GE Multilin
MultiLink ML1200 Managed Field Switch
Canadian Emissions Statement
Electrical Safety requirements
Table of Contents
Access
10-3
10-1
10-5
10-19
10-7
10-12
10-13
15-5
14-9
15-1
15-4
18-3
17-14
17-16
18-1
Getting Started
Multilink ML1200 Managed Field Switch Introduction
Inspecting the Package and Product
ML1200
Order Codes
Performance
Specifications
Alarm Relay Contacts
Sinusoidal Vibration DNV To 4 G
Interrupts
ISO9001
Applicable Council Directive According to
CE Compliance Low voltage directive EN60950-1 EMC Directive
North America CULus UL60950-1 C22.2 No
Console Setup
Command Line Interface Firmware
Console Connection
Console Screen
Automatic IP Address Configuration
Logging In for the First Time
Step
Setting the IP Parameters Using Console Port
ML1200# save
Ipconfig ip=ip-address mask=subnet-mask dgw=gateway
ML1200# reboot
An example is shown below
Privilege Levels
Enable user-name
User Management
Help
Help command string
Command Enter
Command string TAB First character of the command TAB
Following example illustrates logging out from a session
Following example, the TAB key completes the command
Exiting
Logout
Example shown in the previous section, the URL is
Secure site will issue the certificate check shown below
EnerVista Secure Web Management
Make sure you use Https secure Http and not Http in the URL
Login screen
To add a user, use the add button
Select the Administration User Mgmt User Accounts menu item
Introduction
Introduction
Introduction
Modifying the Privilege Level
To exit or logout, click on the logout button
Confirm the logout by selecting OK in the pop-up window
Selecting the Proper Version
ML1200 Firmware Updates
Updating through the Command Line
Updating Multilink ML1200 Firmware
ML1200# xmodem get type=app
Https//IP address of the switch
Introduction
Introduction
Overview
Multilink ML1200 Managed Field Switch Product Description
Product Description
Product Description
Four-Port Copper Module, C1 Module Mdix
PoE power pass-through, C2 Module MDIX, 10/100Mb 4-port
Two -Port 10 Mb mm Fiber ST Modules
Two-Port Fiber Modules, 2@ 100Mb fiber
Packet Prioritization, 802.1p QOS
SFP Gigabit 1000Mbps port modules
Managed Network Firmware for Multilink ML1200-Series
Frame Buffering and Flow Control
Management Software included
Features and Benefits
Managed switching for high performance Ethernet LANs
Features Fiber-Built-In
Product Description
Applications
Example
Example
Locating Multilink ML1200 Switches
Multilink ML1200 Managed Field Switch Installation
Preparation
Fiber
Connecting Ethernet Media
Copper
Twisted Pair CAT
Twisted Pair CAT 3, 4
Gigabit SFP Small Form-factor Pluggable Optical Transceivers
HE HJ Module
H7 Module H8 HD Module
HK Module
DIN-Rail Mounting the Multilink ML1200
Mechanical Installation
Installation
Powering the Multilink ML1200 Managed Field Switch
Electrical Installation
3 ML1200 Port Module PM Installation
Ground
Pinout information for above connector
Request to Send
Transceiver Data
Switching Functionality
Multilink ML1200 Managed Field Switch Operation
Functionality
Auto-Cross Mdix and Auto-negotiation, for RJ-45 ports
Status LEDs
For Multilink ML1200 models /ML1200
Flow-control, Ieee 802.3x standard
Typical
Power Budget Calculations for ML1200 PM’s with Fiber Media
H4, HH Mb FX
2 ML1200 Modules
Multilink ML1200 Managed Field Switch Port Modules
2.2 C7 Module, 2@10Mb multi-mode FX-ST twist lock Module
CB Module, 2 Ports @100Mbps single-mode FX-SC-type, Sgl.M
CC Module, 4 @100Mb multi-mode FX , Mtrj Small-Form-factor
2.10 C1 Module Twisted Pair, 10/100Mb, 4-Port
PoE LEDs Summary
SFPs, Gigabit 1000Mbps port modules
Before Calling for Assistance
Operation
IP Address and System Information
Multilink ML1200 Managed Field Switch IP Addressing
Overview
Edit the IP address information
Importance of an IP Address
Dhcp and bootp
Bootp Database
Configuring DHCP/bootp/Manual/AUTO
Click Edit
Select the Administration System menu item
ML1200access## exit ML1200#
Using Telnet
Telnet enabledisable
ML1200access## telnet enable
Show session Kill session id=session
Select the Administration Telnet menu item
Default port for telnet is
Telnet ipaddress port=port number
ML1200# show session
For example
Setting Serial Port Parameters
Setting Parameters
System Parameters
Set timezone GMT=+ or hour=0-14 min=0-59
Date and Time
Snmp
Setvar sysnamesyscontactsyslocation =string
Set timeformat format=1224
Syntax for other date and time commands are
Following command sequence sets the daylight location
Network Time
ML1200# sntp
ML1200sntp## sync hour=5 ML1200sntp## sntp enable
ML1200sntp## exit
IP Addressing
IP Addressing
Saving and Loading Command Line
System Configuration
Config file
# Restricted Rights
System
Names, passwords
Displaying configuration
Syntax show config module=module-name
Where module-name can be
More
’show config’ command output
ML1200# show config module=snmp Hardware
Select Y. The ML1200 will prompt
Saving Configuration
Select N
Save format=v2v3
Show host command displays the host table entries
# Restricted Rights
Script File
Saving and Loading EnerVista Software
IP Addressing
Host Names
IP Addressing
Kill Config option using SWM
Erasing Configuration
IP Addressing
Lacp settings
STP, Rstp settings
Port/Tag Vlan settings
IP-Access and Host Table settings
ML1200# kill config
Introduction to IPv6
IPv6
What’s changed in IPV6?
