Cisco Unified IP Phones 7970G/7971G-GE
Page
Page
Page
N T E N T S
Products
Vii
Adding Phones with Cisco Unified CallManager Administration
Viii
Disabling a Headset
Customizing and Modifying Configuration Files
Configuring a Custom Background Image
Troubleshooting and Maintenance
Xii
Monitoring the Voice Quality of Calls
Xiii
Xiv
Audience
Overview
Xvi
Organization
Related Documentation
Cisco Unified CallManager Administration
Cisco Unified IP Phones 7970G/7971G-GE
Xvii
Obtaining Documentation
Troubleshooting
Cisco.com
Product Documentation DVD
Cisco Product Security Overview
Documentation Feedback
Ordering Documentation
Xix
For emergencies only security-alert@cisco.com
Reporting Security Problems in Cisco Products
Obtaining Technical Assistance
Product Alerts and Field Notices
Xxi
Xxii
Cisco Technical Support & Documentation Website
Definitions of Service Request Severity
Submitting a Service Request
Xxiii
Xxiv
Obtaining Additional Publications and Information
Convention Description
Document Conventions
Boldface font
Italic font
Xxvi
Italic screen font
Varoitus Tärkeitä Turvallisuusohjeita
Waarschuwing Belangrijke Veiligheidsinstructies
Xxvii
Avvertenza Importanti Istruzioni Sulla Sicurezza
Warnung Wichtige Sicherheitshinweise
Xxviii
Xxix
Aviso Instruções Importantes DE Segurança
Xxx
Varning! Viktiga Säkerhetsanvisningar
Xxxi
Xxxii
GEM Disse Anvisninger
Xxxiii
Xxxiv
An Overview of the Cisco Unified IP Phone
Cisco Unified IP Phone
Understanding the Cisco Unified IP Phones 7970G/7971G-GE
Page
OL-11524-01
Networking Protocol Purpose Usage Notes
What Networking Protocols Are Used?
Unified CallManager System Guide
Refer to the Supporting
Authentication on Cisco Unified IP
