Microsoft VPN
IKE Phase 2 Screen
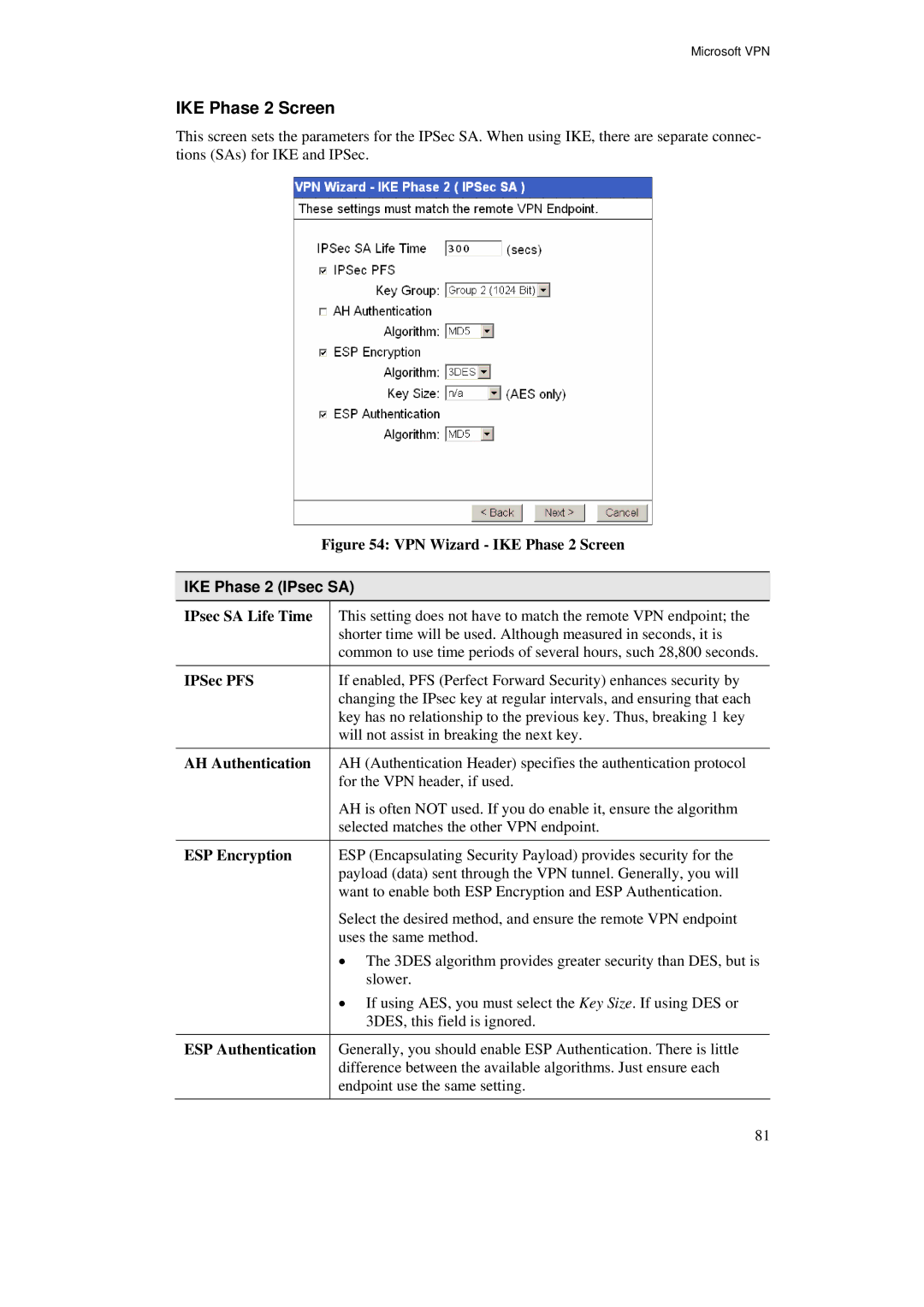
This screen sets the parameters for the IPSec SA. When using IKE, there are separate connec- tions (SAs) for IKE and IPSec.
Figure 54: VPN Wizard - IKE Phase 2 Screen
IKE Phase 2 (IPsec SA)
IPsec SA Life Time | This setting does not have to match the remote VPN endpoint; the |
| shorter time will be used. Although measured in seconds, it is |
| common to use time periods of several hours, such 28,800 seconds. |
IPSec PFS | If enabled, PFS (Perfect Forward Security) enhances security by |
| changing the IPsec key at regular intervals, and ensuring that each |
| key has no relationship to the previous key. Thus, breaking 1 key |
| will not assist in breaking the next key. |
AH Authentication | AH (Authentication Header) specifies the authentication protocol |
| for the VPN header, if used. |
| AH is often NOT used. If you do enable it, ensure the algorithm |
| selected matches the other VPN endpoint. |
ESP Encryption | ESP (Encapsulating Security Payload) provides security for the |
| payload (data) sent through the VPN tunnel. Generally, you will |
| want to enable both ESP Encryption and ESP Authentication. |
| Select the desired method, and ensure the remote VPN endpoint |
| uses the same method. |
| • The 3DES algorithm provides greater security than DES, but is |
| slower. |
| • If using AES, you must select the Key Size. If using DES or |
| 3DES, this field is ignored. |
ESP Authentication | Generally, you should enable ESP Authentication. There is little |
| difference between the available algorithms. Just ensure each |
| endpoint use the same setting. |
81