3 IPv6 Addressing
Syntax ftp IPv6 address ftp to an IPv6 station
Configuring IPv6
Syntax ping6 IPv6 address pings an IPv6 station
Syntax show ipv6 displays the IPv6 information
Syntax telnet IPv6 address telnet to an IPv6 station
List of commands in this chapter
Description
Multilink ML1200 Managed Field Switch Access Considerations
Securing Access
Passwords
Port Security Feature
Ps enabledisable
Commands
For example, using the configure port-securitycommand
Learn port=number-list enabledisable show port-security
ML1200port-security## allow
ML1200port-security## ps enable
ML1200port-security## ps disable
Allowing MAC Addresses
Example 6-2 Enabling learning on a port
Example 6-1 Viewing the port security settings
ML1200port-security## learn port=3 enable
To deny a mac address, use the following
ML1200port-security## signal port=3 logandtrap
Save the port-security configuration use the save command
Example 6-4 Removing MAC addresses from specific ports
Access Considerations
Security Logs
Example 6-5 Configuring port security
Set logsize size=1-1000
Example 6-6 Security log commands
ML1200# show log
Removeall
Access
Show ip-access
Authorized Managers
ML1200access## exit
ML1200# access
Example 6-7 Allowing/blocking specific IP addresses
After enabling the EnerVista Secure Web Management software
Configuring Port Security with EnerVista Software
Access Considerations
Access Considerations
Logs
Authorized Managers
Access Considerations
Access Considerations
Introduction to
Multilink ML1200 Managed Field Switch Access Using Radius
2 802.1x Protocol
802.1x network components
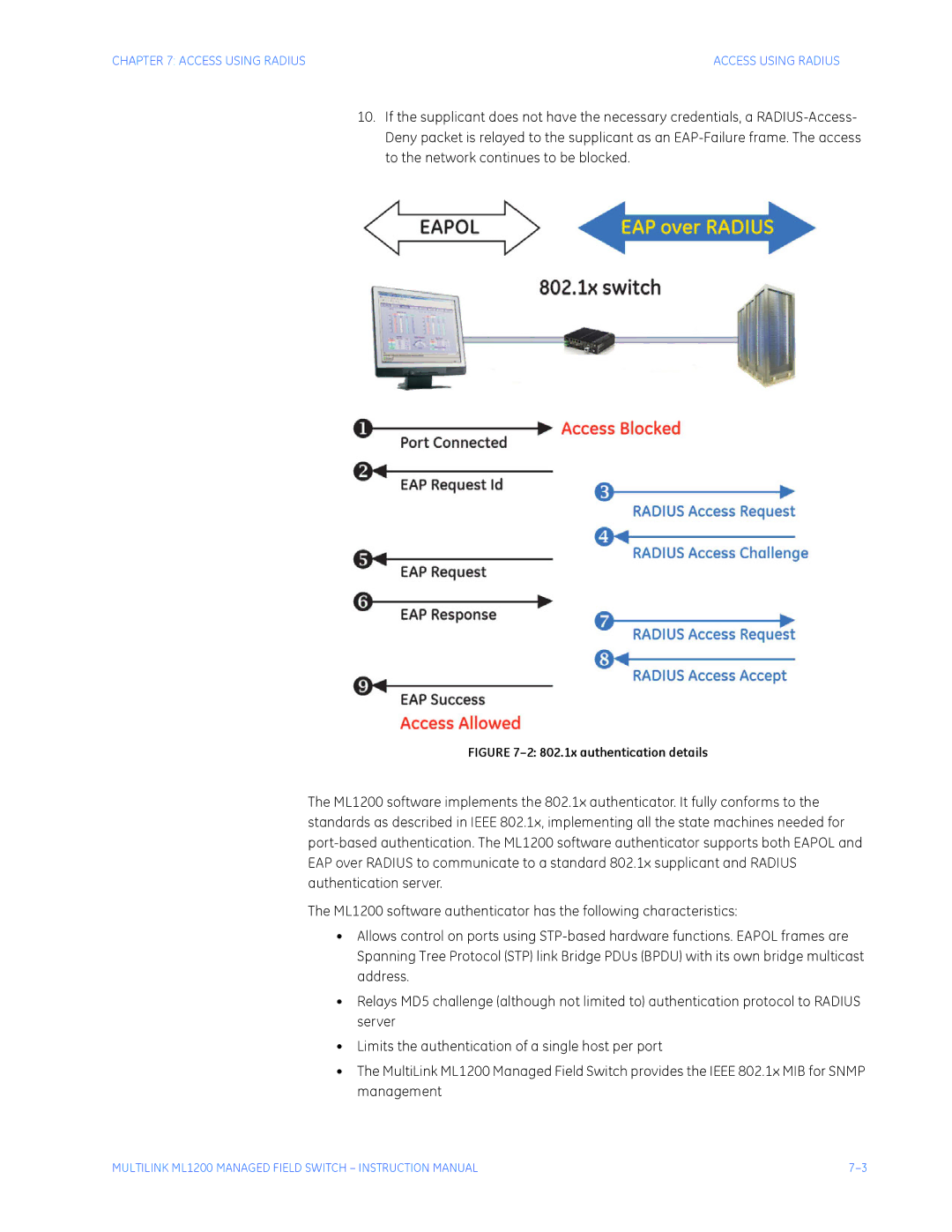
802.1x authentication details
Auth
Configuring 802.1x through the Command Line Interface
Show auth configports
Auth enabledisable
Show-stats port=num
Show-statscommand displays 802.1x related statistics
Trigger-reauthport=numlistrange
Example
Example 7-1 Setting port control parameters
On following
ML1200auth## show-port backend
Setting port control parameters
ML1200auth##
ML1200auth## shoW-port reauth
Commands
To edit the port settings, click on the edit icon
Select the Configuration Radius Port Access menu item
Access Using Radius
Access Using Radius
After all the port characteristics are enabled
Introduction to TACACS+
Multilink ML1200 Managed Field Switch Access using TACACS+
TACACS+ Packet
TACACS+ Flow
Tacacs packet format
Packet type Possible values are
Show tacplus statusservers
Configuring TACACS+ through the Command Line Interface
Tacplus enabledisable
Example 8-1 below, illustrates how to configure TACACS+
ML1200user## tacplus enable
Example 8-1 Configuring TACACS+
ML1200user## tacplus disable
Access Using TACACS+
Access Using TACACS+
Access Using TACACS+
Port Mirroring
Multilink ML1200 Managed Field Switch Port Mirroring Setup
Port-mirror
Port Mirroring using the Command Line Interface
Prtmr enabledisable
Show port-mirror
Device
Port Setup
Device command enters the device configuration mode
