ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual
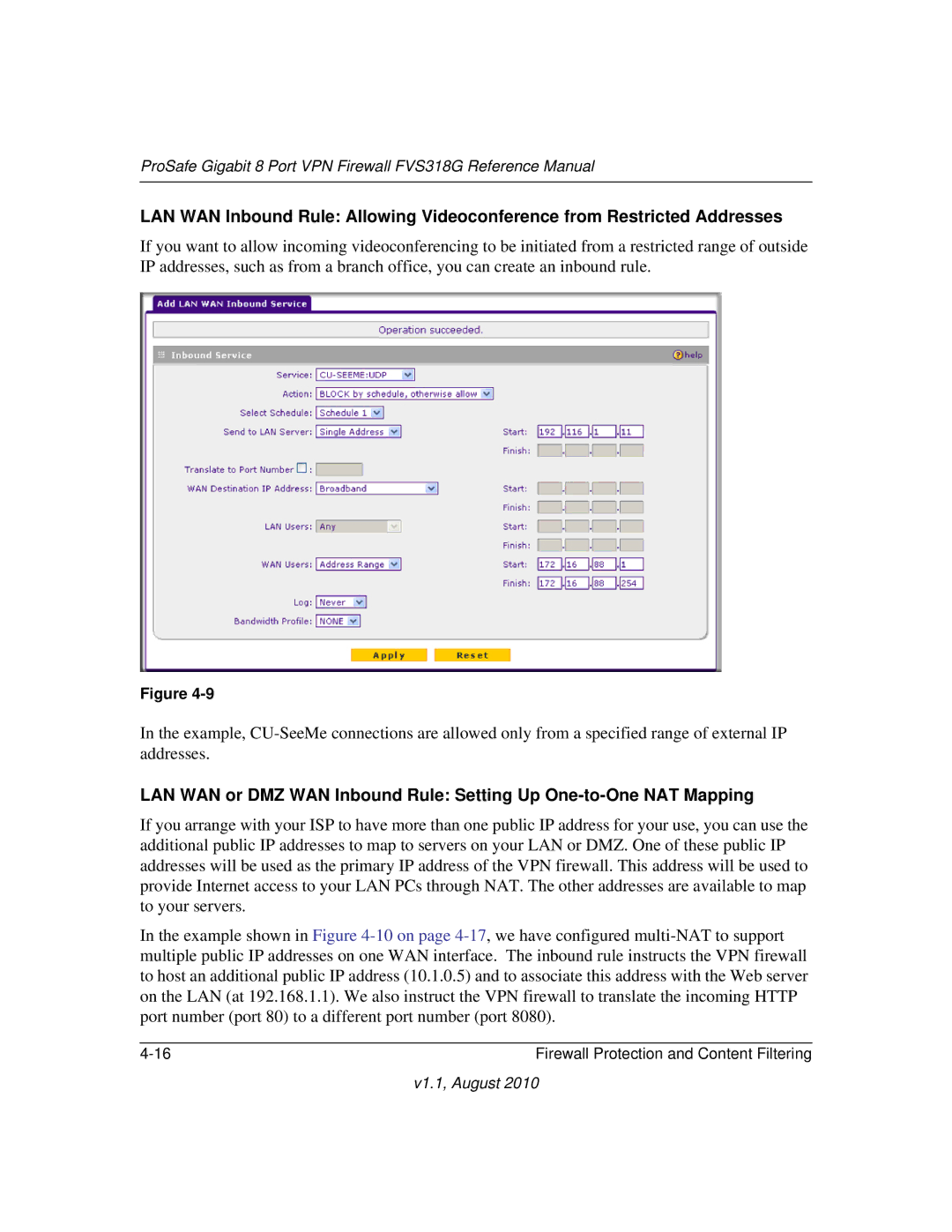
LAN WAN Inbound Rule: Allowing Videoconference from Restricted Addresses
If you want to allow incoming videoconferencing to be initiated from a restricted range of outside IP addresses, such as from a branch office, you can create an inbound rule.
Figure
In the example,
LAN WAN or DMZ WAN Inbound Rule: Setting Up
If you arrange with your ISP to have more than one public IP address for your use, you can use the additional public IP addresses to map to servers on your LAN or DMZ. One of these public IP addresses will be used as the primary IP address of the VPN firewall. This address will be used to provide Internet access to your LAN PCs through NAT. The other addresses are available to map to your servers.
In the example shown in Figure
Firewall Protection and Content Filtering |