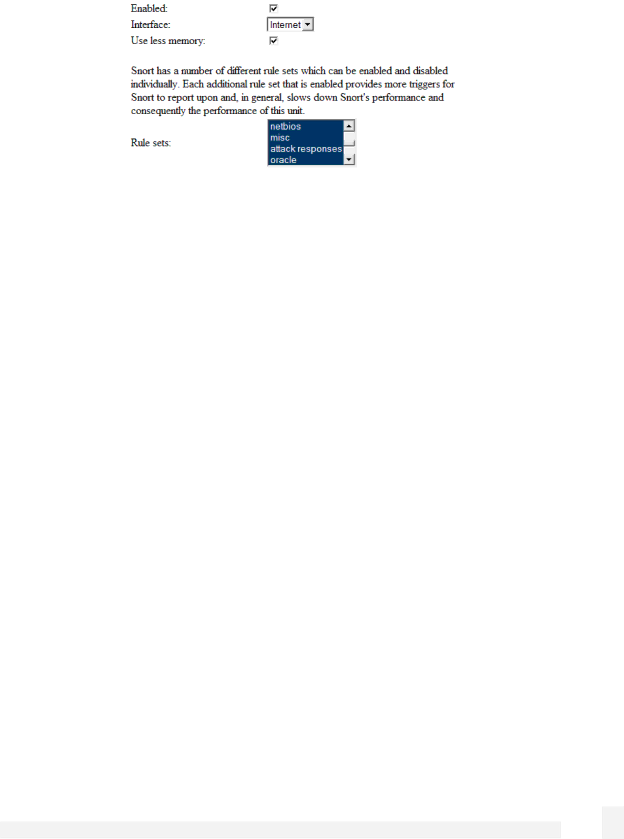
Advanced Intrusion Detection configuration
Figure
Check Enabled, and select the Interface/network port to monitor. This will typically be Internet, or possibly DMZ.
Checking Use less memory will result in slower signature detection throughput, but may be necessary if your CyberGuard SG appliance is configured to run many services or many VPN tunnels.
Next the Rule sets, of which there are more than forty, need to be selected. They are grouped by type such as DDOS, exploit, backdoor, NETBIOS, etc. Each type in turn has many subtypes depending on the exact attack signature.
For example, selecting NETBIOS will enable matching subtype signatures for NETBIOS winreg access and NETBIOS Startup Folder access attempt, etc. The subtypes or signatures themselves however are not displayed on the Web Management Console.
The full subtype signatures can be viewed at Snort web site. Included is detailed information such as signature, impact, operating systems affected, attack scenarios, ease of attack, corrective action. There are thousands of these in the Snort signature database:
94
