Security Configuration
Logs
The Logs record various types of activity on the
Since only a limited amount of log data can be stored in the
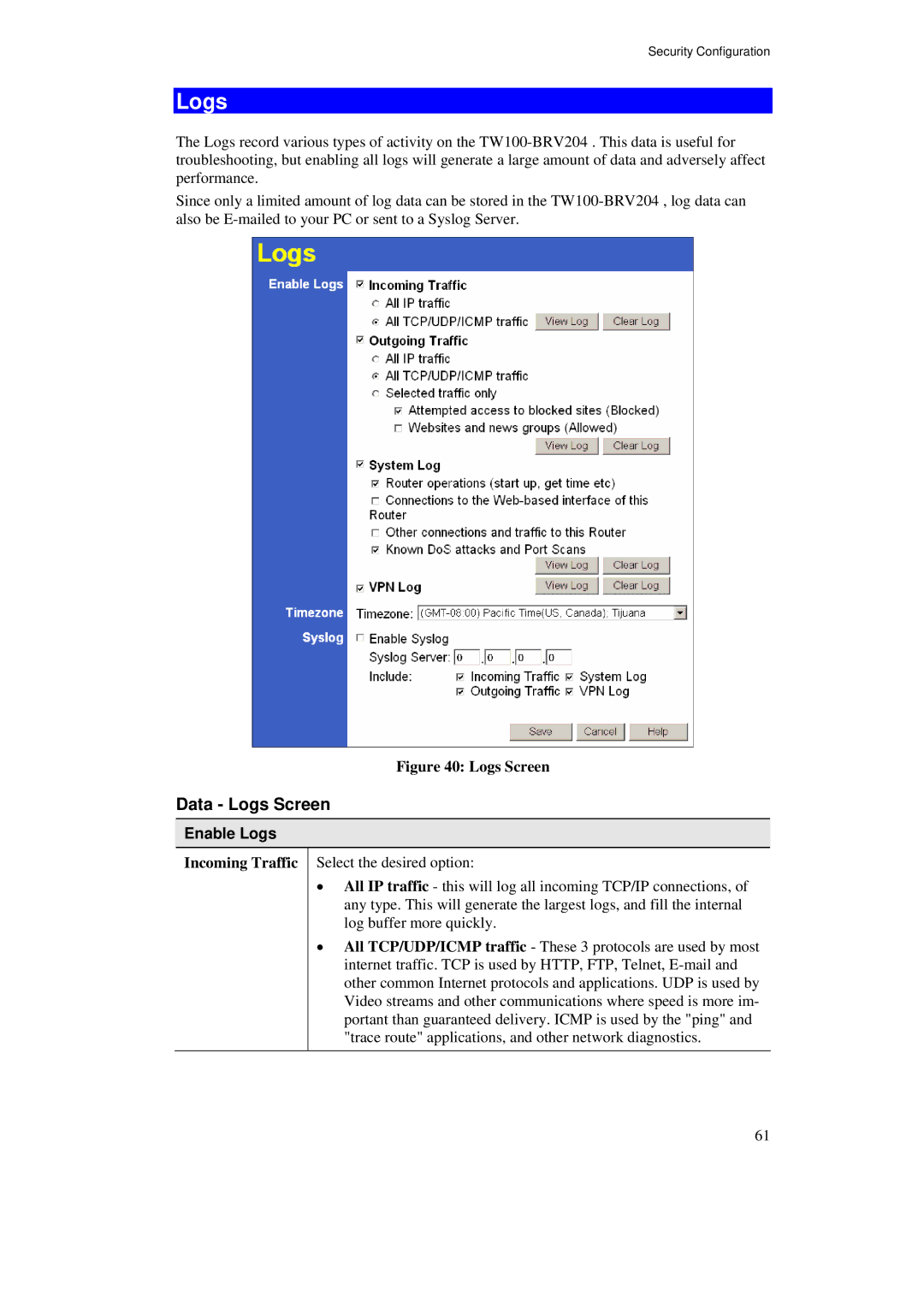
Figure 40: Logs Screen
Data - Logs Screen
Enable Logs
Incoming Traffic Select the desired option:
•All IP traffic - this will log all incoming TCP/IP connections, of any type. This will generate the largest logs, and fill the internal log buffer more quickly.
•All TCP/UDP/ICMP traffic - These 3 protocols are used by most internet traffic. TCP is used by HTTP, FTP, Telnet,
61