ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual
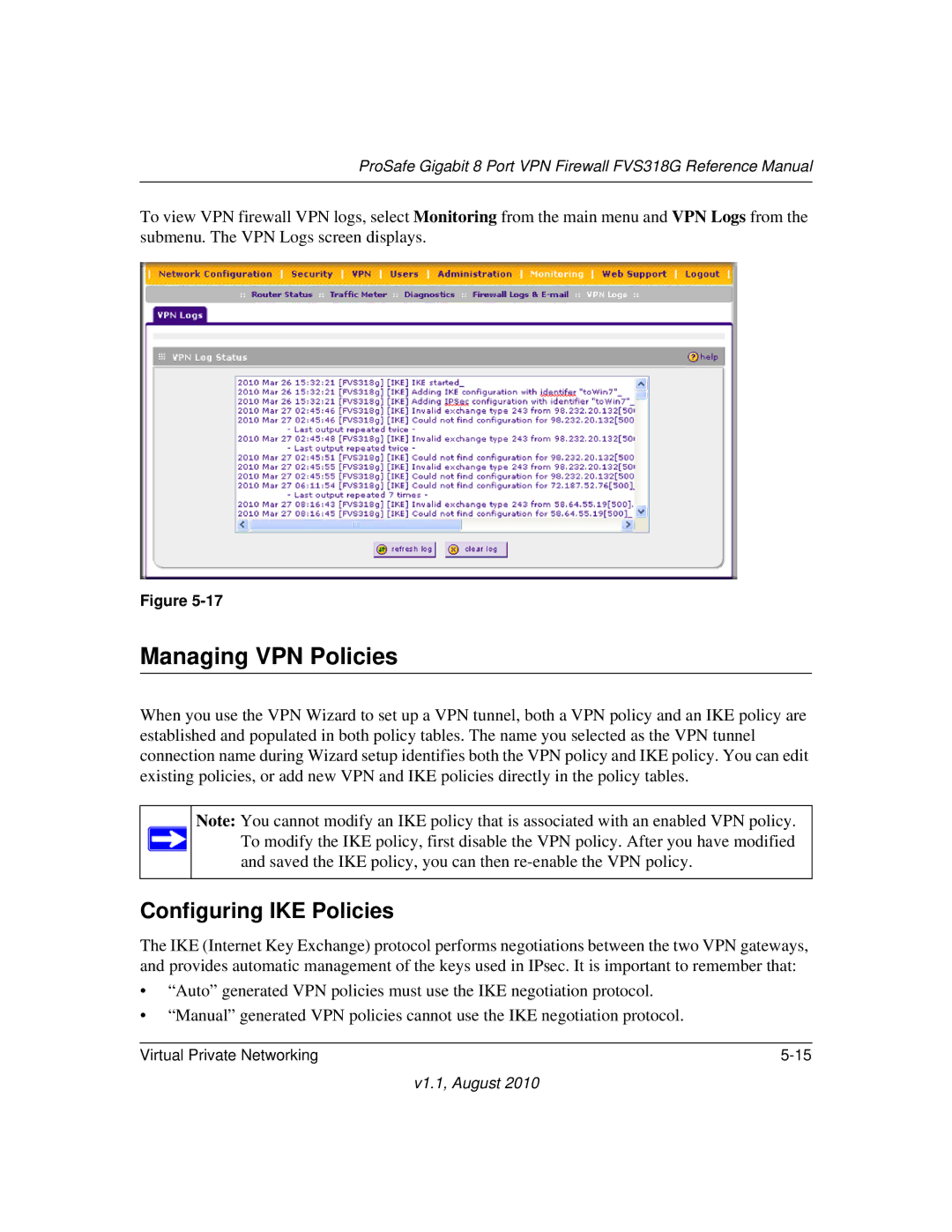
To view VPN firewall VPN logs, select Monitoring from the main menu and VPN Logs from the submenu. The VPN Logs screen displays.
Figure
Managing VPN Policies
When you use the VPN Wizard to set up a VPN tunnel, both a VPN policy and an IKE policy are established and populated in both policy tables. The name you selected as the VPN tunnel connection name during Wizard setup identifies both the VPN policy and IKE policy. You can edit existing policies, or add new VPN and IKE policies directly in the policy tables.
Note: You cannot modify an IKE policy that is associated with an enabled VPN policy. To modify the IKE policy, first disable the VPN policy. After you have modified and saved the IKE policy, you can then
Configuring IKE Policies
The IKE (Internet Key Exchange) protocol performs negotiations between the two VPN gateways, and provides automatic management of the keys used in IPsec. It is important to remember that:
•“Auto” generated VPN policies must use the IKE negotiation protocol.
•“Manual” generated VPN policies cannot use the IKE negotiation protocol.
Virtual Private Networking |