Phones section on page 1-18 for
Network Configuration section on
Related Topics
Understanding the SIP Protocol
Feature Overview
Configuring Telephony Features
Providing Users with Feature Information
Topic Reference
Understanding Security Features for Cisco Unified IP Phones
Refer to Cisco Unified CallManager Security
Guide
Topic Reference
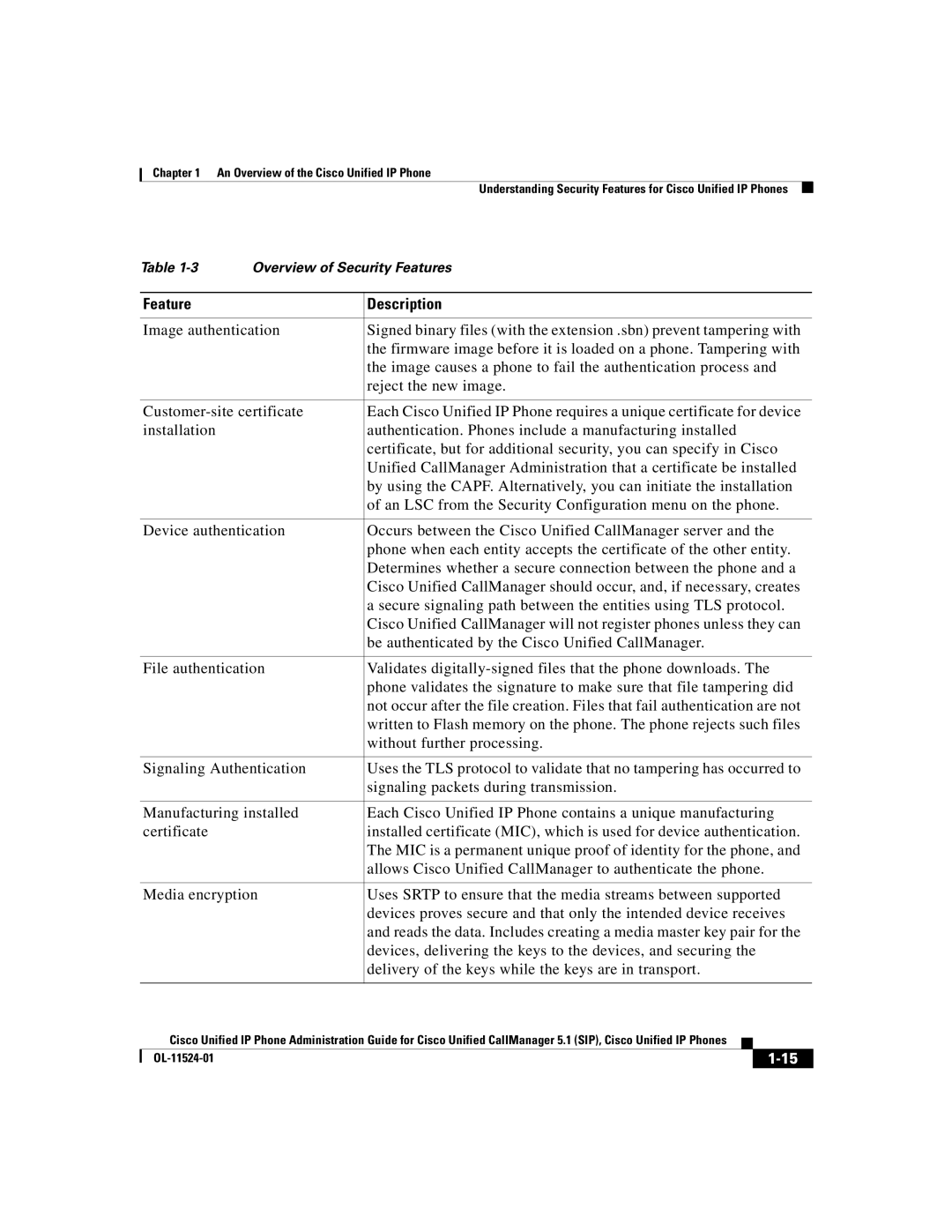
Overview of Supported Security Features
Feature Description
Authentication on Cisco Unified IP Phones section on
More information, see the Device Configuration Menu
Procedure
Identifying Encrypted and Authenticated Phone Calls
Select Security Configuration
Understanding Security Profiles
Related Topic
Supporting 802.1X Authentication on Cisco Unified IP Phones
Required Network Components
OL-11524-01
Security Restrictions
OL-11524-01
Task Purpose For More Information
CallManager Administration
CallManager System Guide
Refer to Cisco Unified
See the Setting Up Services
See the Configuring Softkey
Templates section on
See the Adding Users to
Installing Cisco Unified IP Phones
Cisco Unified CallManager
Page
See the Installing
See the Providing Power
See the Adjusting
Placement of the Cisco
IP Phone 7970 Guide
SettingsNetwork Configuration
OL-11524-01
A P T E R
OL-11524-01
Vlan
Telephony Features Available for the Phone,
Providing Power to the Phone
Phone Power Consumption and Display Brightness
Power Guidelines
Power Type Guidelines
Brightness
Obtaining Additional Information about Power
Power Outage
Understanding Phone Configuration Files
SIP Dial Rules
Understanding the Phone Startup Process
Step Description Related Topics
Security Guide
Unified CallManager
Files,
Understanding
Requires MAC Method Address?
