria
Shared Secret Field Description
Remote Validation Criteria Field Descriptions
Allow L2TP/IPsec
L2TP/IPsec
Exceptions
Field Description
Adding/Editing a VPN Exception
Syslog Client
Services
Telnet Server
TruePort Full
Sntp Client
DeviceManager
WebManager
SSH Server
Keys and Certificates
Key Type
244 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Configuring I/O InterfacesChapter
Access Functionality
Settings
Advanced Slave Modbus Settings
Request Queuing
Default 30 seconds
Failsafe Timer Functionality
Failsafe Action is triggered
Broadcast of I/O Default Disabled Status
Enable UDP
UDP Functionality
UDP Entry
UDP Settings
Default Celsius
Temperature Functionality
Analog I/O Analog
Channels
Analog
Monitoring Application A4D2
Alarm Settings
Default Current
Monitoring Application
Digital Input
Digital I/O
Input Mode
257
Digital Output
Default Sink
Output Mode
Output
Pulse Count
Pulse Mode
Inactive Signal Width Active Signal Width
Delay
Monitoring Application A4D2Relay
Relay
Relay I/O
Width
Inactive Signal
Warehouse Perle Iolan Reception
Active Signal
Digital I/O Extension
Front Door
Message type 1 Byte
Current Alarm State 1 Byte z 0 = Not in alarm
Input number 1 Byte
Extension
Enable I/O
Input TCP Port
Local connection
Hosts
Simultaneously
Communicate to the Host
Temperature I/O Industrial Freezers
Temperature
Default RTD
Basic Analog Alarm Settings
Alarm Settings
Clear Mode
Advanced Analog Alarm Settings
Trigger Type
Clear
UDP Broadcast Packet
UDP Unicast Format
Analog Section
Length Enabled
Section Channel
Length Pin
Serial Pin Signal Section
Digital/Relay Section
Length Channel
Modbus Serial Application Connected to the Network
Modbus Slave
UDP Unicast Example
Modbus Serial Application Connected to the Serial Port
PC running a Modbus RTU or Ascii Application UID
Modbus I/O Access
Modbus TCP Application
Function Codes
Coil/Register Descriptions
Input Registers
Serial Port Coil/Register Descriptions
A4/T4 Registers
Data Model A1/T1 A2/T2 A3/T3 A4/T4 Holding Registers
Data Model D1/R1 D2/R2 Coils
A4D2/A4R2 Registers
Data Model Pin Coils
Serial Pin Signals
D4/D2R2 Registers
Data Model D3/R1 D4/R2 Coils
PC running a
Modbus Serial Application TruePort Power Digital Output
TruePort I/O
TruePort/Modbus Combination
PC running Custom Application API TruePort
API Over TruePort Only
Setup
Accessing I/O Data Via TruePort
Introduction
Response Format
Format of API Commands
Get Commands
Command Format
Set Commands
Example 2 Turn on the first and second relay on a D2R2 unit
Successful Response Format
Unsuccessful Response Format
Example 1 Turn on the first relay on a D2R2 unit
Snmp Traps
Error Codes
290 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Clustering Slave List
Configuring Clustering Chapter
Advanced Button
Adding Clustering Slaves
Advanced Clustering Slave Options
Editing Clustering Slave Settings
Port Name
Master TCP Port
Slave TCP Port
Option Card Settings
Configuring the Option Card
Configuring the Iolan Modem Card
Overview Field Descriptions
Configuring a Wireless WAN Card
Card
APN
298 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Alerts
Configuring the System Chapter
Email Alerts
Alerts
Syslog
Community
Management
Contact
Location
Privacy Password
Auth Algorithm Data Options MD5, SHA Default MD5
Auth Password
Default DES
Time
Algorithm Data Options MD5, SHA Default MD5
Privacy Algorithm Data Options DES, AES Default DES
Confirm Password Trap
Network Time Tab Field Descriptions
Sntp Mode
Sntp Version
Time Zone/Summer Time Tab Field Descriptions
Custom App/Plugin
Login Tab Field Descriptions
Bootup Files Tab Field Descriptions
Display Motd WebManager EasyPort Web
Message of the Day Motd Tab Field Descriptions
Tftp Host
Filename
Baud Rate
Default Flow Control
Tftp Tab Field Descriptions
Console Port Tab Field Descriptions
312 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Controlling the RPS, I/O Channels, and IPsec Tunnels
State Button Management profile settings
RPS Control
OK Button Closes the window
Plug Control
Power Plug Status
Serial Port Power Control
Button Serial port
Deactivate Output Manually deactivates the channel output
IPsec Tunnel Control
318 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Managing Configuration Files
System Administration Chapter
Saving Configuration Files
Downloading Configuration Files
Reboot Server
Downloading Configuration Files to Multiple IOLANs
Specifying a Custom Factory Default Configuration
Uploading Configuration Files
Calibrating Analog Input
Resetting the Iolan to the Default Configuration
Downloading Iolan Firmware
Calibrating I/O
Calibrating Thermocouple
Calibrating Temperature Input
Calibrating Voltage
Calibrating Current
Calibrating Analog Channels
Resetting Calibration Data
