Software Version
Page
Contents
Configuring Logging, Alarms, and Snmp Traps
Redefining Sun Keyboard Equivalent Hot Keys
Installation
119
116
117
120
170
Configuration 167 Software Upgrade 169
Host Settings 228
171
279
277
278
281
321
Network Configuration Screens OSD 366
319
325
394
389
390
396
Glossary
Xii
Before You Begin
Audience
Document Organization
This document contains the following chapters
Typographic and Other Conventions
Related Documents
Typeface Meaning Example
Term or Convention Meaning Examples
Introduction
Chapter
Description
KVM Terminator Usage and Types
Introduction
Types of Ports
Guidelines for Using the KVM/net
Connectors on the KVM/net
Port Types Connection Information
COM port on a computer
1Port Types Connection Information Where Documented
Console
Local area network LAN
Connectors on the Back
2KVM/net Back Panel
Power Connector and Power Switch
KVM Ports
Management Ports Console, Ethernet, User 1, User
5Management Ports
Introduction
AUX Ports
Activity LEDs on the Back of the KVM/net
Ethernet Console
7LEDs on the KVM/net Management Ports
Number Label Function Color/Status
VID
AlterPath KVM/net Ordering Options
Model Number Part Numbers KVM Ports
Username Responsibilities Default Password
Types of Users
Simultaneous KVM/net Logins
8Simultaneous Administrator Login Prompt
Simultaneous Server Connections
Local Users KVM-over-IP Inband Total
Administration Options
Cyclades Web Manager
Cyclades Web Manager
Prerequisites for Using the Web Manager
TCP Ports
Task
Cascaded Devices
9Cascaded KVM Devices from a KVM/net
AlterPath
KVM Unit Management Ports Connectors KVM Expander
AlterPath KVM
KVM/net
Access Auth Type
Accessing Ports on Cascaded KVM Devices
Default Access Types
KVM/net Port Permissions
Understanding KVM Port Permissions
KVM Port Permissions Hierarchy
Tools Where Documented
Web Manager To Assign KVM Port Access to a User or Group on
Decision 1 Check User’s KVM Port Permissions
Decision 2 Check Group’s KVM Port Permissions
Decision 3 Check Generic User’s KVM Port Permissions
Decision 4 Check User’s Default Permissions
Decision 5 Check Group’s Default Permissions
Decision 6 Check Generic User’s Default Permissions
Server Access Inband and Out of Band
In-band Out-of-Band Connection Type
Source
Power
In-band Out-of-Band Supported
Computers
Server Connection Description Labels
Server Connection Description Labels In-band
KVM + In-band
Types of Access to Ports
Administering Users of Connected Servers
Tasks Related to Access to Connected Devices
Task
Redefining KVM Connection Hot Keys
Redefining Keyboard Shortcuts Hot Keys
Redefining Sun Keyboard Equivalent Hot Keys
Disabling Mouse Acceleration
Part Web Where OSD Form Manager Documented
Summary of Tasks for Redefining Hot Keys
Screen Resolution and Refresh Rate
Resolution Refresh Rates Hz
Packet Filtering on the KVM/net
15Levels of IP Filtering
Rule
Power Management
Options for Managing Power
Controlling Power While Connected to KVM Ports
Setting Up and Configuring Power Management
Task Where Documented/Notes
17Tasks KVM-connected Power Management
Security
Security Profiles
Choosing Among Authentication Methods
Authentication
Encryption
Authentication All Type Description KVM/net KVM Ports
Ldap
Uses Terminal Access Controller Access Control System
Tools for Specifying Authentication Methods
Authentication TACACS+/Local Uses local Authentication if
Lockout Macro
