HP OneView 1.0 User Guide
Abstract
Acknowledgments
Contents
Understanding the security features of the appliance
Navigating the graphical user interface
Planning for configuration changes
Using the Rest APIs and other programmatic interfaces
Accessing documentation and help
II Planning tasks Planning your data center resources
Managing networks and network resources 115
An HP 3PAR Storage System 105
107
Managing enclosures and enclosure groups 131
Managing power and temperature 139
Managing users and authentication 143
Managing firmware for managed devices 135
Backing up an appliance 149
Managing the appliance 153
Monitoring power and temperature 179
About unsupported and unmanaged hardware 165
Using the State-Change Message Bus Scmb 185
VI Troubleshooting 197 199
231
Restoring an appliance from a backup file 221
Support and other resources 227
Index 293
Using the virtual appliance console 269
Backup and restore script examples 271
Part I Learning about HP OneView
Page
Architecture
Learning about HP OneView
HP OneView for converged infrastructure management
HP OneView for converged infrastructure management
Learning about HP OneView
Hardware and software provisioning features
One tool and one data set-one view
Groups, templates, and sets
Hardware and software provisioning features
Server profiles
Expert design with consistent deployment
Define configurations for specific environments
Types of groups and sets
Flexibility in design and deployment
Streamlined process for bringing hardware under management
Operating system deployment
Simplified configuration change management
Firmware and configuration change management features
Monitoring and response features
Simplified firmware management
Monitoring and response features
Automatic configuration for monitoring
Monitoring the environment and responding to issues
Isolated management network
Alert and health management
Data center environmental management
Resource utilization monitoring
Recovery from catastrophic failures
Backup and restore features
Specialized user role for creating backup files
Backup and restore features
Security features
Availability features
Rest APIs-automation and integration
Graphical and programmatic interfaces
User interface-efficiency and simplicity by design
Convenient licensing model
Integration with other HP management software
Open integration
Supported networks
Networking features
Networking features
Logical interconnects
Network sets
Resource model summary diagram
Understanding the resource model
Relationship to other resources
Server profiles
Connection templates
UI screens and Rest API resources
Connection-templates
Connections
Server hardware types
Connections and server-profiles
UI screen Rest API resource Server Hardware Types
Server hardware
Zero or more server profiles
Server-hardware-types
Server-hardware
Enclosure groups
Enclosure types
Enclosure-groups
Interconnect types
Zero or more power delivery devices
Enclosures
Exactly one enclosure group
Interconnects
Interconnect-types
Interconnects , interconnect-types ,
Logical interconnect groups
UI screen Rest API resources Interconnects
Logical-interconnects
Logical-interconnect-groups
Logical interconnects
UI screen Rest API resource Logical Interconnect Groups
Logical-downlinks
Uplink sets
UI screen Rest API resource Logical Interconnects
To a downlink
Zero or one uplink set per logical interconnect
Networks
Network sets
Uplink-sets
Network-sets
Domains
Appliance
Domains
Racks
Resources related data center facilities
Data centers
Relationship to other resources
Unmanaged devices
Power delivery devices
Power-devices
Zero or more unmanaged devices
You can view, add, or edit the properties
UI screen Rest API resource Unmanaged Devices
Unmanaged-devices
Rest APIs
Page
Securing the appliance
Understanding the security features of the appliance
Securing the appliance
Understanding the security features of the appliance
Best practices for maintaining a secure appliance
Creating a login session
Creating a login session
Authentication for appliance access
Understanding the audit log
Controlling access for authorized users
Protecting credentials
Specifying user accounts and roles
Understanding the audit log
Resource category
Message
Managing certificates from a browser
Appliance access over SSL
Example 1 Sample audit entries user login and logout
Overview
Downloading and importing a self-signed certificate
Using a certificate authority
Verifying a certificate
Managing certificates from a browser
Nonbrowser clients
Passwords
Browser best practices for a secure environment
SSL connection
Ports needed for HP OneView
Access to the appliance console
Switching from one console to another
Required ports
Algorithms for securing the appliance
Enabling or disabling authorized services access
Restricting console access
SSL see
Downloads from the appliance
Downloads from the appliance
Page
Navigating the graphical user interface
Required plug-ins and settings
Commonly used browser features and settings
Browsers
Set US or metric units of measurement
About the graphical user interface
Set the browser for US or metric units of measurement
Screen topography
About the graphical user interface
Button functions
About the Activity sidebar
Banner and main menu
UI buttons
Filters sidebar
Help sidebar
Icon descriptions
Oneviewcommunity online
Large icon Small icon Resource Activity Task Critical
Status and severity icons
User control icons
Display details
Map view screen details
Informational icons
Notifications area
Notifications area
Log out of the appliance
Search help topics
Search resources
About help system search results
Advanced searching and filtering with properties
Error Unknown Disabled
View resources according to their health status
Nameenclosure10 name192.0.2.0, PDU
Reset the health status view
View resources according to their health status
Page
Operation Http Verb Create
Using the Rest APIs and other programmatic interfaces
Resource operations
Resource data
URI format
Log in to the appliance using Rest APIs
Return codes
Resource model format
Asynchronous versus synchronous operations
Error handling
Concurrency control using etags
Task resource
Developer tools in a web browser
Querying resources using common Rest API parameters
State Change Message Bus
This user guide supplements the online help
Accessing documentation and help
Online help-conceptual and task information as you need it
Rest API help design
HP OneView documentation
Where to find HP OneView documentation
Accessing documentation and help
Downloading Html help and Rest API files
Part II Planning tasks
Page
Security planning
Planning your data center resources
How many data centers?