Rebooting the Iolan
Setting the IOLAN’s Date and Time
Resetting the Iolan to Factory Defaults
Language Support
Resetting the SecurID Node Secret
Loading a Supplied Language
Translation Guidance
Software Upgrades and Language Files
Creating Terminal Definition Files
Downloading Terminal Definitions
For example
Resetting Configuration Parameters
Lost Admin Password
332 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Applications
Configuring Modbus
Configuring a Master Gateway
Configuring a Slave Gateway
Modbus Master Gateway
Modbus Gateway Settings
Modbus Slave Gateway
Master Gateway Serial EIA-232
Modbus Serial Port Settings
Modbus Master Settings
Modbus Slave UID
Modbus Master Slave Gateway
Modbus Slave Settings
Serial Port EIA-422/485 Modbus Master Modbus Slave UID
172.16.0.0
Configuring PPP Dial On Demand
Remote Printing Using LPD
Setting Up Printers
Remote Printing Using Host-Based Print Handling Software
Remote Printing Using RCP
IOLAN-to-Host/Network
Configuring a Virtual Private Network
Or just
172.16.45.84 192.168.45.87 192.168.45.12
Network-to-Network
172.16.45.99
Host-to-Host
Left External IP Address Right
Gateway Router
344 Iolan SDS/SCS/STS/MDC User’s Guide, Version
VPN Client Initiate Communication Router Broadband Right
VPN Client-to-Network
346 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Supported Radius Parameters
Radius and TACACS+ Appendix a
PPP
User level. See Perle Radius Dictionary Example
Accounting Message
Radius Parameter Iolan Parameter
Mapped Radius Parameters to Iolan Parameters
Perle Radius Dictionary Example
Value
TACACS+
Accessing the Iolan Through a Serial Port Users
Name Values Description
Slip
Accessing the Iolan from the Network Users
Accessing the Iolan from the Network User Example Settings
Valid SSL/TLS Ciphers
SSL/TLS Ciphers
DES-CBC-MD5
Virtual Modem Initialization Commands
Commands
AT&Rn
AT&Sn
AT&Cn
Serial Pinouts
Pinouts and Cabling Diagrams
DB25 Male
DB25 Female
RJ45
Number Iolan model Pins See
RJ45 for desktop and rack mount models
RJ45 for SCS48C/SCS32C/SCS16C/SCS8C models
Pinout EIA-232 Admin Port Serial Ports
EIA-485 Pin# EIA-232 EIA-422 Full Duplex Half Duplex
RJ45 for SDS32C/SDS16C/SDS8C Electric Utility models
RJ45 for medical unit models
DB9 Male Serial Only
DB9 Male I/O
Power Over Ethernet Pinouts
DB25 Female
EIA-232 Cabling Diagrams
Terminal DB25 Connector
DB25 Male
10-pin Pin
RJ45
DB9 Male
Iolan RJ45 DCE
Modem DB25 Connector
RxD TxD DTR 20 DTR GND
376 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Port Iolan DB25 Male/Female
Setting Jumpers
Port Iolan RJ45
Port Iolan RJ45 P Power Over Ethernet
Port Iolan SDS1M Modem
Port Iolan DB9
Port Iolan
Port/Line # Line Termination 5V Output Input Volt Output
Port Desktop Iolan
Digital I/O Module
Analog Input Module
384 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Digital Input Dry Contact
Wiring I/O Diagrams
Digital I/O
Digital Input Wet Contact
Digital Output Source
Digital Output Sink
Current
Analog Input
Voltage
Thermocouple
Temperature Input
RTD 2-Wire
RTD 3-Wire
Normally Closed Contact
RTD 4-Wire
Relay Output
Normally Open Contact
390 Iolan SDS/SCS/STS/MDC User’s Guide, Version
TruePort
Utilities
API Request Format
API I/O Access Over TruePort
API Response Format
Decoder
Error Codes
394 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Installing a Perle PCI Card
Accessories
Installing a Perle PCI Card
Accessories
RJ45F to DB25M DTE Crossover Adapter
Starter Kit Adapters/Cable
RJ45F to DB25M DCE Modem Adapter
RJ45F DB25F
RJ45F to DB25F DTE Crossover Adapter
RJ45F to DB9M DTE Crossover Adapter
RJ45F to DB9F DTE Crossover Adapter
Sun/Cisco RJ45M Connector Cable for Rack Mount Models
SCS48C/SCS32C/SCS16C/SCS8C Starter Kit Adapters/Cable
GND DTR 20 DTR DSR
RJ45F to DB25F DTE Crossover Adapter
406 Iolan SDS/SCS/STS/MDC User’s Guide, Version
RJ45F
Sun/Cisco Roll-Over Adapter for Rack Mount Models
408 Iolan SDS/SCS/STS/MDC User’s Guide, Version
Hardware Troubleshooting
Troubleshooting
General communication checks and practices are as follows
Communication Issues
DeviceManager Problems
Power/Ready LED Labels
Radius Authentication Problems
Host Problems
Problems with Terminals
Login Problems
You observe Tftp errors when the Iolan boots, for example
DHCP/BOOTP Problems
Callback Problems
Language Problems
Long Reboot Cycle
Modem Problems
PPP Problems
Printing Problems
An A4R2 model is starting/stopping
Certificate did not match configuration
Models
Could not obtain peers certificate
IPv6 Issues
Making a Technical Support Query
Contacting Technical Support
Feedback on this Manual
Repair Procedure
Glossary
RIP Routing
PAP Password
Authentication Protocol Radius Remote
Authentication Dial Users Services Reverse Connection
API
Index
Ldap
Radius