Operating System Lockout Macro
Select Lock Screen and enter the desired
Go to Launch Preferences Desktop
Preference Keyboard Shortcuts
Hot key sequence, for example, Ctrl+Alt +
Regional & Accessibility Keyboard
Default key sequence is Ctrl+Alt +L
Default key sequence
Scroll down to Desktop to see the default
Notifications, Alarms, and Data Buffering
Shortcut Key
Prerequisites for Logging to Syslog Servers
Example of Using Facility Numbers
Syslog Servers
Facility Numbers for Syslog Messages
Configuring Logging, Alarms, and Snmp Traps
Snmp Traps
VPN and the KVM/net
Considerations When Choosing Whether to Enable Dhcp
Server Type Connection KVM Terminator Model Part Number
KVM Terminator Usage and Types
Activity LEDs on the Terminator
VGA and PS/2 ports APK4615 PC / Sun VGA and USB ports
KVM Expander Features
KVM Expander
KVM Expander Models and Components
ATP4208 ATP4216
11KVM Expander Back Panel Components
KVM/net They allow the connection of a CAT 5 cable to a
Ports on the KVM Expander
Port Type Use and Connection Information
Terminator, which is connected to a server
Power Outlets on the KVM Expander
LEDs on the KVM Expander
Cascading a KVM Expander
14Connecting a KVM Expander to the KVM/net
KVM Unit Model Number KVM Expander Maximum Servers
AlterPath KVM KVM Expander 512
Upgrading the Microcontroller Code
15Devices Form on KVM/net Web Manager
User Access
AlterPath KVM RP
Connectors on the Back of the KVM RP
17 KVM RP Front
Port Type Use and Connection Information
Installation
Page
Shipping Box Contents KVM/net
Description Purpose
Setting Up the KVM/net
To Mount the KVM/net
Use a Phillips screwdriver to tighten the screws
Making an Ethernet Connection
To Make an Ethernet Connection
Connecting Servers to the KVM Ports
2Connecting Servers to KVM Ports
To Prepare to Connect Servers to the KVM/net
To Connect Computers to KVM Ports
Installation
Making a Direct Connection for Network Configuration
To Connect to the Console Port
Powering On the KVM/net and Connected Devices
To Connect to the User 1 Management Port
To Power On the KVM/net
Performing Basic Network Configuration
To Power On Connected Devices
To Change the Password Through the Console
Configuring Basic Networking Using the wiz Command
To Log in to the KVM/net Through the Console
To Use the wiz Command to Configure Network Parameters
Enter the IP address for the gateway
Enter the netmask for the subnetwork
Enter y to save the changes
Configuring Basic Networking Using the OSD
Action OSD Equivalent
To Log into the OSD
To Change a Password Using the OSD
To Configure Network Parameters Using the OSD
Installation
Performing Basic Network Configuration
Installation
To Set the Time and Date Using the OSD
Installation
Completing Configuration Using the Web Manager
Changing the Root Password Command Line
Changing Default Passwords
Changing admin’s Default Password Web Manager
Password cyclades Enter the passwd command
Save the new password by entering the saveconf command
Changing Default Passwords OSD
Log out
To Use the Default IP Address to Access the Web Manager
To Use a Dynamic IP Address to Access the Web Manager
Inet addr192.168.50.72 Bcast192.168.51.255 Mask255.255.252.0
Preconfiguring the KVM/net for Remote Installation
To Preconfigure the KVM/net
Task Where Documented
Additional Configuration Tasks
To Set Up a Preconfigured KVM/net
See the following sections for other procedures
