Appendix A
Advanced Security Configuration
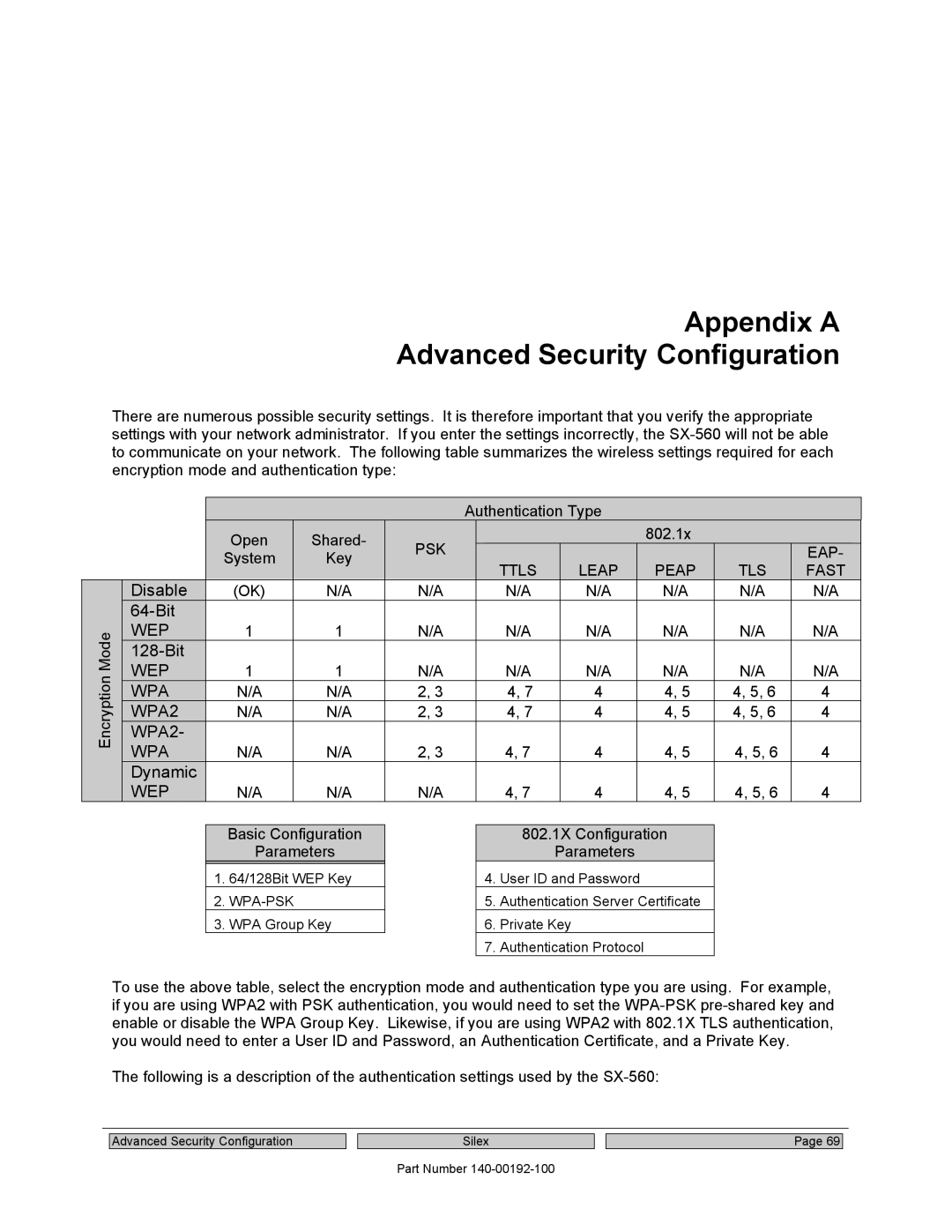
There are numerous possible security settings. It is therefore important that you verify the appropriate settings with your network administrator. If you enter the settings incorrectly, the
! | !! |
|
|
|
|
|
|
|
|
| Authentication Type! |
|
|
|
|
|
|
|
|
| |||||||
! | !! |
|
| Open |
|
| Shared- |
|
| PSK! |
|
|
|
|
|
|
|
| 802.1x! |
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| EAP- |
| |||
!! | !! |
|
| System! |
|
| Key! |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||
|
|
|
|
|
|
|
|
| TTLS! |
|
| LEAP! |
|
| PEAP! |
|
| TLS! |
|
| FAST! |
| |||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||||||||
|
| Disable! |
|
| (OK)! |
| N/A! |
| N/A! |
|
| N/A! |
| N/A! |
| N/A! |
| N/A! |
| N/A! | |||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
! |
| WEP! |
| 1! |
| 1! |
|
| N/A! |
|
| N/A! |
| N/A! |
| N/A! |
| N/A! |
| N/A ! | |||||||
Mode |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Encryption |
| WEP! |
| 1! |
| 1! |
|
| N/A! |
|
| N/A! |
| N/A! |
| N/A! |
| N/A! |
| N/A! | |||||||
| WPA! |
|
| N/A! |
| N/A! | 2, 3! |
| 4, 7! |
| 4! |
| 4, 5! |
| 4, 5, 6! |
| 4! |
| |||||||||
|
| WPA2! |
| N/A! |
| N/A! | 2, 3! |
| 4, 7 ! |
| 4! |
| 4, 5! |
| 4, 5, 6! |
| 4! |
| |||||||||
|
| WPA2- |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| WPA! |
|
| N/A! |
| N/A ! | 2, 3! |
| 4, 7 ! |
| 4! |
| 4, 5! |
| 4, 5, 6! | 4! |
| |||||||||
|
| Dynamic |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| WEP! |
|
| N/A! |
| N/A! |
| N/A ! |
| 4, 7 ! |
| 4! |
| 4, 5! |
| 4, 5, 6! | 4! |
| ||||||||
! | ! |
| ! |
| ! |
| ! | ! |
| ! |
| ! |
| ! |
| ! |
| ||||||||||
! | ! |
! | ! |
! | ! |
! | ! |
! | ! |
! | ! |
Basic Configuration
Parameters!
1.64/128Bit WEP Key!
2.
3.WPA Group Key!
!!
!!
!
!
!
!
!
!
802.1X Configuration
Parameters!
4.User ID and Password!
5.Authentication Server Certificate!
6.Private Key!
7.Authentication Protocol!
!!!
! | ! |
! | ! |
! | ! |
! | ! |
! | ! |
! | ! |
To use the above table, select the encryption mode and authentication type you are using. For example, if you are using WPA2 with PSK authentication, you would need to set the
The following is a description of the authentication settings used by the
Advanced Security Configuration
Silex
Part Number
Page 69