Determining roles and restrictions for authorized users
Determining your backup policy
Choosing a security certificate policy
Choosing a policy for the audit log
Planning your resource names
Preparing your data center network switches
Reviewing your firewall access
Resource name
Planning the appliance configuration
Appliance VM and host requirements
Separate networks for data and management
Planning for high availability
Location of the appliance
Time clocks and NTP
Page
Enclosures
Planning for configuration changes
Appliance
Interconnects and logical interconnects
Adding a network
Planning for configuration changes
Server profiles and server hardware
Adding an enclosure
Page
Part III Configuration quick starts
Page
Process overview
Quick Start Initial Configuration
Configure the environment for the first time
Process overview
Ethernet
Local authentication
Directory-based authentication
Fibre Channel
Configuration step Required action or input
Configuration step Add power devices to the appliance
Page
Process
Resource Task Description Networks Add the network
Resource Task
Server Profiles Hardware
Page
Checklist connecting a server blade to a data center network
Page
Process
Resource Task Enclosures
Server Profiles Do one Following Hardware Create a server
Resource Task Logical Create a logical Interconnect
Groups Enclosure
It to the server
Enter a name for
104
105
Attach network
Resource Task Description Networks Add the Fibre
Sets for the Direct
107
Resource Task Server Hardware Add the server using
Rest APIs for
108
Part IV Configuration and management
110
UI screens and Rest API resources
Server hardware features supported by the appliance
Managing servers and server profiles
Server-profiles and connections
Tasks for server profiles
Prerequisites for bringing server hardware under management
Roles
Effects of managing server hardware iLOs
Tasks for server hardware
Tasks for server hardware types
Tasks for server hardware
Learning more
Managing Fibre Channel networks SANs
Data center switch port requirements
Managing networks and network resources
Interconnects
Roles
Managing Ethernet networks
About network connectivity
Tasks
About network connectivity
About Fibre Channel networks
Fibre Channel network types
Fabric attach Fibre Channel networks
Direct attach Fibre Channel networks
Fibre Channel networks and FCoE
About Ethernet networks
About network sets
Ethernet networks and network sets
Network set details
Managing enclosure interconnect hardware
Managing enclosure interconnect hardware
About interconnects
Connectivity and synchronization with the appliance
Interconnects Networking features
Learning more
About unsupported interconnects
About logical interconnects
Uplink sets
Server Blade Logical Interconnect
Adding a logical interconnect
Stacking modes
Stacking health
About logical interconnect groups
Deleting a logical interconnect
About Snmp settings
Logical Interconnect Group a
Set?
Items Compliance checking Ethernet interconnect settings
Configuration defined by the logical interconnect group?