To Disable Mouse Acceleration Windows XP/Windows
To Disable Mouse Acceleration Windows
To Disable Mouse Acceleration Windows ME
To Disable Mouse Acceleration Windows 95/ 98/NT
To Disable Mouse Acceleration Linux
Exit the AlterPath Viewer
Modify IE Security Settings
Required Security Settings For Internet Explorer
To Modify Trusted Sites Settings
Click the Sites button to open the Trusted sites dialog box
To Modify Internet or Local Intranet Zone Settings
Download signed ActiveX controls
Installation 113
114
Advanced Installation Procedures
Connecting an External Modem
To Connect an External Modem to the AUX Port
Connecting AlterPath PMs to the KVM/net
To Connect an AlterPath PM to the AUX Port
To Connect Multiple PMs to the KVM/net
Installing the AlterPath KVM Expander
Shipping Box Contents KVM Expander
Setting Up the KVM Expander
To Mount the KVM Expander
Advanced Installation Procedures 123
Powering On the KVM Expander and Connected Devices
To Power On the KVM Expander
To Power On KVM-connected Devices
Connecting Cascaded KVM Units to the Primary KVM/net
To Connect a Secondary KVM Unit to the Primary KVM/net
To Connect a KVM Expander to the Primary KVM/net
Installing the AlterPath KVM RP
Tasks
Shipping Box Contents AlterPath KVM RP
Options for Accessing the KVM RP
To Connect the KVM RP to the KVM/net
To Power On the KVM RP
Supplying Power to the KVM RP
To Connect the KVM RP to the Local Work Station
Web Manager for Administrators
Administrative Modes Wizard Mode Expert Mode
Common Tasks
Web Manager for Administrators 135
Common Features of Administrators’ Windows
Button Name Use
Logging In to the Web Manager and Saving Changes
Obtaining More Information
Window Area Purpose
To Log In to the Web Manager as Admin
IPaddress/login.asp?portname=portnumber
To Save Configuration Changes
Administrative Modes
Wizard Mode
Procedures in Wizard Mode
2Example Window in Wizard Mode
Security Profile Wizard
Steps in Wizard Mode Wizard
Pre-defined Security Profiles
Custom Security Profile
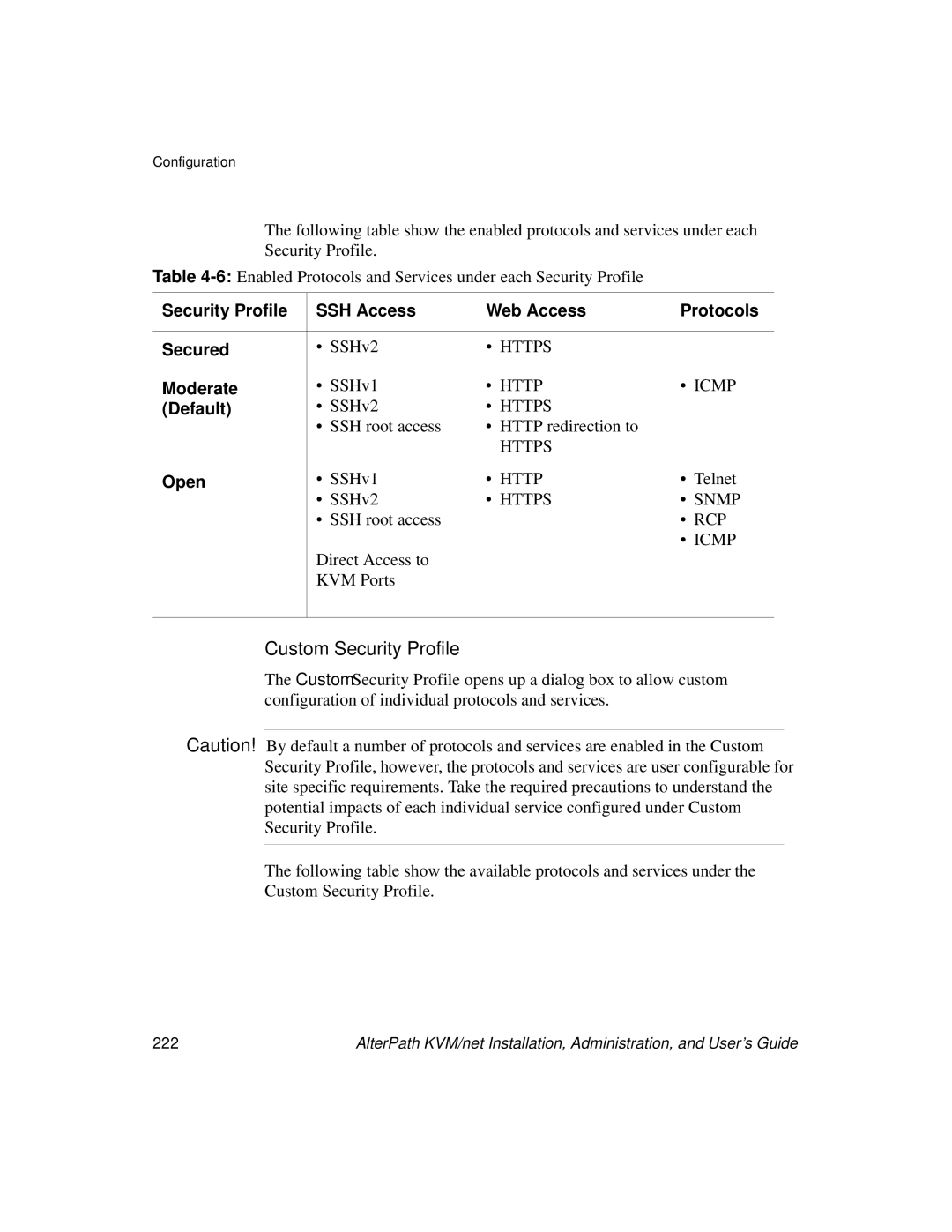
Security Profile SSH Access Web Access Protocols Secured
Default
Moderate
Security Profile SSH Access Web Access Protocols Custom
To Select or Configure a Security Profile Wizard
SSH Options SSH Http Options
3Security Advisory Dialog Box
4Security Profile in Wizard Mode
5Custom Security Profile Dialog Box
Network Settings Wizard
3Configuring KVM/net in Expert Mode
To Change Network Settings Wizard
Access Wizard
6Network Settings in Wizard Mode
7User Access in Wizard Mode
To Add a User Wizard
Field Name Definition
Wizard mode, go to Access. The Access form appears
To Change a Password Wizard
To Delete a User Wizard
156
8System Log in Wizard Mode
System Log Wizard
To Add a Syslog Server Wizard
Expert Mode
To Delete a Syslog Server Wizard
Access
10Access Form in Expert Mode
Ipdu Power Management
Connect to Server
Outlets Manager
To View Status, Lock, Unlock, Rename, or Cycle Power Outlets
View IPDUs Info
To View and Reset Ipdu Information
Users Manager
To Configure Users to Manage Specific Power Outlets
Configuration
To Configure Creation of Alarms and Syslog Files for IPDUs
To Specify or Change the Alias of an Ipdu
Software Upgrade
Configuration
To Upgrade Firmware on an AlterPath PM
KVM
Web Manager Form Where Documented
General
Parameter Name Definition
To Enable Direct Access to KVM Ports
Enabling Direct Access to KVM Ports