Adding Phones to the Cisco Unified CallManager Database
Adding Phones with Auto-Registration
Adding Phones with Auto-Registration and Taps
MAC Address of a Cisco Unified IP Phone section on
Adding Phones with BAT
Using Cisco Unified IP Phones with Different Protocols
Converting a New Phone from Sccp to SIP
See the Configuring Startup Network Settings section on
Converting an In-Use Phone from Sccp to SIP
Deploying a Phone in an Sccp and SIP Environment
Converting an In-Use Phone from SIP to Sccp
Determining the MAC Address of a Cisco Unified IP Phone
Setting Up the Cisco Unified IP Phone
Before You Begin
Cisco Unified CallManager Configuration
Network Requirements
Safety
Setting Up the Cisco Unified IP Phone Before You Begin
Network and Access Ports, Handset, Speakerphone, Headset,
Network and Access Ports
Handset
Headset
Speakerphone
Http//plantronics.com
Audio Quality Subjective to the User
Using External Devices with Your Cisco Unified IP Phone
Procedure Reference
Installing the Cisco Unified IP Phone
See the Providing Power to
See the Headset section on
Ports section on page 3-5 for
See the Network and Access
130055
Adjusting Cisco Unified IP Phone Placement on the Desktop
Adjusting the Placement of the Cisco Unified IP Phone
See -2 below
Securing the Phone with a Cable Lock
Before You Begin
Mounting the Phone to the Wall
Parts Used in Wall Mounting the Cisco Unified IP Phone
Verifying the Phone Startup Process
OL-11524-01
Settings on the Cisco Unified IP Phone
Configuring Startup Network Settings
Before You Begin
From the phone, press the Settings Security Configuration
OL-11524-01
Configuring Settings on Cisco Unified IP Phone
Related Topics
Displaying a Configuration Menu
Unlocking and Locking Options
Editing Values
Category Description
Overview of Options Configurable from a Phone
Values section on
Network Configuration Menu
Option Description To Change
Refer to Cisco Unified CallManager
Security Configuration Menu section
Option Description To Change
Vlan ID
Scroll to the Dhcp Address
Option Description To Change
PC Vlan
Device Configuration Menu
State
CallManager Configuration Menu
Blank
Device Pool
Designation Description
Unified CallManager Security Guide
CallManager Security Guide
SIP General Configuration Menu, Line Settings Menu,
SIP Configuration Menu
Device Device Settings
SIP Profile
Usecallmanager
Line Settings Menu
Call Preferences Menu
This option can also be
Http Configuration Menu
URL
Configuration Menu,
Locale Configuration Menu
NTP Configuration Menu
UI Configuration Menu
Incoming call on the same line when
Administration System Enterprise
Media Configuration Menu
Parameters
Enabled or disabled for the phone. If
Whose phone has the Recording Tone
Receives. The remote party is the party
Power Save Configuration Menu
Security Configuration Menu
Ethernet Configuration Menu
Responses. Disabling the phone’s
Network Configuration
QoS Configuration Menu
WAN by storing images locally
Call Statistics Screen, Streaming Statistics,
Security Configuration Menu
List Screen section on
CTL File Screen section on
Cisco Unified CallManager Security
CTL File Screen
See the 802.1X Authentication
Status section on
Unlocking the CTL File
Configuration Menu section on
Trust List Screen
802.1X Authentication and Status
Configuration
Choose Settings Security
Authentication Device
Authentication
802.1X Authentication Real-Time Status
Configuring Features, Templates Services, and Users
Feature Description Configuration Reference
Telephony Features Available for the Phone
Features and Services Guide
Administration Guide
System Guide, Call Pickup
System Guide
CallManager Features
Cisco Unified CallManager New
Administration Guide, Call
Changed Information Guide
Release 5.11, Cisco Unified
Text, on the phone screen
DND
New and Changed Information
Features and Services Guide section
Services Guide, Presence
Administration Guide, Music
System Guide, Music on
CallManager System Guide, Cisco
Unified CallManager System
Administration Guide , Cisco
Rings section on
Creating Custom Phone
Service Application Development
Administration Guide, Time
System Guide, Time-of-Day
Refer to the Cisco Unified IP Phone
Configuring Corporate Directories and Personal Directories
Configuring Personal Directory
Configuring Corporate Directories
Modifying Phone Button Templates
Configuring Softkey Templates
Setting Up Services
Managing the User Options Web Pages
Adding Users to Cisco Unified CallManager
User Management End User
Giving Users Access to the User Options Web Pages