Interconnect maps
Configure a port to monitor network traffic
130
Managing enclosures and enclosure groups
Prerequisites for bringing an enclosure under management
Connectivity and synchronization with the appliance
Tasks
About enclosures
Managing enclosures and enclosure groups
About enclosure groups
About enclosure groups
Effects of managing an enclosure
134
About unsupported firmware
Managing firmware for managed devices
About the appliance firmware repository
Unsupported firmware for firmware bundles
Unsupported firmware for enclosures
Firmware update process
Roles and Tasks
Unsupported firmware for server profiles
Best practice First step Upload the latest current SPP
Best practices for firmware
Option
Troubleshooting firmware bundles
Best practice
About power delivery devices
Managing power and temperature
Managing power
Managing power and temperature
About racks
Default rack placement
Managing temperature
Default data center Datacenter
Managing temperature
About utilization graphs
About user accounts
Managing users and authentication
Reset the administrator password
Appliance role types
About user roles
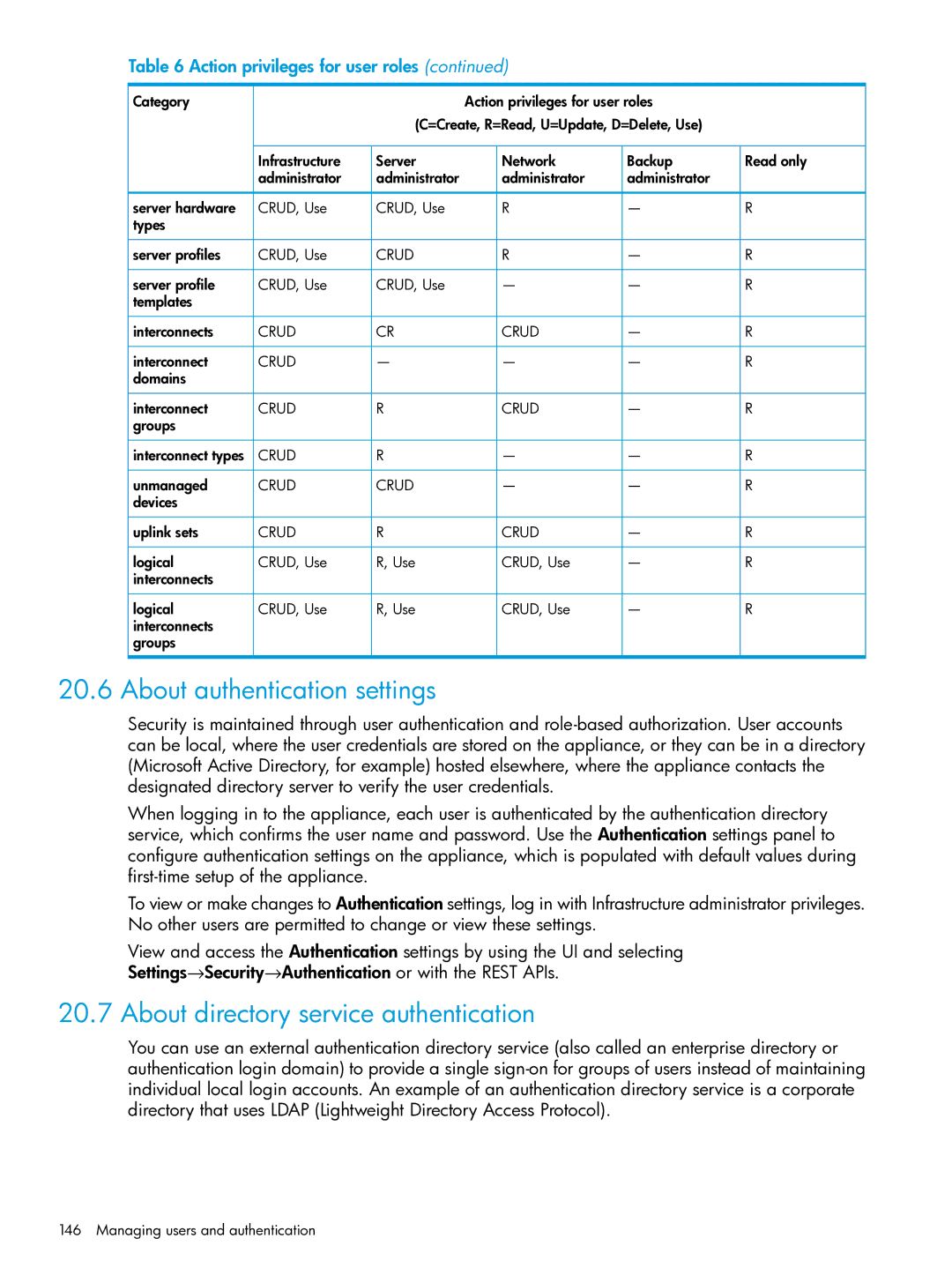
Action privileges for user roles
Action privileges for user roles
Login sessions
Administrator Backups
Global settings
Restores
About authentication settings
About directory service authentication
Managing user passwords
Managing user passwords
Reset the administrator password
Resetting the administrator password
Backups
Overview of the backup process
Backup file name
Backing up an appliance
Backing up an appliance
Guidelines for creating a backup file
Create and download a backup file
Download the backup file
Creating and downloading a backup file
Post /rest/backups
GET /rest/backups/archive/backup URI
152
Best practices for managing a VM appliance
Managing the appliance
Managing appliance availability
How the appliance handles an unexpected shutdown
Shut down the appliance
Appliance recovery operations
What to do when an appliance restarts
Restart the appliance
Restarting the appliance
Managing the appliance settings
About appliance Snmp settings
Managing addresses and ID pools
Managing the security features of the appliance
Enabling or disabling HP support access to the appliance
Id-pools
Roles
Managing SSL certificates
Managing the HP public key
Tasks
Audit-logs
Managing licenses
Downloading audit logs
Licenses
License delivery
About licensing
License types
License reporting
License graph colors
Server hardware licensing
View license status
Enclosure licensing policy behavior
Licensed features
Server blade licensing at the enclosure level
Licensing scenarios
Rack mount server licensing
Licensing and utilization statistics
Rack mount server licensing behavior
Updating the appliance
Licensing scenarios
Appliance/firmware
About unmanaged devices
About unsupported and unmanaged hardware
How the appliance handles unsupported hardware
How the appliance handles unsupported hardware
166
Part V Monitoring
168
Initial check the Dashboard
Monitoring data center status, health, and performance
Daily monitoring
Activities
Best practices for monitoring health with the appliance UI
Monitor data center temperature
Best practices for monitoring data centers
General health monitoring steps
Network health monitoring
Best practices for monitoring health using Rest APIs
Server hardware health monitoring
Overall health monitoring
GET /rest/alerts/id
Get a specific alert using the alert ID
GET /rest/alerts
Get the associated events
GET /rest/logical-interconnects/id
Managing activities
About activities
Managing activities
About tasks
Activity types alerts and tasks
About alerts
Task type Description User
Activity states
Activity statuses
About the Dashboard
Using the Dashboard screen
How to interpret the Dashboard graphs
Dashboard screen details
Disabled or Unknown
Status icons
Monitoring data center status, health, and performance
Power and temperature monitoring features by resource
Monitoring power and temperature
Power and temperature monitoring feature overview