Setport command configures the port characteristics
ML1200device## exit ML1200#
Example 9-1 Port setup
ML1200# device
ML1200device## show port
Flowcontrol xonlimit=value xofflimit=value
Where the rxthreshold value can be from 4 to 30 default is
Flow Control
Back Pressure
ML1200device## show port=11
Back pressure and flow control
Broadcast Storms
Rate-thresholdport=portlistrange rate=frames/sec
Broadcast-protect enabledisable
Show broadcast-protect
Example 9-3 Preventing broadcast storms
Link Loss Alert
ML1200device## show port=3
Example 9-4 Link loss alert
Select the Configuration Port Mirroring menu item
Port Setup
Port Mirroring and Setup
Port Mirroring and Setup
Broadcast Storm menu
Port Mirroring and Setup
Vlan Description
Multilink ML1200 Managed Field Switch Vlan
Vlan
Tag Vlan vs. Port Vlan
Multilink ML1200 supports up to 32 VLANs per switch
10-4
Set vlan type=porttagnone
Configuring Port VLANs through the Command Line Interface
Add id=vlan Id name=vlan name port=numberlistrange
Show vlan type=porttag id=vlanid
Start vlan=namenumberlistrange
Save
Edit id=vlan Id name=vlan name port=numberlistrange
Vlan VID=1
Currently assigned Port VLANs are displayed as follows
Select the Configuration Vlan Port-Based menu item
10-9
10-10
10-11
Show-port port=portlistrange
Configuring Tag VLANs through the Command Line Interface
10-13
Example 10-1 Converting Port Vlan to Tag Vlan
ML1200tag-vlan##add id=20 name=marketing port=3-5
Converting Port Vlan to Tag Vlan
ML1200tag-vlan##set-port port=3-5 filter status=enable
Name engineering Status Active
Port Mode Status Tagged
10-19
Next step is to define the VLANs needed. To do that
Click On Configuration vlan tag-based Menu
10-21
Select the Configuration Vlan Tag-Based Tagging menu
10-23
10-24
Gvrp Concepts
Vlan Registration over Garp
Vlan Registration Over Garp
Gvrp Operations
Vlan assignment in Gvrp enabled switches
Show-vlan
Port settings for Gvrp operations
Static vlan=VID
ML1200gvrp## static vlan=10 ML1200gvrp## show-vlan
Gvrp options
Example 11-1 Converting a dynamic Vlan to a static Vlan
ML1200# gvrp ML1200gvrp## show-vlan
11-6
Show-forbid
Configuring Gvrp through the Command Line Interface
Gvrp Operation Notes
Show gvrp
Example 11-2 Configuring Gvrp
Select the Configuration Vlan Gvrp menu item
To configure Gvrp
Gvrp options on
11-10
Features and Operation
Spanning Tree Protocol STP
STP default values
Show stp configports
Configuring STP
Example 12-2 Viewing STP ports
Example 12-1 Viewing STP configuration
Show active-stp
Stp enabledisable
Stp
Set stp type=stprstp
Example 12-3 Enabling STP
Example 12-3shows how to enable STP using the above commands
Timers forward-delay=4-30 hello=1-10 age=6-40
ML1200stp##show stp ports
Example 12-4 Configuring STP parameters
Configuring STP parameters
ML1200stp##cost port=2 value=20
ML1200stp##port port=1 status=enable
Designated Root Priority 15535
Rstp concepts
Rapid Spanning Tree Protocol
Transition from STP to Rstp
13-3
Rstp
Configuring Rstp through the Command Line Interface
