Grey Headline (continued)
Security
TANDBERG VIDEO COMMUNICATIONS SERVER ADMINISTRATOR GUIDE
Overview |
| Enabling Security |
|
|
|
For extra security, you may wish to have the VCS communicate with other systems (e.g. servers such as LDAP servers, neighbor VCSs, or clients such as SIP endpoints) using TLS encryption.
For this to work successfully in a connection between a client and server:
•the server must have a certificate installed that verifies its identity. This certificate must be signed by a Certificate Authority
(CA).
•the client must trust the CA that signed the certificate used by the server.
The VCS allows you to install appropriate files so that it can act as either a client or a server in connections using TLS.
For an endpoint to VCS connection, the
VCS will be the TLS server. For a VCS to LDAP server connection, the VCS will
be a client. For a VCS to VCS connection either VCS may be the client with the other VCS being the TLS server.
To enable security using the web interface:
•Maintenance > Security.
You will be taken to the Security page.
The files that enable secure
connections over TLS are installed via the web interface. They cannot be
installed using the CLI.
|
|
|
|
|
|
|
|
|
|
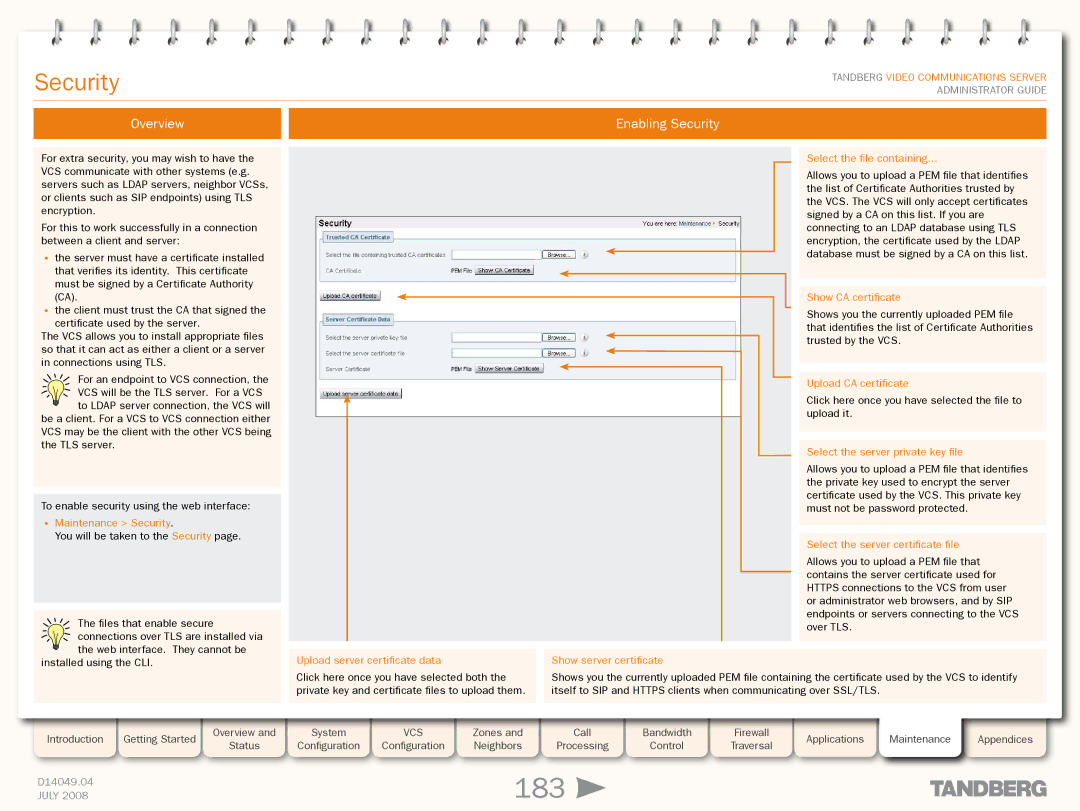
| Select the file containing... |
|
|
|
|
|
|
|
|
|
|
| Allows you to upload a PEM file that identifies |
|
|
|
|
|
|
|
|
|
|
| the list of Certificate Authorities trusted by |
|
|
|
|
|
|
|
|
|
|
| the VCS. The VCS will only accept certificates |
|
|
|
|
|
|
|
|
|
|
| signed by a CA on this list. If you are |
|
|
|
|
|
|
|
|
|
|
| connecting to an LDAP database using TLS |
|
|
|
|
|
|
|
|
|
|
| encryption, the certificate used by the LDAP |
|
|
|
|
|
|
|
|
|
|
| database must be signed by a CA on this list. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Show CA certificate |
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
| Shows you the currently uploaded PEM file |
|
|
|
|
|
|
|
|
|
|
| that identifies the list of Certificate Authorities |
|
|
|
|
|
|
|
|
|
|
| trusted by the VCS. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Upload CA certificate |
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
| Click here once you have selected the file to |
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
| upload it. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Select the server private key file |
|
|
|
|
|
|
|
|
|
|
| Allows you to upload a PEM file that identifies |
|
|
|
|
|
|
|
|
|
|
| the private key used to encrypt the server |
|
|
|
|
|
|
|
|
|
|
| certificate used by the VCS. This private key |
|
|
|
|
|
|
|
|
|
|
| must not be password protected. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Select the server certificate file |
|
|
|
|
|
|
|
|
|
|
| Allows you to upload a PEM file that |
|
|
|
|
|
|
|
|
|
|
| contains the server certificate used for |
|
|
|
|
|
|
|
|
|
|
| HTTPS connections to the VCS from user |
|
|
|
|
|
|
|
|
|
|
| or administrator web browsers, and by SIP |
|
|
|
|
|
|
|
|
|
|
| endpoints or servers connecting to the VCS |
|
|
|
|
|
|
|
|
|
|
| over TLS. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||||||
Upload server certificate data |
| Show server certificate | |||||||||
Click here once you have selected both the |
| Shows you the currently uploaded PEM file containing the certificate used by the VCS to identify | |||||||||
private key and certificate files to upload them. |
| itself to SIP and HTTPS clients when communicating over SSL/TLS. | |||||||||
|
|
|
|
|
|
|
|
|
|
|
|
Introduction | Getting Started |
| Overview and |
| System |
| VCS |
| Zones and |
| Call |
| Bandwidth |
| Firewall |
| Applications |
| Maintenance |
| Appendices |
| Status |
| Configuration |
| Configuration |
| Neighbors |
| Processing |
| Control |
| Traversal |
|
|
| |||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
D14049.04 |
|
|
|
|
|
|
|
| 183 |
|
|
|
|
|
|
|
|
|
| ||
JULY 2008 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||