Redefining KVM Connection Keyboard Shortcuts Hot Keys
Defaults
Common Command Key Where Defined Escape Sequence Format
ConfigurationKVMGeneral
To Redefine KVM Session Keyboard Shortcuts
Redefining Sun Keyboard Modifier Keys
Specifying Authentication for KVM Port Logins
To Redefine the Sun Keyboard Modifier Keys
Local Users and IP Users
18KVM Configuration User 1/User 2/IP Users Form
Value is 60 minutes. a value of 0 disables the idle timeout
Sets the maximum time in minutes for the session to be idle
IP Users only. The default is 5900+. You may need to change
To Configure Local User 1 and User 2 Sessions
More details, see TCP Ports on page 20. Port numbers
To Configure IP User KVM Over IP Sessions Expert
Web Manager for Administrators 181
19KVM Device Configuration Form
Devices
Configuring Individual KVM Ports
To Configure a KVM Port for Power Management
184
Web Manager for Administrators 185
To Enable or Disable a KVM Port
To Specify or Change the Alias for a KVM Port
Configuring Cascaded KVM Units
188
To Edit the Configuration of a Cascaded KVM Unit
190
To Delete the Configuration of a Cascaded KVM Unit
Users & Groups
20KVM Users & Groups Configuration Form
To Add a User Expert
Name of the user to be added
Password associated with the user name
For more details
To Add a Group
To Change a User’s Password Expert
To Delete a User or Group Expert
Click OK Click apply changes
To Select Users and Groups for Assigning KVM Port Access
To Modify a Group
To Assign KVM Port Access to a User or Group
Web Manager for Administrators 197
198
Configuring Inband RDP Servers
21Inband Configuration Form
Prerequisites for Inband Access to RDP Servers
To Add or Modify an inband RDP Server
202
Web Manager for Administrators 203
To Delete an inband RDP Server
Security
Configuring an Authentication Method
To Configure an Authentication Method for KVM/net Logins
23KVM Unit Authentication Configuration Form
To Configure an Authentication Method for KVM Port Logins
NIS, Local/NIS, NIS/Local, or NIS
Method Variations Procedures
To Configure an NIS Authentication Server on
DownLocal
Group Authorization
To Identify a Kerberos Authentication Server
210
24Kerberos Server Authentication Form
To Identify an Ldap Authentication Server
25LDAP Server Authentication Form
To Configure an Smbntlm Authentication Server
To Configure Group Authorization on a Ldap Server
To Configure Group Authorization on a Ntlm Server
Configuring Active Directory Schema
To Configure an NIS Authentication Server
To Identify a Radius Authentication Server
27NIS Server Authentication Form
To Configure Group Authorization on a Radius Server
28Radius Server Authentication Form
To Identify a TACACS+ Authentication Server
29Tacacs+ Server Authentication Form
Group Authorization on TACACS+
To Configure Group Authorization on a TACACS+ Server
222
To Select or Configure a Security Profile Expert
30Security Profiles Configuration Form Expert
31Custom Security Profile Dialog Box
8Configuring KVM/net in Expert Mode Security
Form Use this form to Where Documented
Network configuration comprises eight forms
Network
VPN
Host Settings
To Configure Host Settings Expert
DNS Service
Ethernet Port
Gateway numeric identification
Name that identifies the domain for
Example, domainname.com
Number
33Syslog Configuration Form
Syslog
232
IP Filtering
Add Rule and Edit Rule Options
Inverted Check Boxes