Rstp enabledisable
Normal Rstp
13-5
Example 13-2 Reviewing the Rstp port parameters
Forceversion stprstp
Path cost as defined in Ieee 802.1d / 802.1w
Show-forceversion
Port port=numberlistrange status=enabledisable
Show-timers
ML1200rstp##show stp config
Example 13-4 Configuring Rstp
Configuring Rstp
ML1200rstp##priority port=2 value=100
ML1200rstp##port port=1 status=disable
Romode add port=portlistrange romode del port=portlistrange
Syntax for the romode command on Rstp is shown below
ML1200rstp##romode add port=1,2
Example 13-5 Configuring smart RSTP, ring-only mode
13-15
Status Indicates whether STP or Rstp is enabled
13-17
Path cost defined in Ieee 802.1d and 802.1w
13-19
Click the Edit button to configure Rstp
Then Save Enable Status
13-22
QoS Overview
Multilink ML1200 Managed Field Switch Quality of Service
QoS Concepts
IP Precedence
DiffServ and QoS
IP Precedence ToS Field in an IP Packet Header
Qos
Configuring QoS through the Command Line Interface
Set-weightweight=0-7
Show-portweight
Set-untagport=portlistrange priority=highlow tag=0-7
Port weight settings
Show qos command displays the QoS settings
Show qos type=porttagtos port=portlistrange
Example 14-1 Configuring QoS
Following example shows how to configure QoS
Configuring QoS
ML1200qos##set-weight weight=4 ML1200qos##show-portweight
14-9
14-10
14-11
14-12
Igmp Concepts
Multilink ML1200 Managed Field Switch Igmp
Igmp
Figure below shows a network running Igmp
Isolating multicast traffic in a network
IP Multicast Filters
Igmp Support
Reserved Addresses Excluded from IP Multicast Igmp Filtering
Igmp
Configuring Igmp through the Command Line Interface
Igmp enable/disable
Show igmp command displays the Igmp status
Show-port
Show-group
Show-router
ML1200igmp## show-router
Following example shows how to configure Igmp
Example 15-1 Configuring Igmp
ML1200igmp## show-port
Configuring Igmp
ML1200igmp## mcast enable
ML1200igmp## mcast disable
15-11
15-12
Snmp Concepts
Multilink ML1200 Managed Field Switch Snmp
Snmp
SNMPv1 standards
Traps
Standards
Enterprise Traps Intruder
RFC 2271-2275 SNMPv3
Configuring Snmp through the Command Line Interface
Show-view id=id
Following example shows how to configure Snmp
Show-trap id=id#
Show-group id=id
Example 16-1 Configuring Snmp
Configuring Snmp
ML1200snmpv3## show-view id=1
ML1200snmpv3## show-group
ML1200snmpv3## show-group id=1
ML1200snmpv3## show-view
ML1200snmpv3## show-user id=2
ML1200snmpv3## show-access
ML1200snmpv3## show-access id=1
ML1200snmpv3## show-user
16-11
Multiple managers can be added as shown below
16-13
16-14
Rmon
Configuring Rmon
ML1200rmon## exit ML1200#
ML1200rmon## show rmon event
Mail
Multilink ML1200 Managed Field Switch Miscellaneous
Show smtp configrecipients
Smtp enabledisable
Smtp
Delete id=1-5
Server command configures the global Smtp server settings
Server ip=ip-addr port=1-65535 retry=0-3 domain=domain
ML1200smtp##show smtp config
Statistics
Following figure displays the port statistics for group
