|
|
| Configuration Options |
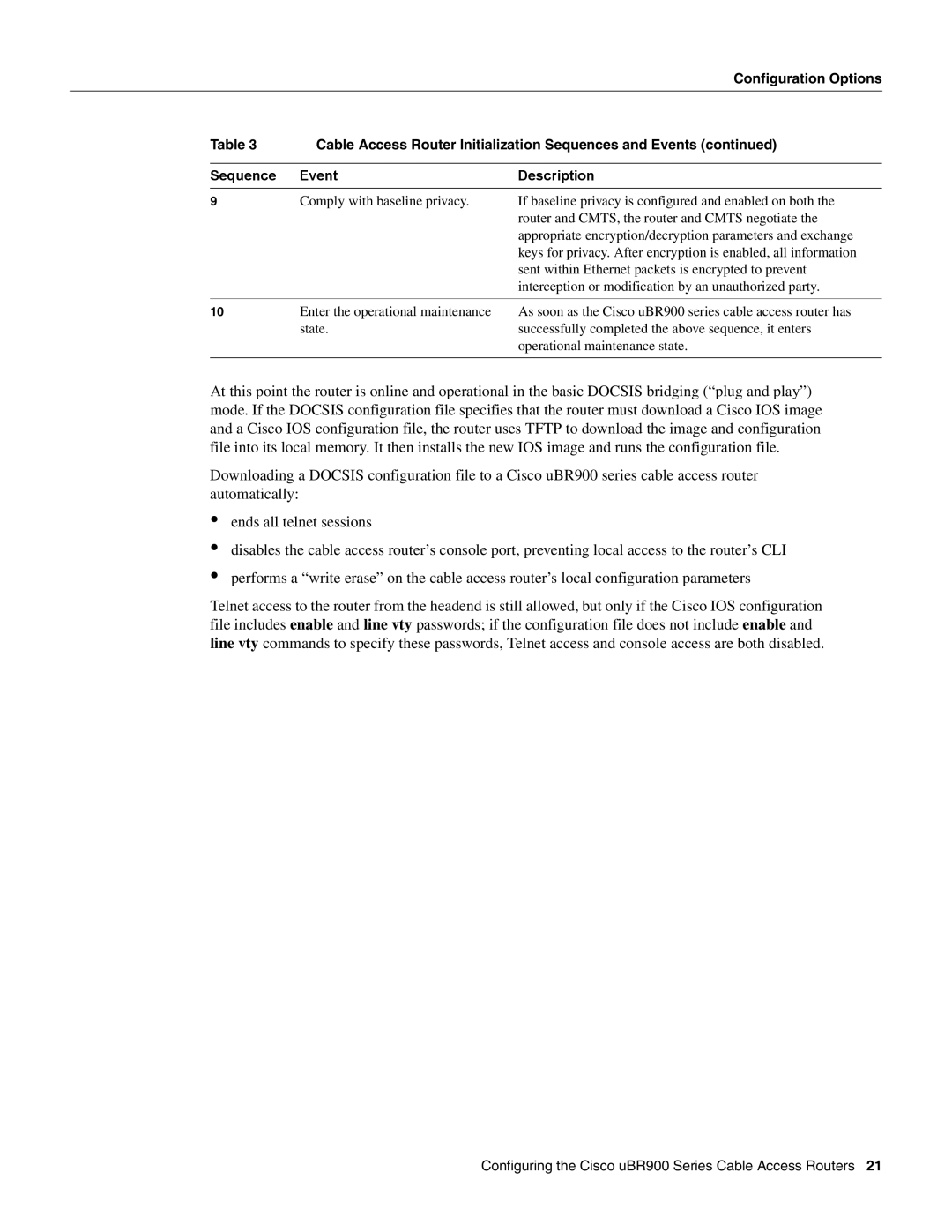
| Table 3 | Cable Access Router Initialization Sequences and Events (continued) | |
|
|
|
|
| Sequence | Event | Description |
|
|
|
|
9 | Comply with baseline privacy. | If baseline privacy is configured and enabled on both the | |
|
|
| router and CMTS, the router and CMTS negotiate the |
|
|
| appropriate encryption/decryption parameters and exchange |
|
|
| keys for privacy. After encryption is enabled, all information |
|
|
| sent within Ethernet packets is encrypted to prevent |
|
|
| interception or modification by an unauthorized party. |
|
|
|
|
10 | Enter the operational maintenance | As soon as the Cisco uBR900 series cable access router has | |
|
| state. | successfully completed the above sequence, it enters |
|
|
| operational maintenance state. |
|
|
|
|
At this point the router is online and operational in the basic DOCSIS bridging (“plug and play”) mode. If the DOCSIS configuration file specifies that the router must download a Cisco IOS image and a Cisco IOS configuration file, the router uses TFTP to download the image and configuration file into its local memory. It then installs the new IOS image and runs the configuration file.
Downloading a DOCSIS configuration file to a Cisco uBR900 series cable access router automatically:
•
•
•
ends all telnet sessions
disables the cable access router’s console port, preventing local access to the router’s CLI
performs a “write erase” on the cable access router’s local configuration parameters
Telnet access to the router from the headend is still allowed, but only if the Cisco IOS configuration file includes enable and line vty passwords; if the configuration file does not include enable and line vty commands to specify these passwords, Telnet access and console access are both disabled.
Configuring the Cisco uBR900 Series Cable Access Routers 21