Source or Destination IP and Mask
Destination Port
Field/Menu Option Definition Source Port
TCP Flags
Source Port or Destination Port field
Field Definition Source Port
Specify a source or destination port number for filtering
Source Port field. If you specify a second number in the to
Output Interface
Field Definition Input Interface
Fragments
Field or Menu Name Definition
To Add a Chain
To Edit a Chain
To Edit a Rule for IP Filtering
To Add a Packet Filtering Rule
To Add a Chain for IP Filtering
To Edit a Chain for IP Filtering
To Add a Rule for IP Filtering
Web Manager for Administrators 245
Indicates the action to be performed to
IP packet when it matches the rule. For
Source network mask. Required when a
Example, the kernel can Accept Drop
Destination IP to invert the target action
Destination network mask
Select the check box adjacent to
For example, the action assigned to
Invert the target action. For example,
On the type of error message such as, alert
Select box adjacent to Output Interface to
Action assigned to the target will be
Check box to include TCP options in the log
Prefix that will identify the log
Check box to include TCP sequence
Check box to include IP options in the log
To Configure VPN
VPN
Web Manager for Administrators 251
Any descriptive name you want to use to
Edit or complete the appropriate fields as follows
Identify this connection such as
Field Name
Boot action configured for the host, either
Ignore, Add, Start
To Configure Snmp
Enter the following system information, as necessary
Community name acts as a password to
Authenticate messages sent between an
Snmp client and a router containing an
Example, mydomain
Authenticate messages sent between an Snmp
Physical location of the system for
Client and a router containing an Snmp server
Object Identifier
Notifications
To Configure Snmp Traps
260
Define the event you want to trigger a
Field Name Description
Notification for
To Configure Hosts
Host Tables
36Host Tables Configuration Form
Static Routes
To Add, Edit, or Delete a Static Route
12Add/Modify Static Routes Fields
AUX Port
Number of hops
13PPP Fields for Configuring the AUX Port
System
Time/Date
To Set the KVM/net’s Date and Time Manually
To Set The Time and Date With NTP
Setting up Customized Timezone Configuration
Using the Custom Option to Set Daylight Savings Time
Creating a Custom Timezone Selection
Boot Configuration
42System Boot Configuration Form
Field or Value Name Description
New IP address for the KVM/net
Speed of the Ethernet connection. Select
Appropriate Ethernet setting if you need to
Change the Auto Negotiation default value
100BaseT Half-Duplex
To Configure KVM/net Boot
To Configure the Online Help Path
Online Help
Viewing System Information
General
To View General Information for Your KVM/net
Station Status
Field
To View Station Status
Information
Management
Field Information
Menu Selection Use this menu to
Configuration data
Use a FTP server to save or retrieve your
Reboot the system
Backup Configuration
Reset or kill sessions
View the status of all active sessions as well as
Field Definition
Such as KVM8802config040406 in a directory called upload
IP address of the FTP server
To Back Up or Retrieve KVM/net Configuration Data
286
Firmware Upgrade
48Firmware Upgrade
FTP Site
Password
Field/Menu Definition Name Type
Username
ZImagekvm200.bin ZImagekvm200.bin.md5
To Upgrade Firmware