UI power and temperature monitoring
Monitoring power and temperature
Manipulating the view of the data center visualization
About utilization graphs
Monitoring power and temperature utilization
About the Utilization panel
Utilization graphs
Enclosures Power Delivery Devices Server Hardware
Utilization statistics gathered by resource
Utilization metric Resource
Power utilization metrics
Update server hardware power capacity settings
Rest API power and temperature monitoring
Update enclosure power capacity settings
Prerequisites
Connect to the Scmb
Using the State-Change Message Bus Scmb
GET /rest/certificates/client/rabbitmq/keypair/default
Create and download the Amqp client certificate
Set up a queue to connect to the HP OneView Scmb exchange
Using the State-Change Message Bus Scmb
Json structure of message received from the Scmb
Sample queues
Example 2 Json example
NET C# code example
ChangeType values
Additional example-specific prerequisites
NET C# code example
Examples
Java code example
Java code example
Python code example
Example 5 Java code example
Example 6 Python code example pika
Python code example
Example 7 Python code example amqplib
Re-create the Amqp client certificate
Re-create the Amqp client certificate
Delete /rest/certificates/ca/rabbitmqreadonly
196
Part VI Troubleshooting
198
199
Troubleshooting
Category
About reported serious errors
Basic troubleshooting techniques
About network setup errors
Recommendation Details Look for a message
Creating a support dump file
When VM host is down or nonresponsive
Create a support dump file
Recommendation Details
Download the support dump file
Creating a support dump using Rest APIs Create support dump
Post /rest/appliance/support-dumps
GET /rest/appliance/support-dumps/file name
Appliance cannot access the network
Troubleshooting the appliance
First time setup
Unexpected appliance shutdown
Certificate action fails
Appliance update is unsuccessful
Support dump file creation action fails
Insufficient time
Backup file is incompatible
Backup file creation, download, or restore action fails
Backup file creation is still in progress
Appliance network is down
Internal server error
Profile operation was running during the backup
Restore operation fails or times out
Restart or shutdown failure
Reinstall the software
VM does not restart when VM host time is manually set
Reinstall the remote console
Clear vcmode
Troubleshooting enclosures and enclosures groups
Add or remove enclosure is unsuccessful
Restart interconnect
Restart interconnect N
Add server blade is unsuccessful
Troubleshooting firmware bundles
Certificate Error
Incorrect credentials
Troubleshooting interconnects
Troubleshooting licensing
Uplink set warnings or errors
Troubleshooting logical interconnects
27.9.1 I/O bay occupancy errors
License assigned does not match the type specified
Physical interconnect warnings and errors
Troubleshooting networks
Troubleshooting server hardware
Network create operation is unsuccessful
Cannot control power on server blade
Is claimed by that software
Troubleshooting server profiles
Troubleshooting server profiles
Server profile is not created or updated correctly
Prerequisites and conditions have not been met
Invalid configuration
What to do when you cannot apply the server profile
Server hardware or its iLO are powered-off or reset
Verify the operational status of the server hardware
Profile operations fail
Troubleshooting user accounts
Unauthenticated user or group
Incorrect privileges
User public key is not accepted
Directory service not available
Cannot add directory service
Inaccurate credentials
User or group not configured in the directory service
Cannot add server for a directory service
Lost connection with directory service host
Cannot add directory user or group
Restores
Restoring an appliance from a backup file
Restore operation overview
See also Post-restoration tasks
Preparing to restore an appliance
Restoring an appliance from a backup file
Restore an appliance from a backup file
Restore an appliance from a backup file
Restoring an appliance from a backup file
