Chapter 6 Network Security Monitoring
A key aspect of network security deployment is the ability to monitor the network for security events, analyze them, and perform counter measures. To that end, the
•collect, monitor, and correlate security events/alerts in the network
•analyze security events based on context
•categorize and escalate events for intrusion response decisions
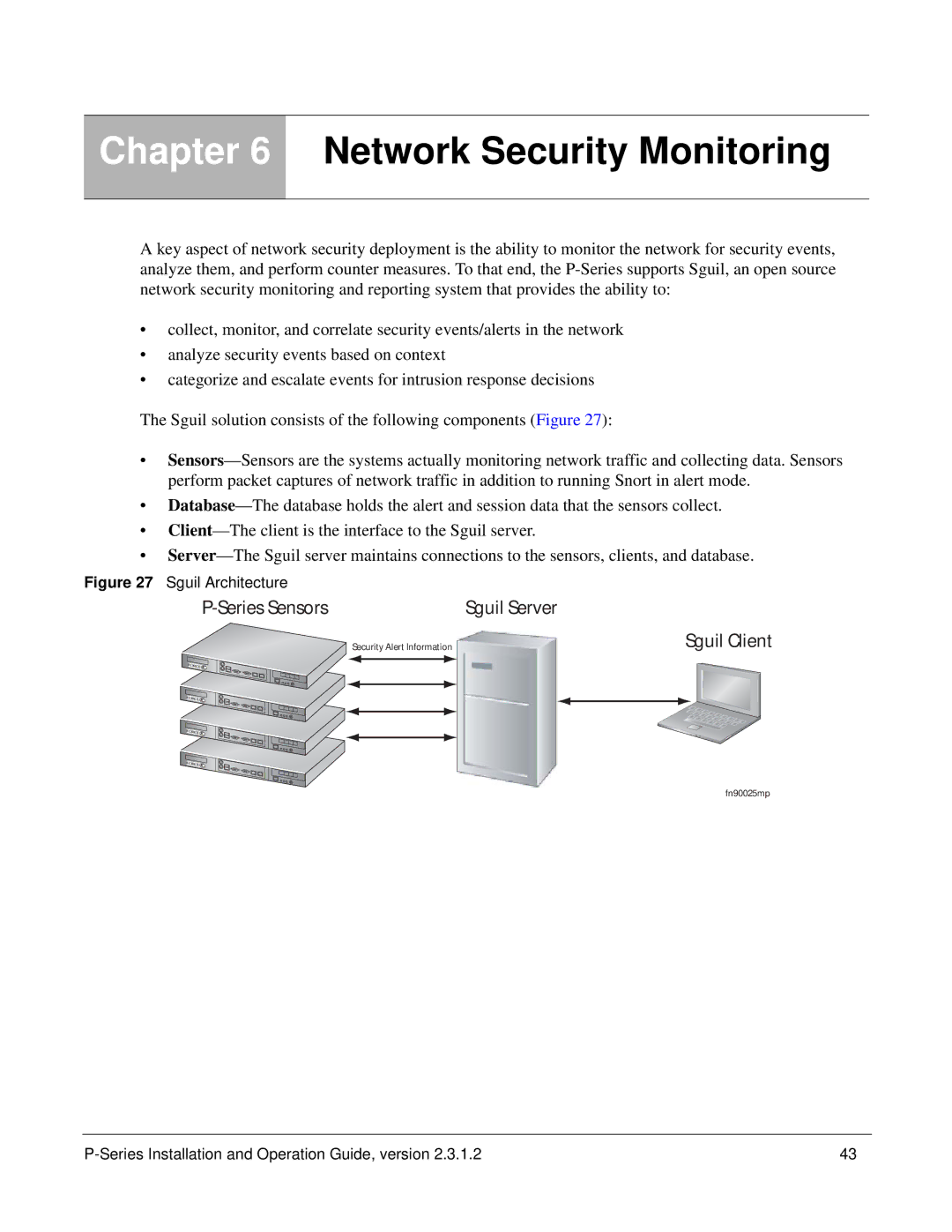
The Sguil solution consists of the following components (Figure 27):
•
•
•
•
Figure 27 Sguil Architecture
| Sguil Server | |||||||
|
| Security Alert Information |
|
| Sguil Client | |||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
fn90025mp
43 |