Optimizing serial connection in HyperTerminal
Serial Connectivity
Show history
History
Show version
Ping
Ping through the Command Line Interface
Ping through EnerVista Secure Web Management software
Prompt
Changing the Command Line Prompt
Set prompt prompt string
Example 17-2 Typical system event log
Command Line Interface Example
System Events
Following example illustrates a typical event log
EnerVista Example
Select the Configuration Statistics Log Statistics menu item
17-13
Main Commands
Command Reference
Set password sets the current user password
Set commands are listed below
Set timeout sets the system inactivity time out
Authorization commands are shown below
Configuration commands
Snmp enables or disables Snmp
Alarm commands are shown below
Vlan Registration over Garp for details
Device commands are shown below
Rapid Spanning Tree Protocol for additional details
Setqos configures QOS configuration usage
Spanning Tree Protocol STP for additional details
Passwd change the user password
17-20
Following command-line interface settings are available
Multilink ML1200 Managed Field Switch Modbus Protocol
Modbus Configuration
Command Line Interface Settings
ML1200access## show modbus
ML1200# access ML1200access## modbus enable
ML1200access## modbus port=602
Select the Configuration Access Modbus menu item
EnerVista Settings
Modbus Memory Map
Memory Mapping
Modbus memory map Sheet 1
Modbus memory map Sheet 2
Modbus memory map Sheet 3
Modbus memory map Sheet 4
Modbus memory map Sheet 5
Modbus memory map Sheet 6
Modbus memory map Sheet 7
Modbus memory map Sheet 8
Modbus memory map Sheet 9
Modbus memory map Sheet 10
Modbus memory map Sheet 11
Modbus memory map Sheet 12
Modbus memory map Sheet 13
Modbus memory map Sheet 14
Modbus memory map Sheet 15
Modbus memory map Sheet 16
Modbus memory map Sheet 17
Modbus memory map Sheet 18
Modbus memory map Sheet 19
Modbus memory map Sheet 20
Modbus memory map Sheet 21
Modbus memory map Sheet 22
Modbus memory map Sheet 23
Modbus memory map Sheet 24
Modbus memory map Sheet 25
Modbus memory map Sheet 26
Modbus memory map Sheet 27
Modbus memory map Sheet 28
Modbus memory map Sheet 29
Modbus memory map Sheet 30
Modbus memory map Sheet 31
Modbus memory map Sheet 32
Modbus memory map Sheet 33
Format Codes
18-38
Changes to the Manual
Multilink ML1200 Managed Field Switch Appendix a
Revision History
Change Notes
GE Multilin Warranty Statement
Warranty
Multilin
Power Consumption
48 V DC, 24 V DC and 125 V DC Power, Theory of Operation
Applications for DC Powered Ethernet Switches
ML1200, -48 V, 24 V, 125 V DC Installation
UL Requirements for DC-powered units
Operation
DC Power Input
Appendix C Internal DC Dual- Source Power Input
Power Supply Internal, -48VDC Dual-Source
Specifications for Multilink ML1200 Field Switch
Chapter C Internal DC DUAL-SOURCE Power Input Option
Dual-Source Option Theory of Operation
Features and Benefits of the Dual-Source Design
Installation