Microcode Upgrade
IP modules
Target Name Used on Form Filename Format Component
Modules
FTP Server
Field Name Definition Target
Directory
To Download Microcode From an FTP Server
Microcode Reset
To Reset the Microcode After Upgrade
Web Manager for Administrators 295
Column Definition
Active Sessions
To View Active Sessions Information
Name of the KVM port
To Kill an Active Session
Reboot
To Reboot the KVM/net From a Remote Location
Web Manager for Regular Users
Web Manager for Regular Users
1Example of Regular User Web Manager Form
Prerequisites for Logging in to the Web Manager
To Log Into the KVM/net Web Manager as a Regular User
Web Manager for Regular Users 303
Ipdu Power Management
Connect to Server
See Controlling Power of a KVM-connected Server on
Changing Your KVM/net Password
To Change Your KVM/net Password
Accessing Connected Devices
308
Who Can Access Connected Devices
Server Connections What You See
Viewing KVM Connections
1AlterPath Viewer for KVM Connections
312
Viewing In-band Connections
2ActiveX Viewer for In-band Connections
Prerequisites for Accessing Servers With KVM Connections
1Supported Screen Resolutions and Refresh Rates
Web Manager Login Screen
Conditions
Accessing Connected Devices 317
Login Screen Direct Logins Not Enabled
Connect to Server Drop-down List
Accessing Connected Devices 319
Login Screen Direct Logins Enabled, Only IP Address Entered
Connecting to Servers Remotely Through the Web Manager
322
Accessing Connected Devices 323
IPaddress/login.asp?portname=portnumber
Connecting to Servers Locally Through the OSD
To Connect to Servers Through the OSD Connection Menu
Accessing Connected Devices 327
Controlling KVM Port Connections
Hot Keys for KVM Connections
Key Combination Action
Win Function Key Sun Key
Hot Keys for Emulating Sun Keyboard Keys
Numeric Keypad
To Return to the Connection Menu After Connecting to a Port
To View Connected Port Information
Cycling Between Servers
To Initiate Cycle by Server
To Adjust Screen Brightness and Cable Length
Default is Ctrl+k q
Resetting the Keyboard and Mouse
To Reset the Keyboard and Mouse
Controlling Power of a KVM-connected Server
To Power On, Power Off, or Reboot the Connected Server
To Close a KVM Connection
Closing a KVM Connection
Sharing KVM Port Connections
Quit this session Connect read only
Connect read write Kill other session
Recommended Settings
AlterPath Viewer Settings
Menu Select the following options
Options Menu
Menu Selection Description
Vertical Offset
Setting the Viewer Options
Field or Menu Item Function Horizontal Offset
Quality ----Speed
Connection Menu
High Color
Menu Selection Function Encryption Type
No Encryption
Low Color
344
Accessing Connected Devices 345
7Tasks for Configuring and Making Dial Up Connections User
Modem Connections
To Configure a PPP Connection on a Remote Computer
To Make a PPP Connection From a Remote Computer
Accessing Connected Devices 349
350
On Screen Display
Basic Navigation Keys
Navigating the OSD
Key Action
Tab to the OK button and press the Enter key
Logging In Through the OSD
Common Navigation Actions
On your keyboard
OSD Main Menu
To Log into the KVM/net Through the OSD
Menu Selection Select the menu item to Where Documented
Invoking OSD Using PrintScreen Key
To Invoke OSD Using Print Screen Button
Reboot the KVM/net
Connection Menu
Power Management Menu
Configure Menu Overview
Date/Time
Network
