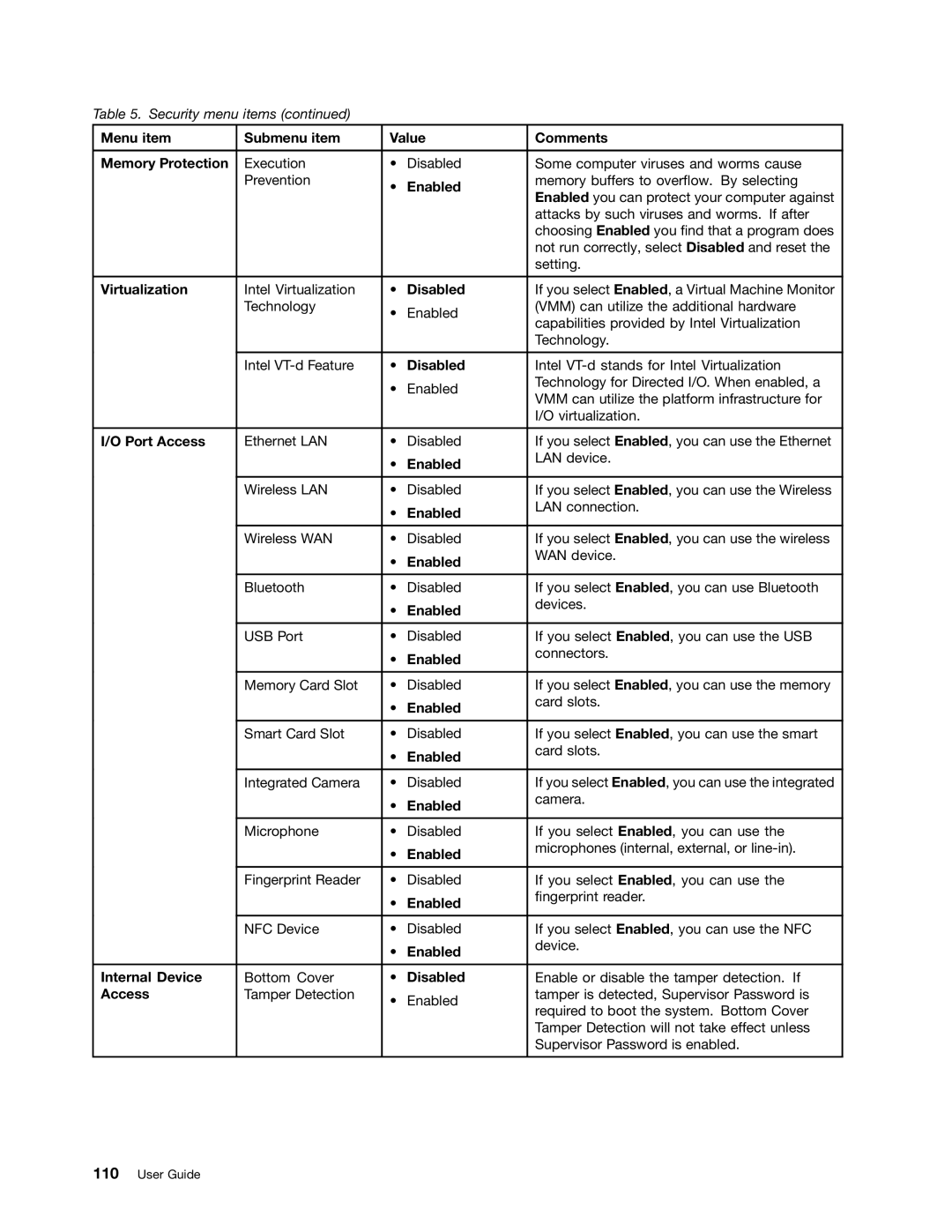
Table 5. Security menu items (continued)
Menu item | Submenu item | Value | Comments | |
|
|
|
|
|
Memory Protection | Execution | • | Disabled | Some computer viruses and worms cause |
| Prevention | • | Enabled | memory buffers to overflow. By selecting |
|
| Enabled you can protect your computer against | ||
|
|
|
| |
|
|
|
| attacks by such viruses and worms. If after |
|
|
|
| choosing Enabled you find that a program does |
|
|
|
| not run correctly, select Disabled and reset the |
|
|
|
| setting. |
|
|
|
|
|
Virtualization | Intel Virtualization | • | Disabled | If you select Enabled, a Virtual Machine Monitor |
| Technology | • | Enabled | (VMM) can utilize the additional hardware |
|
| capabilities provided by Intel Virtualization | ||
|
|
|
| |
|
|
|
| Technology. |
|
|
|
|
|
| Intel | • | Disabled | Intel |
|
| • | Enabled | Technology for Directed I/O. When enabled, a |
|
| VMM can utilize the platform infrastructure for | ||
|
|
|
| |
|
|
|
| I/O virtualization. |
|
|
|
|
|
I/O Port Access | Ethernet LAN | • | Disabled | If you select Enabled, you can use the Ethernet |
|
| • | Enabled | LAN device. |
|
|
| ||
|
|
|
|
|
| Wireless LAN | • | Disabled | If you select Enabled, you can use the Wireless |
|
| • | Enabled | LAN connection. |
|
|
| ||
|
|
|
|
|
| Wireless WAN | • | Disabled | If you select Enabled, you can use the wireless |
|
| • | Enabled | WAN device. |
|
|
| ||
|
|
|
|
|
| Bluetooth | • | Disabled | If you select Enabled, you can use Bluetooth |
|
| • | Enabled | devices. |
|
|
| ||
|
|
|
|
|
| USB Port | • | Disabled | If you select Enabled, you can use the USB |
|
| • | Enabled | connectors. |
|
|
| ||
|
|
|
|
|
| Memory Card Slot | • | Disabled | If you select Enabled, you can use the memory |
|
| • | Enabled | card slots. |
|
|
| ||
|
|
|
|
|
| Smart Card Slot | • | Disabled | If you select Enabled, you can use the smart |
|
| • | Enabled | card slots. |
|
|
| ||
|
|
|
|
|
| Integrated Camera | • | Disabled | If you select Enabled, you can use the integrated |
|
| • | Enabled | camera. |
|
|
| ||
|
|
|
|
|
| Microphone | • | Disabled | If you select Enabled, you can use the |
|
| • | Enabled | microphones (internal, external, or |
|
|
| ||
|
|
|
|
|
| Fingerprint Reader | • | Disabled | If you select Enabled, you can use the |
|
| • | Enabled | fingerprint reader. |
|
|
| ||
|
|
|
|
|
| NFC Device | • | Disabled | If you select Enabled, you can use the NFC |
|
| • | Enabled | device. |
|
|
| ||
|
|
|
|
|
Internal Device | Bottom Cover | • | Disabled | Enable or disable the tamper detection. If |
Access | Tamper Detection | • | Enabled | tamper is detected, Supervisor Password is |
|
| required to boot the system. Bottom Cover | ||
|
|
|
| |
|
|
|
| Tamper Detection will not take effect unless |
|
|
|
| Supervisor Password is enabled. |
|
|
|
|
|