|
| Chapter 5: Protection 79 |
|
|
|
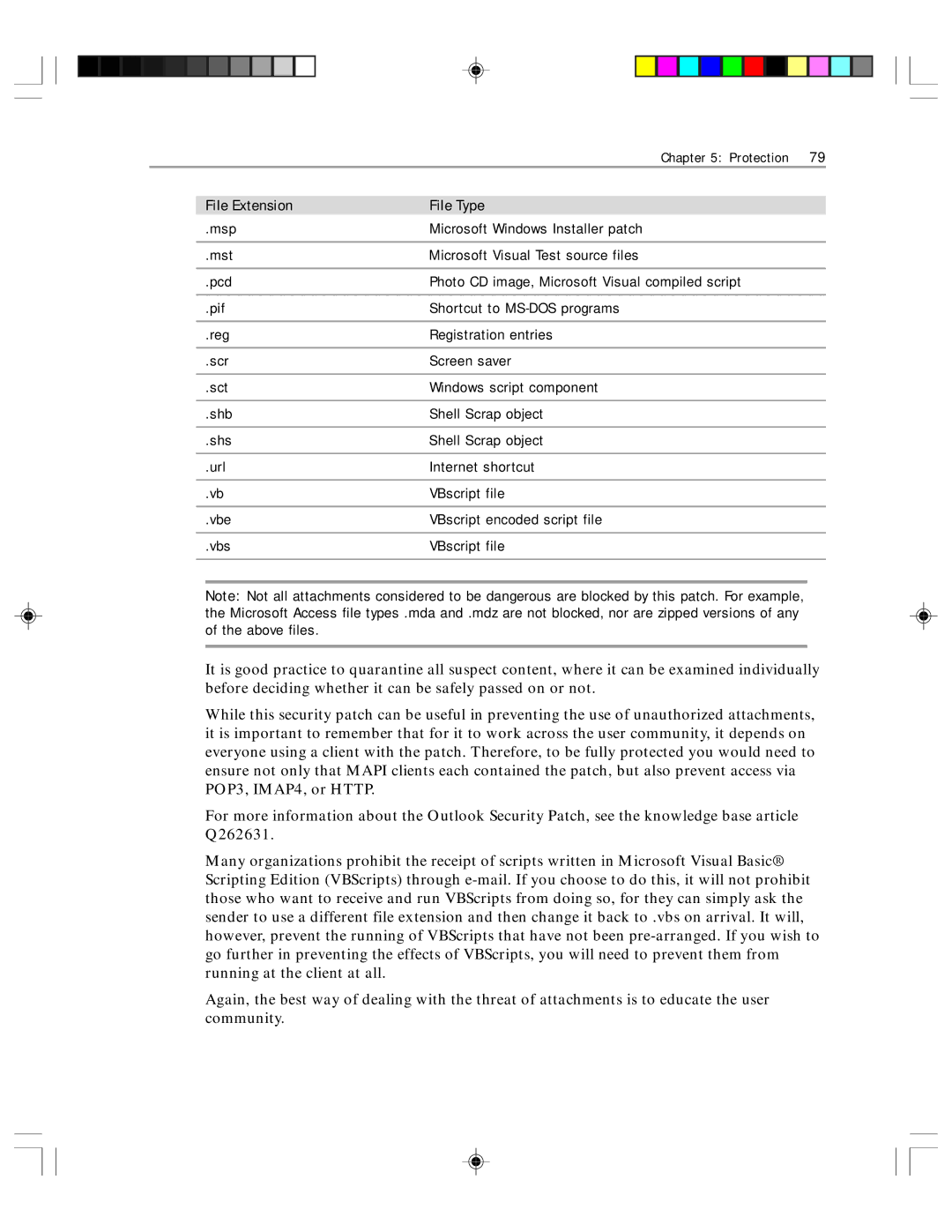
| File Extension | File Type |
| .msp | Microsoft Windows Installer patch |
|
|
|
| .mst | Microsoft Visual Test source files |
|
|
|
| .pcd | Photo CD image, Microsoft Visual compiled script |
|
|
|
| .pif | Shortcut to |
|
|
|
| .reg | Registration entries |
|
|
|
| .scr | Screen saver |
|
|
|
| .sct | Windows script component |
|
|
|
| .shb | Shell Scrap object |
|
|
|
| .shs | Shell Scrap object |
|
|
|
| .url | Internet shortcut |
|
|
|
| .vb | VBscript file |
|
|
|
| .vbe | VBscript encoded script file |
|
|
|
| .vbs | VBscript file |
|
|
|
Note: Not all attachments considered to be dangerous are blocked by this patch. For example, the Microsoft Access file types .mda and .mdz are not blocked, nor are zipped versions of any of the above files.
It is good practice to quarantine all suspect content, where it can be examined individually before deciding whether it can be safely passed on or not.
While this security patch can be useful in preventing the use of unauthorized attachments, it is important to remember that for it to work across the user community, it depends on everyone using a client with the patch. Therefore, to be fully protected you would need to ensure not only that MAPI clients each contained the patch, but also prevent access via POP3, IMAP4, or HTTP.
For more information about the Outlook Security Patch, see the knowledge base article Q262631.
Many organizations prohibit the receipt of scripts written in Microsoft Visual Basic® Scripting Edition (VBScripts) through
Again, the best way of dealing with the threat of attachments is to educate the user community.