Prestige 201 ISDN Access Router
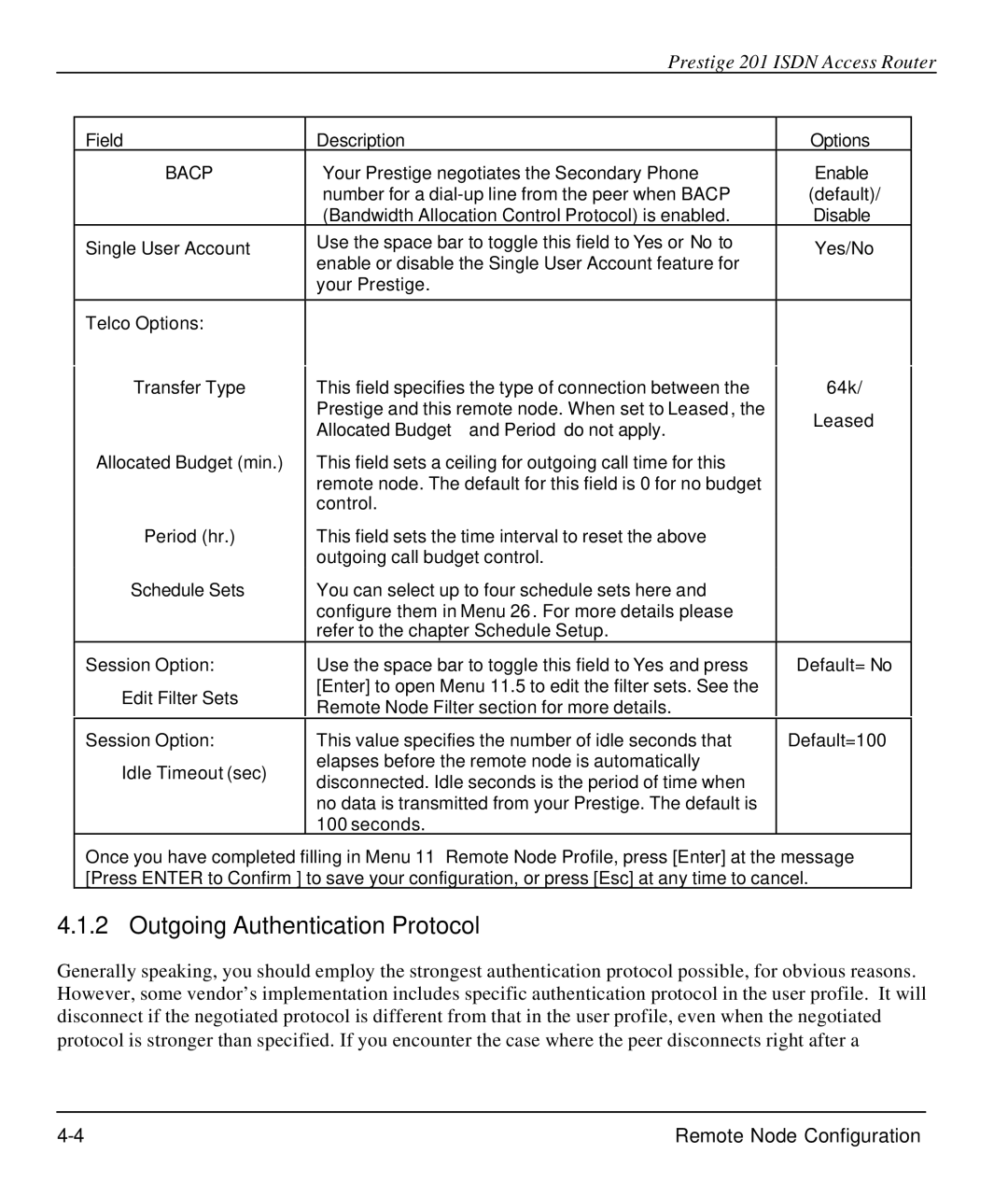
Field | Description | Options | |
BACP | Your Prestige negotiates the Secondary Phone | Enable | |
| number for a | (default)/ | |
| (Bandwidth Allocation Control Protocol) is enabled. | Disable | |
Single User Account | Use the space bar to toggle this field to Yes or No to | Yes/No | |
enable or disable the Single User Account feature for | |||
|
| ||
| your Prestige. |
| |
|
|
| |
Telco Options: |
|
| |
|
|
| |
Transfer Type | This field specifies the type of connection between the | 64k/ | |
| Prestige and this remote node. When set to Leased, the | Leased | |
| Allocated Budget and Period do not apply. | ||
|
| ||
Allocated Budget (min.) | This field sets a ceiling for outgoing call time for this |
| |
| remote node. The default for this field is 0 for no budget |
| |
| control. |
| |
Period (hr.) | This field sets the time interval to reset the above |
| |
| outgoing call budget control. |
| |
Schedule Sets | You can select up to four schedule sets here and |
| |
| configure them in Menu 26. For more details please |
| |
| refer to the chapter Schedule Setup. |
| |
Session Option: | Use the space bar to toggle this field to Yes and press | Default= No | |
Edit Filter Sets | [Enter] to open Menu 11.5 to edit the filter sets. See the |
| |
Remote Node Filter section for more details. |
| ||
|
| ||
Session Option: | This value specifies the number of idle seconds that | Default=100 | |
Idle Timeout (sec) | elapses before the remote node is automatically |
| |
disconnected. Idle seconds is the period of time when |
| ||
|
| ||
| no data is transmitted from your Prestige. The default is |
| |
| 100 seconds. |
|
Once you have completed filling in Menu 11– Remote Node Profile, press [Enter] at the message [Press ENTER to Confirm…] to save your configuration, or press [Esc] at any time to cancel.
4.1.2 Outgoing Authentication Protocol
Generally speaking, you should employ the strongest authentication protocol possible, for obvious reasons. However, some vendor’s implementation includes specific authentication protocol in the user profile. It will disconnect if the negotiated protocol is different from that in the user profile, even when the negotiated protocol is stronger than specified. If you encounter the case where the peer disconnects right after a
Remote Node Configuration |