6 • Security | Model 3086 G.SHDSL Integrated Access Device User Guide |
|
|
Intrusion Detection System (IDS)
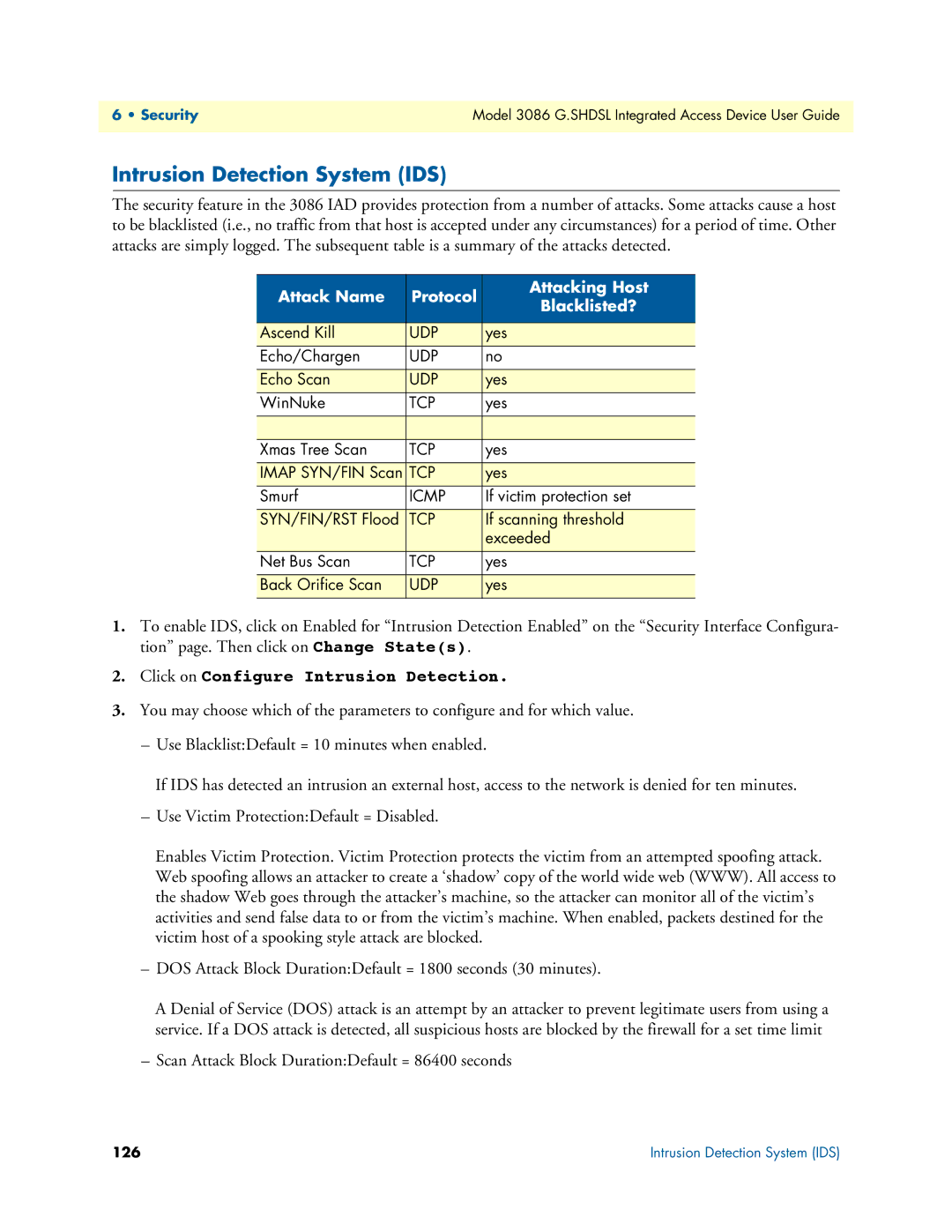
The security feature in the 3086 IAD provides protection from a number of attacks. Some attacks cause a host to be blacklisted (i.e., no traffic from that host is accepted under any circumstances) for a period of time. Other attacks are simply logged. The subsequent table is a summary of the attacks detected.
Attack Name | Protocol | Attacking Host | |
Blacklisted? | |||
|
| ||
|
|
| |
Ascend Kill | UDP | yes | |
Echo/Chargen | UDP | no | |
|
|
| |
Echo Scan | UDP | yes | |
WinNuke | TCP | yes | |
|
|
| |
|
|
| |
Xmas Tree Scan | TCP | yes | |
|
|
| |
IMAP SYN/FIN Scan | TCP | yes | |
Smurf | ICMP | If victim protection set | |
|
|
| |
SYN/FIN/RST Flood | TCP | If scanning threshold | |
|
| exceeded | |
Net Bus Scan | TCP | yes | |
|
|
| |
Back Orifice Scan | UDP | yes | |
|
|
|
1.To enable IDS, click on Enabled for “Intrusion Detection Enabled” on the “Security Interface Configura- tion” page. Then click on Change State(s).
2.Click on Configure Intrusion Detection.
3.You may choose which of the parameters to configure and for which value.
–Use Blacklist:Default = 10 minutes when enabled.
If IDS has detected an intrusion an external host, access to the network is denied for ten minutes.
–Use Victim Protection:Default = Disabled.
Enables Victim Protection. Victim Protection protects the victim from an attempted spoofing attack. Web spoofing allows an attacker to create a ‘shadow’ copy of the world wide web (WWW). All access to the shadow Web goes through the attacker’s machine, so the attacker can monitor all of the victim’s activities and send false data to or from the victim’s machine. When enabled, packets destined for the victim host of a spooking style attack are blocked.
–DOS Attack Block Duration:Default = 1800 seconds (30 minutes).
A Denial of Service (DOS) attack is an attempt by an attacker to prevent legitimate users from using a service. If a DOS attack is detected, all suspicious hosts are blocked by the firewall for a set time limit
–Scan Attack Block Duration:Default = 86400 seconds
126 | Intrusion Detection System (IDS) |