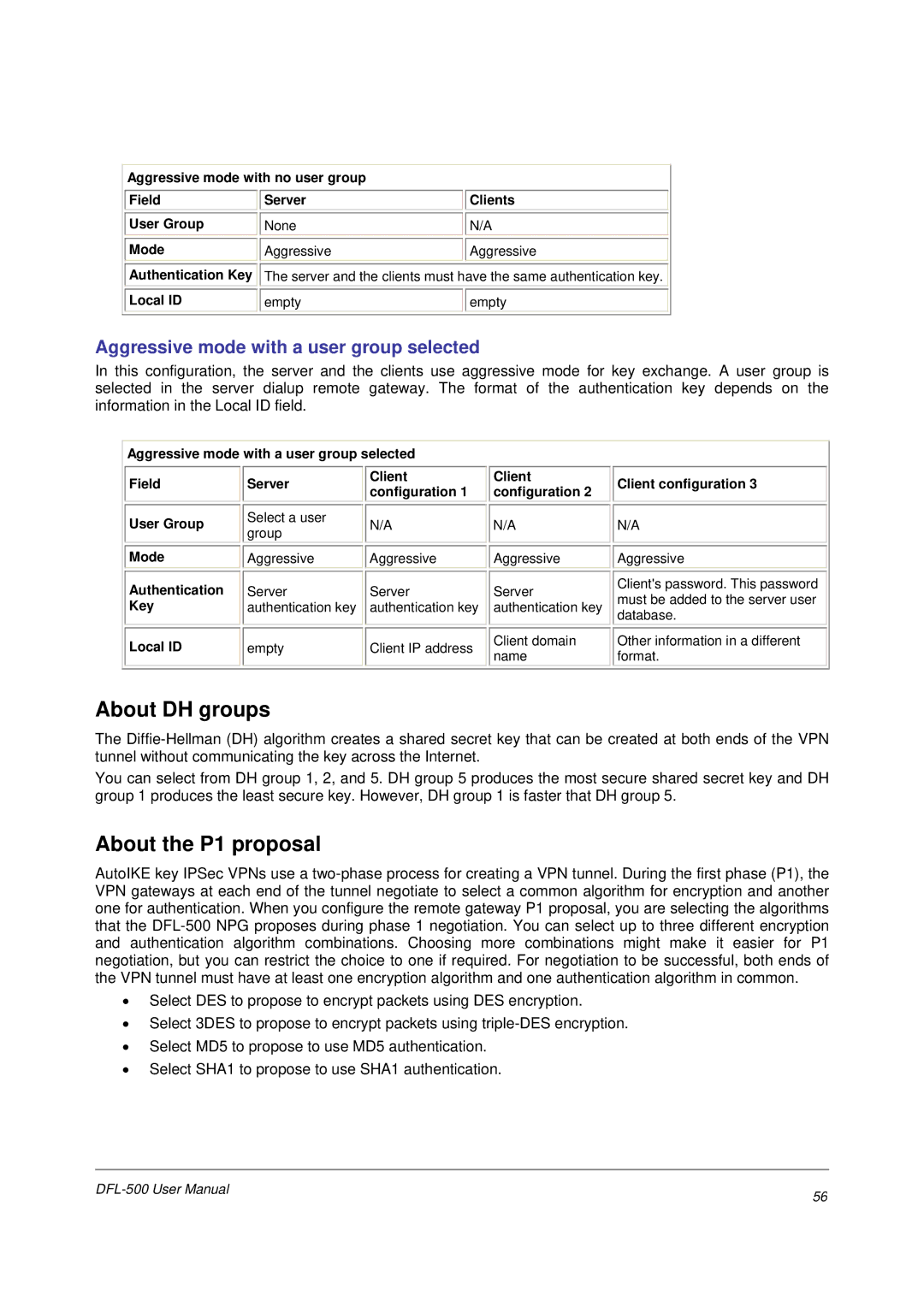
Aggressive mode with no user group |
|
| ||
|
|
|
|
|
Field |
| Server |
| Clients |
|
|
|
|
|
User Group |
| None |
| N/A |
|
|
|
|
|
Mode |
| Aggressive |
| Aggressive |
|
|
| ||
Authentication Key |
| The server and the clients must have the same authentication key. | ||
|
|
|
|
|
Local ID |
| empty |
| empty |
|
|
|
|
|
Aggressive mode with a user group selected
In this configuration, the server and the clients use aggressive mode for key exchange. A user group is selected in the server dialup remote gateway. The format of the authentication key depends on the information in the Local ID field.
Aggressive mode with a user group selected |
|
|
|
| ||||
|
|
|
|
|
|
|
|
|
Field |
| Server |
| Client |
| Client |
| Client configuration 3 |
|
| configuration 1 |
| configuration 2 |
| |||
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
|
User Group |
| Select a user |
| N/A |
| N/A |
| N/A |
| group |
|
|
| ||||
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
Mode |
| Aggressive |
| Aggressive |
| Aggressive |
| Aggressive |
|
|
|
|
|
|
|
|
|
Authentication |
| Server |
| Server |
| Server |
| Client's password. This password |
|
|
|
| must be added to the server user | ||||
Key |
| authentication key |
| authentication key |
| authentication key |
| |
|
|
|
| database. | ||||
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
Local ID |
| empty |
| Client IP address |
| Client domain |
| Other information in a different |
|
|
| name |
| format. | |||
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
|
About DH groups
The
You can select from DH group 1, 2, and 5. DH group 5 produces the most secure shared secret key and DH group 1 produces the least secure key. However, DH group 1 is faster that DH group 5.
About the P1 proposal
AutoIKE key IPSec VPNs use a
•Select DES to propose to encrypt packets using DES encryption.
•Select 3DES to propose to encrypt packets using
•Select MD5 to propose to use MD5 authentication.
•Select SHA1 to propose to use SHA1 authentication.
56 | |
|