Using Rest APIs to restore an appliance from a backup file
Creating a custom script to restore an appliance
Post-restoration tasks
Preventing duplicate IDs on the network after a restore
Post-restoration tasks
226
Support and other resources
How to contact HP
Software technical support and software updates
Get connected to the HP OneView online user forum
Documentation Product websites
Using your software technical support and update service
Related information
Support and other resources
For user guides and other manuals
Submit documentation feedback
For UI and Rest API help
Docsfeedback@hp.com
230
Sample data center hardware
Tasks you can perform without data center hardware
Information about the sample data center
Tasks you can perform without data center hardware
Rack mount server
ILOAdmin
OAAdmin
Enclosure
Fibre Channel networks for the SAN fabrics
Data center networks
Fibre Channel networks
Storage system
SAN a and SAN B Fibre Channel network configurations
Switches in the data center
Production networks
Ethernet Networks
Networks for vMotion and virtual machine management
Ethernet network configuration values
Planning the configuration
Planning for installation of the appliance
Development networks
Planning for users and roles
Planning the configuration
Planning for network sets
Assumptions
Installing the appliance
Planning resource names
Workflow
Copying the template server profile to eight servers
Configuring the networks and network sets
Configuring the Fibre Channel SAN networks
Configuring the Ethernet networks
Use the following names and Vlan IDs for the test networks
Prod 1101 1102 1103 1104
Configuring the network sets
Page
Creating a logical interconnect group and its uplink sets
Creating the logical interconnect group
Creating the uplink sets for the Fibre Channel networks
Creating the uplink sets for the Ethernet networks
TestUS
ProdUS
DevUS
Creating an enclosure group for vSphere ESXi hosts
Click Create to create the logical interconnect group
Viewing the server hardware types
Enclosures Password
Adding the enclosure
172.18.1.12 Address
Editing server hardware types
Creating a server profile to use as a template
Viewing server hardware types
View information about the server hardware
Page
Secondary
Attribute Value Device type Ethernet Network
Esxi mgmt
Esxi vmotion
Requested bandwidth
Boot Not bootable
Attribute Value Device type Fibre Channel Network
Page
Esx02 Encl1, bay Esx03 Esx04 Esx05 Esx06 Esx07 Esx08
Copying the template server profile to eight servers
Name Server hardware
Creating the Flat SAN networks
172.18.1.14 Address
Page
Page
Encl2
Creating the server profile
Enclosure name
Enclosure group name
FlatSAN a
Requested bandwidth Default value FlexNIC
Device type Fibre Channel Network
FlatSAN B
Page
Assumptions
Viewing information about the server
Powering on the server
Adding the server hardware
Page
Adding a license for the server
Page
Using the virtual appliance console
Using the virtual appliance console
Using the virtual appliance console
Key combinations for the virtual appliance console
270
Sample backup script
Backup and restore script examples
Sample backup script
Sample script
Example 8 Sample backup.ps1 script
Backup and restore script examples
Sample backup script
None, does not accept piping
Sample backup script
Backup and restore script examples
Backup resource object
Absolute path of the download file
Sample backup script
Backup and restore script examples
Sample backup script
Sample restore script
Sample restore script
Example 9 Sample restore.ps1 script
Outputs the new active Api version
Response body to the upload post request
Sample restore script
Outputs the response body from the Post restore call
None, end of script upon completion or fail
Uri of the restore task in string form
Sample restore script
Backup and restore script examples
293
Host, security access, 80 initial configuration
Index
Eula
Index
Scmb see State-Change Message Bus
295
Logical interconnect, 125 State-Change Message Bus
Status icon, 62 storage system website
Vlan ID
297