Customizing the Cisco Unified IP Phone
Creating Custom Phone Rings
Ringlist.xml File Format Requirements
PCM File Requirements for Custom Ring Types
Configuring a Custom Phone Ring
List.xml File Format Requirements
Creating Custom Background Images
List.xml Example
PNG File Requirements for Custom Background Images
Configuring a Custom Background Image
Configuring Wideband Headset Codec
Configuring the Idle Display
OL-11524-01
Page
Field Description
Field Description
OL-11524-01
A P T E R
CTL
Model Information Screen
Status Menu
See the Using Cisco Unified IP
Phones with Different Protocols
Select Status Messages
Status Messages Screen
Network Configuration Menu section
CallManager Administration section on
Message Description Possible Explanation and Action
Adding Phones with Cisco Unified
Unified CallManager Administration Guide
802.1X Authentication option on the phone
Settings Security Configuration
Authentication and Status section on
Address. See the Network Configuration
Message Description Possible Explanation and Action
Network Configuration Menu section on
Section on page 7-15 to verify the phone
Phone. See the Firmware Versions Screen
Device Phone
Section on page 4-7 section for details
See the Network Configuration Menu
Message Description Possible Explanation and Action
Select Network Statistics
Network Statistics Screen
PC port is in a link up state and has auto-negotiated
Select Firmware Versions
Firmware Versions Screen
Select Call Statistics
Call Statistics Screen
Monitoring the Voice Quality of Calls section on
MOS LQK
OL-11524-01
Monitoring the Cisco Unified IP Phone Remotely
Network Statistics, Device Logs, Streaming Statistics,
Accessing the Web Page for a Phone
Http//IPaddress
Disabling and Enabling Web Page Access
Choose Device Phone
Device Information
UDI
Network Configuration
Network Configuration
Description
Description
Description
Network Statistics
Ethernet Information Area Items
Description
Device Logs
Streaming Statistics
MOS LQK
Streaming Statistics
Related Topics
Page
OL-11524-01
Troubleshooting and Maintenance
Resolving Startup Problems
Troubleshooting and Maintenance Resolving Startup Problems
Identifying Error Messages
Verifying IP Addressing and Routing
Choose Tools Control Center
Cisco CallManager Serviceability
Creating a New Configuration File
Symptom Cisco Unified IP Phone Unable to Obtain IP Address
Verifying Physical Connection
Cisco Unified IP Phone Resets Unexpectedly
Identifying Intermittent Network Outages
Checking Static IP Address Settings
Verifying Dhcp Settings
Verifying Voice Vlan Configuration
Verifying that the Phones Have Not Been Intentionally Reset
Eliminating DNS or Other Connectivity Errors
Problem Possible Cause
Checking Power Connection
802.1X Enabled on Phone but Not Authenticating
802.1X Not Enabled
Summary Explanation
General Troubleshooting Tips
See the Call Statistics Screen section on page 7-16 for
Unlocking and Locking Options section on page 4-4 for
Halfduxcollisionexceedthreshold
Performing a Basic Reset, Performing a Factory Reset,
Operation Performing Explanation
Performing a Basic Reset
Locking Options section on
Unlocking and Locking Options
Performing a Factory Reset
Monitoring the Voice Quality of Calls
Using the Quality Report Tool
Using Voice Quality Metrics
Troubleshooting Tips
Condition
Where to Go for More Troubleshooting Information
Cleaning the Cisco Unified IP Phone
Providing Information to Users Via a
Website
How Users Obtain Support for the Cisco Unified IP Phone
How Users Access the Online Help System on the Phone
How Users Get Copies of Cisco Unified IP Phone Manuals
Unified CallManager section on
How Users Access a Voice Messaging System
How Users Configure Personal Directory
Click Next
Configuring the Synchronizer
OL-11524-01
P E N D I X B
Cisco Unified IP Phone
Features
CMC
Calling Features Cisco Unified IP Phone 7970G/7971G-GE
Development Notes for Release 4.13 or
Cisco IP Phone Service Application
Cisco Ipma User Guide
Cisco CallManager Attendant Console
Cisco CallManager Features and Services
User Guide
Cisco IP Phone Expansion Module
Adding Language Overlays to Phone Buttons
Supporting International Users
Installing the Cisco Unified CallManager Locale Installer
Specification Value or Range
Technical Specifications
Network and Access Port Pinouts
Cable Specifications
Access Port Connector
Network Port Connector
Pin Number Function
IN-1
Numerics
IN-2
IN-3
IN-4
IN-5
IN-6
IN-7
IN-8
IN-9
IN-10
IN-11
IN-12
IN-13
Vlan
IN-14