ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual
Attack Checks
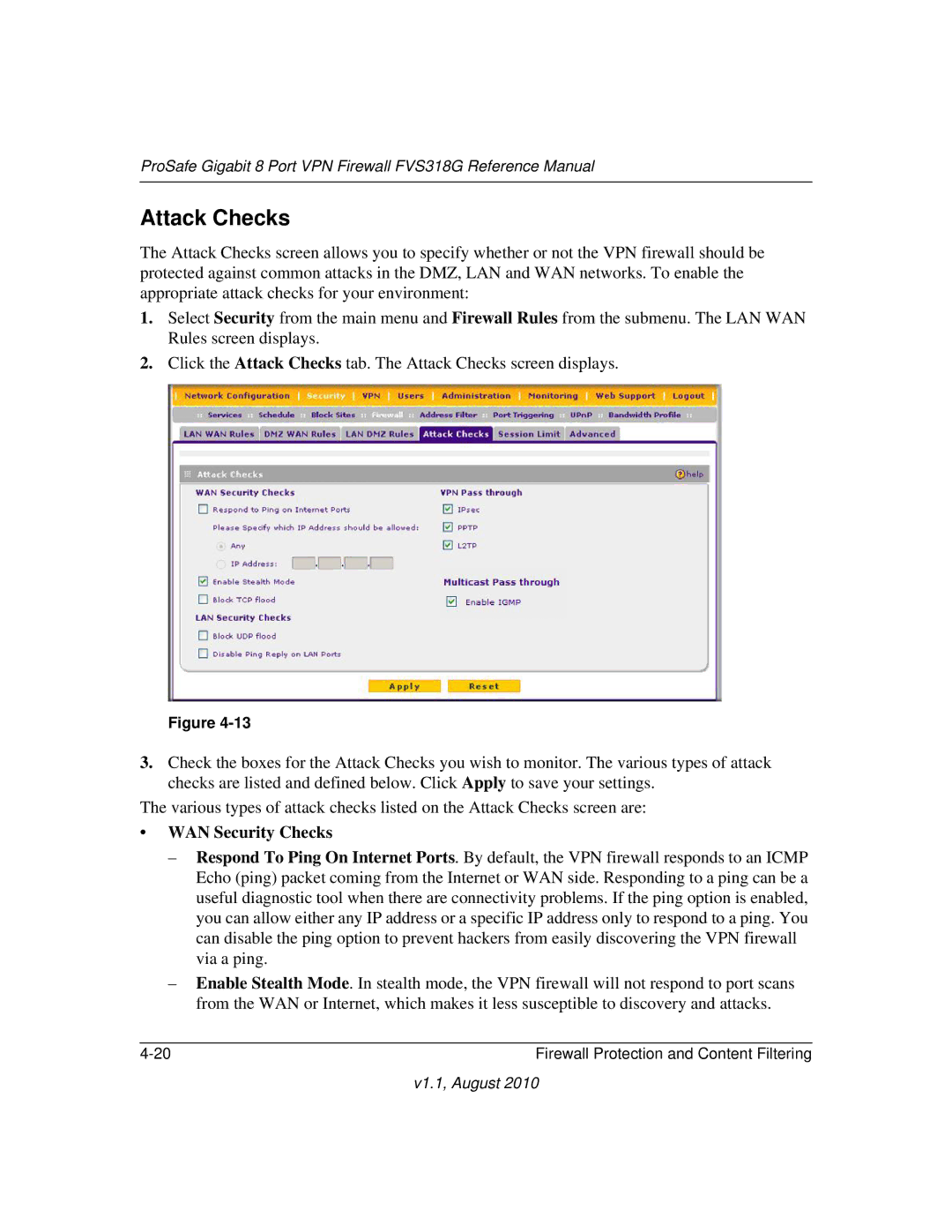
The Attack Checks screen allows you to specify whether or not the VPN firewall should be protected against common attacks in the DMZ, LAN and WAN networks. To enable the appropriate attack checks for your environment:
1.Select Security from the main menu and Firewall Rules from the submenu. The LAN WAN Rules screen displays.
2.Click the Attack Checks tab. The Attack Checks screen displays.
Figure
3.Check the boxes for the Attack Checks you wish to monitor. The various types of attack checks are listed and defined below. Click Apply to save your settings.
The various types of attack checks listed on the Attack Checks screen are:
•WAN Security Checks
–Respond To Ping On Internet Ports. By default, the VPN firewall responds to an ICMP Echo (ping) packet coming from the Internet or WAN side. Responding to a ping can be a useful diagnostic tool when there are connectivity problems. If the ping option is enabled, you can allow either any IP address or a specific IP address only to respond to a ping. You can disable the ping option to prevent hackers from easily discovering the VPN firewall via a ping.
–Enable Stealth Mode. In stealth mode, the VPN firewall will not respond to port scans from the WAN or Internet, which makes it less susceptible to discovery and attacks.
Firewall Protection and Content Filtering |