OnSite 2800 Series User Manual | 7 • Access control list configuration |
|
|
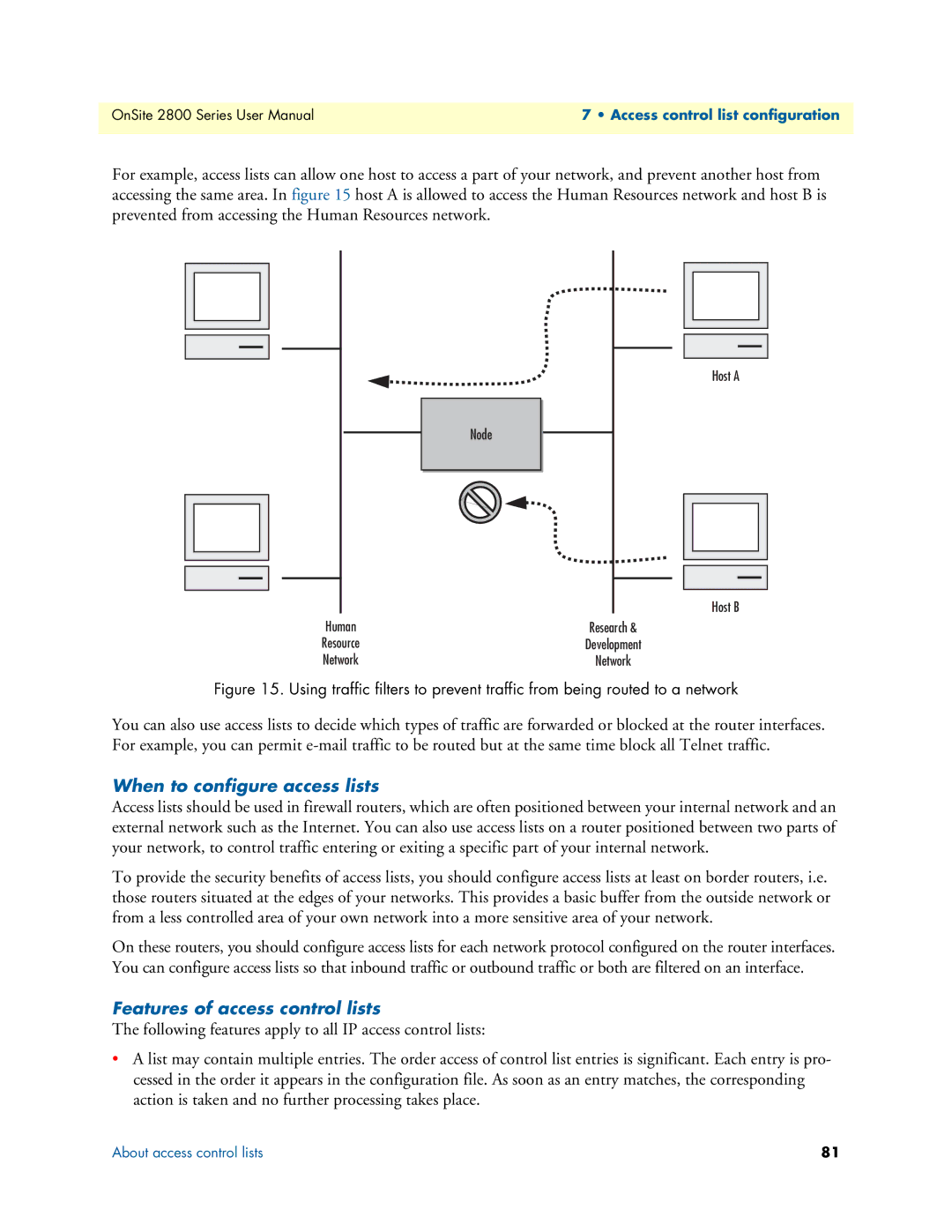
For example, access lists can allow one host to access a part of your network, and prevent another host from accessing the same area. In figure 15 host A is allowed to access the Human Resources network and host B is prevented from accessing the Human Resources network.
NodeNode
Host A
Host B
Human | Research & |
Resource | Development |
Network | Network |
Figure 15. Using traffic filters to prevent traffic from being routed to a network
You can also use access lists to decide which types of traffic are forwarded or blocked at the router interfaces. For example, you can permit
When to configure access lists
Access lists should be used in firewall routers, which are often positioned between your internal network and an external network such as the Internet. You can also use access lists on a router positioned between two parts of your network, to control traffic entering or exiting a specific part of your internal network.
To provide the security benefits of access lists, you should configure access lists at least on border routers, i.e. those routers situated at the edges of your networks. This provides a basic buffer from the outside network or from a less controlled area of your own network into a more sensitive area of your network.
On these routers, you should configure access lists for each network protocol configured on the router interfaces. You can configure access lists so that inbound traffic or outbound traffic or both are filtered on an interface.
Features of access control lists
The following features apply to all IP access control lists:
•A list may contain multiple entries. The order access of control list entries is significant. Each entry is pro- cessed in the order it appears in the configuration file. As soon as an entry matches, the corresponding action is taken and no further processing takes place.
About access control lists | 81 |