User Station
Groups
Notifications Authentication Save/Load Config Exit
Users
Cascade
Understanding OSD Configuration Screen Series
2OSD Configuration Series Screens
General Configuration Screens OSD
Screen Description
Escape sequence or keyboard shortcuts configuration
Syslog facility number that is used by the administrator
Examples of using facility numbers as needed. In addition,
Default Ctrl+k, shown as Ctrlk in the screen. See
Administrator
Enables or disables direct access to KVM ports from the Web
Manager login screen
AlterPath Viewer. For example 5903+ means that the first
Network Configuration Menu Options OSD
Network Configuration Screens OSD
Save overwrites the backup configuration files and makes
Enable or disable DHCP. When you select enabled, the screen
Active saves the changes to the configuration files. active
Network Configuration menu
Domain name
IP address for the DNS server
Hostname for the KVM/net
Snmp Configuration Screens OSD
On Screen Display 369
370
Commonly known. By default, the public community cannot
Email address for the KVM/net administrator, for example
Further defined by the type of access specified under
Access Snmp information on the KVM/net
Read/Write Read-write access to the entire MIB except for
Read Only Read-only access to the entire MIB Management
Information Base except for Snmp configuration objects
Snmp configuration objects
VPN Configuration Screens OSD
On Screen Display 373
Any descriptive name you want to use to identify this
Connection such as MYCOMPANYDOMAIN-VPN
This is the hostname that a local system use for IPSec
Negotiation and authentication
Hostname of the KVM/net, referred to as the local host
It can be a Fully Qualified Domain Name preceded by @. For
VPN connection is ignored. Add means to wait for
Side sends packets to the KVM/net
Connections at startup. Start means to make the connection
IP Filtering Configuration Screens
On Screen Display 377
378
Only appears when Add Chain is selected. Entering the name
Lists the default chains along with any administratively
Configured chains, the Add Chain, and the Exit options
Appears when a user-added chain is selected from the Filter
Chosen from the Chain Chainname menu. Choices are
Target action to take when a packet’s characteristics match
Netmask of the subnetwork where an input packet originates
Accept or Drop
Choices are All, Numeric, TCP, UDP, Icmp
Netmask of the subnet to which an output packet is going
Appears only if Numeric is selected from the Protocol menu
Appears only if TCP is selected from the Protocol menu
Options are Any, Set, Unset
Appears only if All, Numeric, TCP, UDP, or Icmp
Are selected from the Protocol menu
Hosts Configuration Screens OSD
ScreenDescription
Static Routes Configuration Screens
Choices are default and any previously configured static
Appears only when the Edit and Delete options are selected
Routes
Listed in the routing table
Types of routes host, net, or default. Note a default
Appears only when net is selected from the Host or Net
IP address for the target host or network
Screen
Date/time Configuration Screens
Number of hops to the destination
User Station Screens
OSD. The default is 3 minutes
Period of inactivity before the user is logged out from
Redefine the command key for the KVM connection quit hot
Default is 10 minutes
US Default
Period of inactivity before the screen saver starts.
