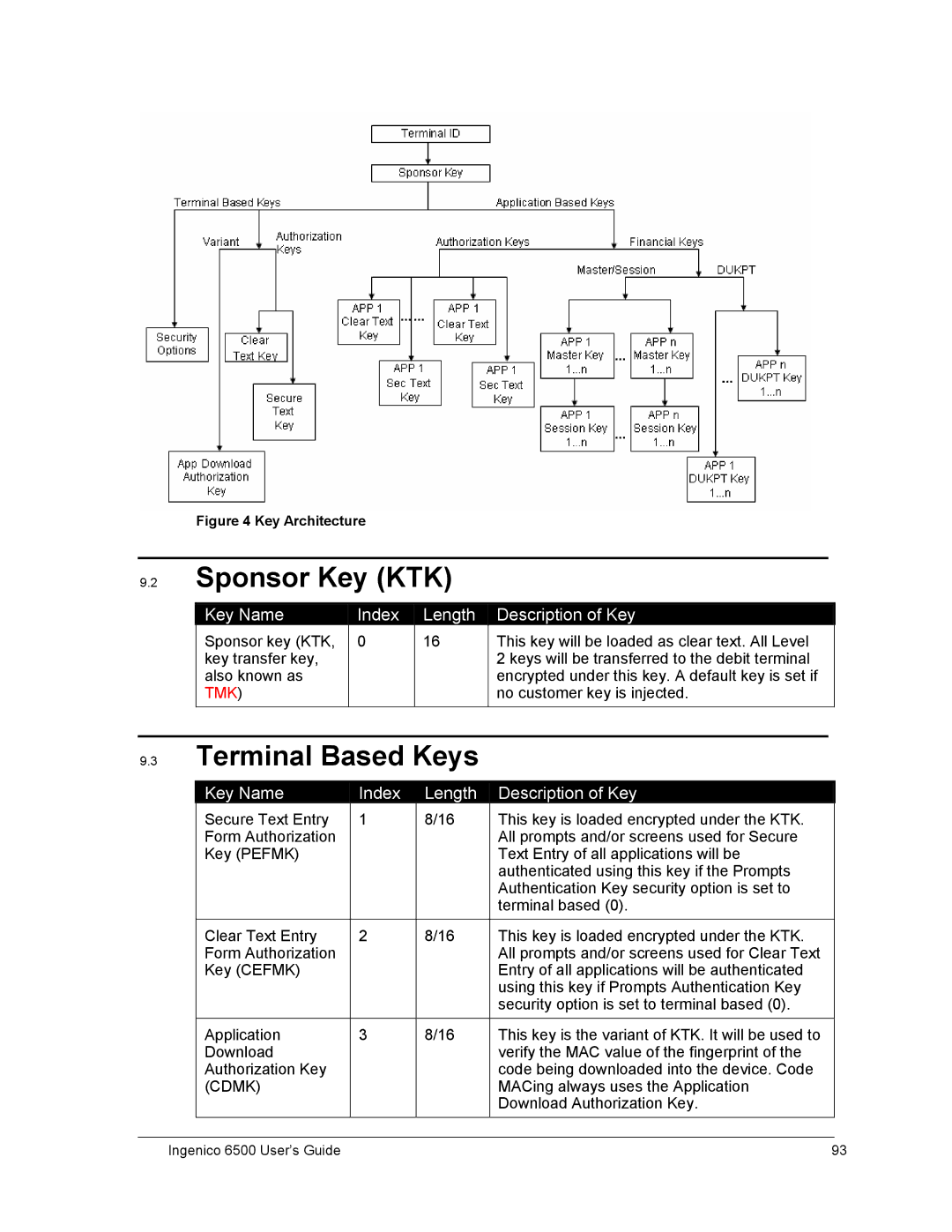
Figure 4 Key Architecture
9.2Sponsor Key (KTK)
Key Name |
|
| Index |
|
| Length |
Sponsor key (KTK, |
| 0 |
| 16 | ||
key transfer key, |
|
|
|
|
|
|
also known as |
|
|
|
|
|
|
TMK) |
|
|
|
|
|
|
|
|
|
|
|
|
|
Description of Key
This key will be loaded as clear text. All Level 2 keys will be transferred to the debit terminal encrypted under this key. A default key is set if no customer key is injected.
9.3Terminal Based Keys
| Key Name | Index | Length |
| Description of Key |
|
| Secure Text Entry | 1 | 8/16 |
| This key is loaded encrypted under the KTK. |
|
| Form Authorization |
|
|
| All prompts and/or screens used for Secure |
|
| Key (PEFMK) |
|
|
| Text Entry of all applications will be |
|
|
|
|
|
| authenticated using this key if the Prompts |
|
|
|
|
|
| Authentication Key security option is set to |
|
|
|
|
|
| terminal based (0). |
|
|
|
|
|
|
|
|
| Clear Text Entry | 2 | 8/16 |
| This key is loaded encrypted under the KTK. |
|
| Form Authorization |
|
|
| All prompts and/or screens used for Clear Text |
|
| Key (CEFMK) |
|
|
| Entry of all applications will be authenticated |
|
|
|
|
|
| using this key if Prompts Authentication Key |
|
|
|
|
|
| security option is set to terminal based (0). |
|
| Application | 3 | 8/16 |
| This key is the variant of KTK. It will be used to |
|
| Download |
|
|
| verify the MAC value of the fingerprint of the |
|
| Authorization Key |
|
|
| code being downloaded into the device. Code |
|
| (CDMK) |
|
|
| MACing always uses the Application |
|
|
|
|
|
| Download Authorization Key. |
|
|
|
|
|
|
|
|
Ingenico 6500 User’s Guide |
|
| 93 | |||