Chapter 9: Authentication
RADIUS: The Remote Authentication
http://www.cisco.com/en/US/tech/tk59/technologies_tech_note09186a00800945cc.shtml
http://www.freeradius.org/
9.1.4 LDAP Authentication
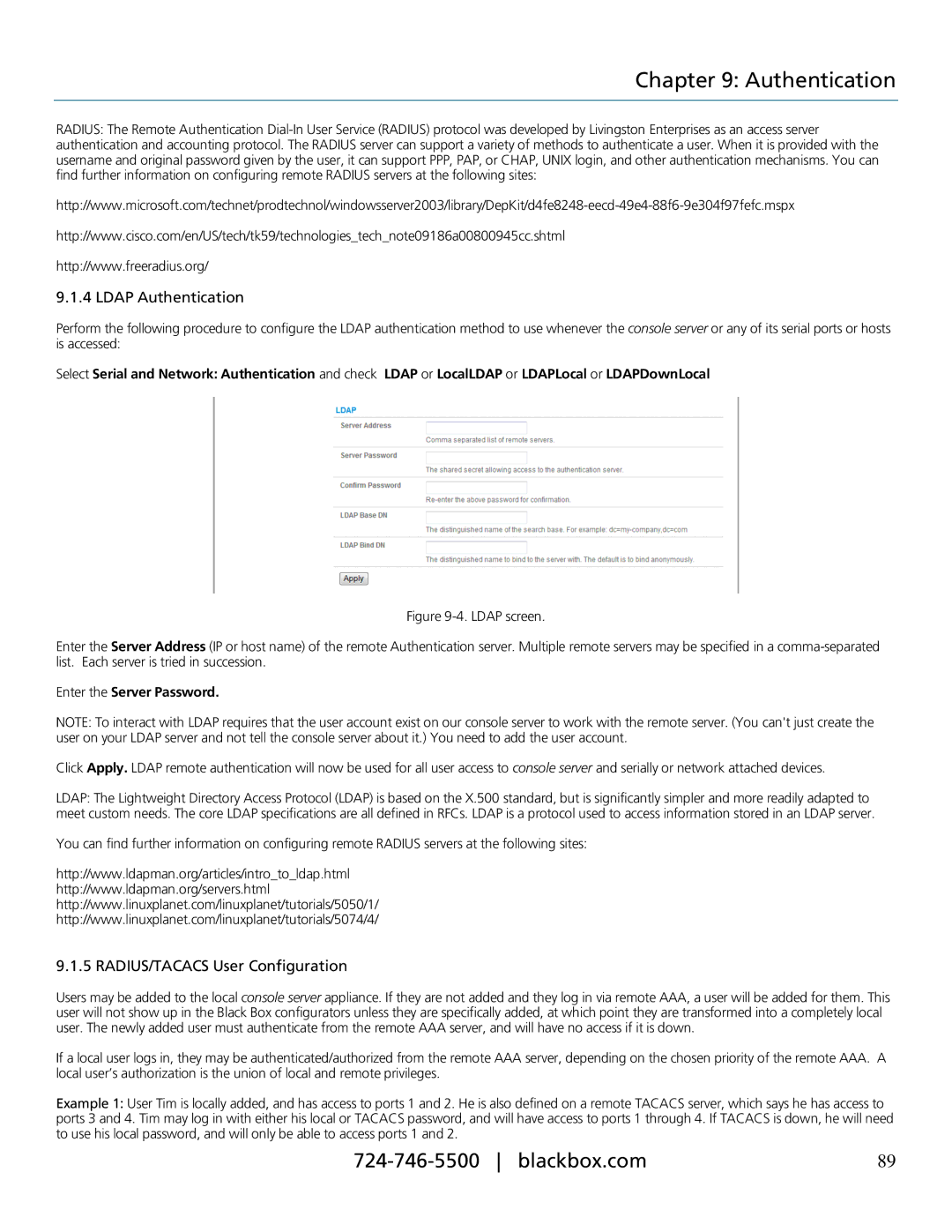
Perform the following procedure to configure the LDAP authentication method to use whenever the console server or any of its serial ports or hosts is accessed:
Select Serial and Network: Authentication and check LDAP or LocalLDAP or LDAPLocal or LDAPDownLocal
Figure 9-4. LDAP screen.
Enter the Server Address (IP or host name) of the remote Authentication server. Multiple remote servers may be specified in a comma-separated list. Each server is tried in succession.
Enter the Server Password.
NOTE: To interact with LDAP requires that the user account exist on our console server to work with the remote server. (You can't just create the user on your LDAP server and not tell the console server about it.) You need to add the user account.
Click Apply. LDAP remote authentication will now be used for all user access to console server and serially or network attached devices.
LDAP: The Lightweight Directory Access Protocol (LDAP) is based on the X.500 standard, but is significantly simpler and more readily adapted to meet custom needs. The core LDAP specifications are all defined in RFCs. LDAP is a protocol used to access information stored in an LDAP server.
You can find further information on configuring remote RADIUS servers at the following sites:
http://www.ldapman.org/articles/intro_to_ldap.html
http://www.ldapman.org/servers.html
http://www.linuxplanet.com/linuxplanet/tutorials/5050/1/
http://www.linuxplanet.com/linuxplanet/tutorials/5074/4/
9.1.5 RADIUS/TACACS User Configuration
Users may be added to the local console server appliance. If they are not added and they log in via remote AAA, a user will be added for them. This user will not show up in the Black Box configurators unless they are specifically added, at which point they are transformed into a completely local user. The newly added user must authenticate from the remote AAA server, and will have no access if it is down.
If a local user logs in, they may be authenticated/authorized from the remote AAA server, depending on the chosen priority of the remote AAA. A local user’s authorization is the union of local and remote privileges.
Example 1: User Tim is locally added, and has access to ports 1 and 2. He is also defined on a remote TACACS server, which says he has access to ports 3 and 4. Tim may log in with either his local or TACACS password, and will have access to ports 1 through 4. If TACACS is down, he will need to use his local password, and will only be able to access ports 1 and 2.
89 |