12User Station Configuration Screens
Mouse/keyboard reset hot key
KVM Ports Screens
Following table shows the KVM port configuration screens
Defined aliases
Display the new login window
Accepted. The new alias replaces the default port name
Command is sent to the server to lock the current user
Allows you to enter one or more numbers that identify power
5AUX Port Configuration Screens
AUX Port Screens
Aux port are enabled by default. If you need to disable a
Following table shows the AUX port configuration screens
Choices are Disable, Power Management, and PPP
Select the desired protocol Power Management or PPP
None, even, or odd
Local IP address
Cascade Devices
Options include Add device, Edit device, and Delete device
Device name
Screen Description Cascade Device
Edit Device
Device
Appears when Delete device is selected from the Cascade
Device Choose an option screen
Following confirmation screen appears once a cascaded
Users and Groups Screens
On Screen Display 403
7Users and Groups Configuration Screens
Selected. Note Passwords are case sensitive
Options are Add User, Change Password, Delete User
Appears only when Add User or Change Password are
When the password is successfully confirmed, the following
Options are Add group, Add user to group, Del. user from
Appears only when Change Password or Delete User are
Confirmation screen like the following appears
Group, Delete group, and Exit
Multiple users, use a comma to separate each username
When Add user or Add user to group are selected. To add
When the user is successfully added, the following
Confirmation screen appears
Generic Users’ default permission is No Access, and no
Generic Users, admin, and any administratively defined
Admin and any users in the admin group. By default,
Regular users that may be added cannot access any KVM ports
Ports, which apply unless the user has specific access
Access list includes the Reset all, Default, Multiple
Default option defines access permissions for all KVM
For a new user, because Default Access, is not defined,
Syslog Screens
Notification Screens
Alarm Trigger
Define the event you want to trigger a notification for
Community
Trap Number
Server IP
Authentication Screens
Screen Body Description
9Authentication Options and Screens
Authentication method options for KVM/net logins. Default =
Method for KVM/net logins, or choose one
Authentication server Kerberos, Ldap, Radius, TacacsPlus
Local. Other authorization type options are Kerberos
IP address of the Kerberos or Ldap server
Login attribute
Choices are Yes or No
Radius or TACACS+ authentication server
IP addresses of one or two optional accounting servers
23Smb Ntlm Configuration Screens
IP addresses for one or two SMB Ntlm
Authentication servers. The second server IP is
Choose the NIS authentication server
Optional
Save/Load Configuration Screens
On Screen Display 421
When Save Configuration is selected, the following two
FTP Login Username and Password. The last screens
25Save/Load Configuration Screens
When Save to FTP is selected, the following five screens
Confirm the save to FTP succeeded
System Info Menu
Information Type Example
RP main
RP local
To reboot the KVM/net
Reboot
To Access System Information
Select Reboot from the Main Menu Following message appears
Select Yes to reboot the KVM/net
To Use to the KVM RP to Access the KVM/net
Controlling the OSD Through the AlterPath KVM RP
On Screen Display 429
430
To Boot From Tftp
How to Replace the KVM/net’s Boot Image
Appendix a
Press ESC when the Testing Ethernet prompt appears
Select the boot type at the following prompt
IP address assigned to Ethernet interface
434
Table A-1Boot Message
To Save the zImage into the KVM/net’s Flash Memory
Exit ftp when the download is completed Reboot the KVM/net
From this directory, ftp to your FTP server
FTP Method
How to Upgrade the Firmware on KVM/net
SSH/SCP Method
Following md5 file is generated and displayed
439
How to Boot the KVM/net Over the Network
Firmware boot from Flash or Network F N
To Boot the KVM/net in Single User Mode
How to Boot the KVM/net in Single User Mode
Type spsingle spacebar, then the word single
If the password is forgotten execute the following command
System reboots and displays the following message
Root@none root# saveconf Root@none root# reboot
How to Disable Mouse Acceleration Using Windows Registry
446
Technical Specifications
Appendix B
Dimensions WxDxH Certifications
General Safety Precautions
Appendix C
450
Table Placement
Rack or Cabinet Placement
Safety Guidelines for Rack-Mounting the KVM/ net
Temperatur
Safety Precautions for Operating the AlterPath KVM/net
Circuit Overloading
Sicherheitsvorkehrungen beim Betrieb des AlterPath KVM/net
455
456
Basic In/Out System
Baud Rate
BogoMips
Boot
Bootp
Bonding Linux
DNS Server
Cidr Notation
Cluster
Domain Name
Flash
Escape Sequence
Ethernet
Flow control
IP address
Hot-Swap
IP packet filtering
IPsec
Kerberos
Network Mask
Packet
Parity
Port
Routing Table
Root Access
Secure Shell SSH
Server Farm
Snmp Traps
Subnet Mask
Stop Bit
Sudo
Telnet
Rack Height Unit
Watchdog timer
Index
268
Adding 240, 243 editing 240
Authentication servers 208 AUX 1 port Basic networking
OSD
CPU 424
Domain Name 416, 419, 420 download microcode 293 downloading
477
478
209
LAN Ldap Ldap authentication server, configuring an
LEDs
IP address and port entered 320 IP address entered
Netmask 367, 388 network 226 Network bits/sec
410
484
485
Conventions for showing how to navigate to screens
200
Target 380
489
VPN 56