Configuring Security and Authentication
Chain rule - The Chain rule determines whether access from the hosts is allowed or not. It can be one of these two values:
ACCEPT : access allowed
DROP : access not allowed
A user can add a new IP filtering rule by entering the values for the parameters and clicking the Add button on the right hand side of the table. A user can remove a rule by using the Remove button. After having finished editing the table be sure to save the settings to flash using the Save to flash button or to save and apply them using the Save & apply button. Be aware that the changes need to be applied before becoming active.
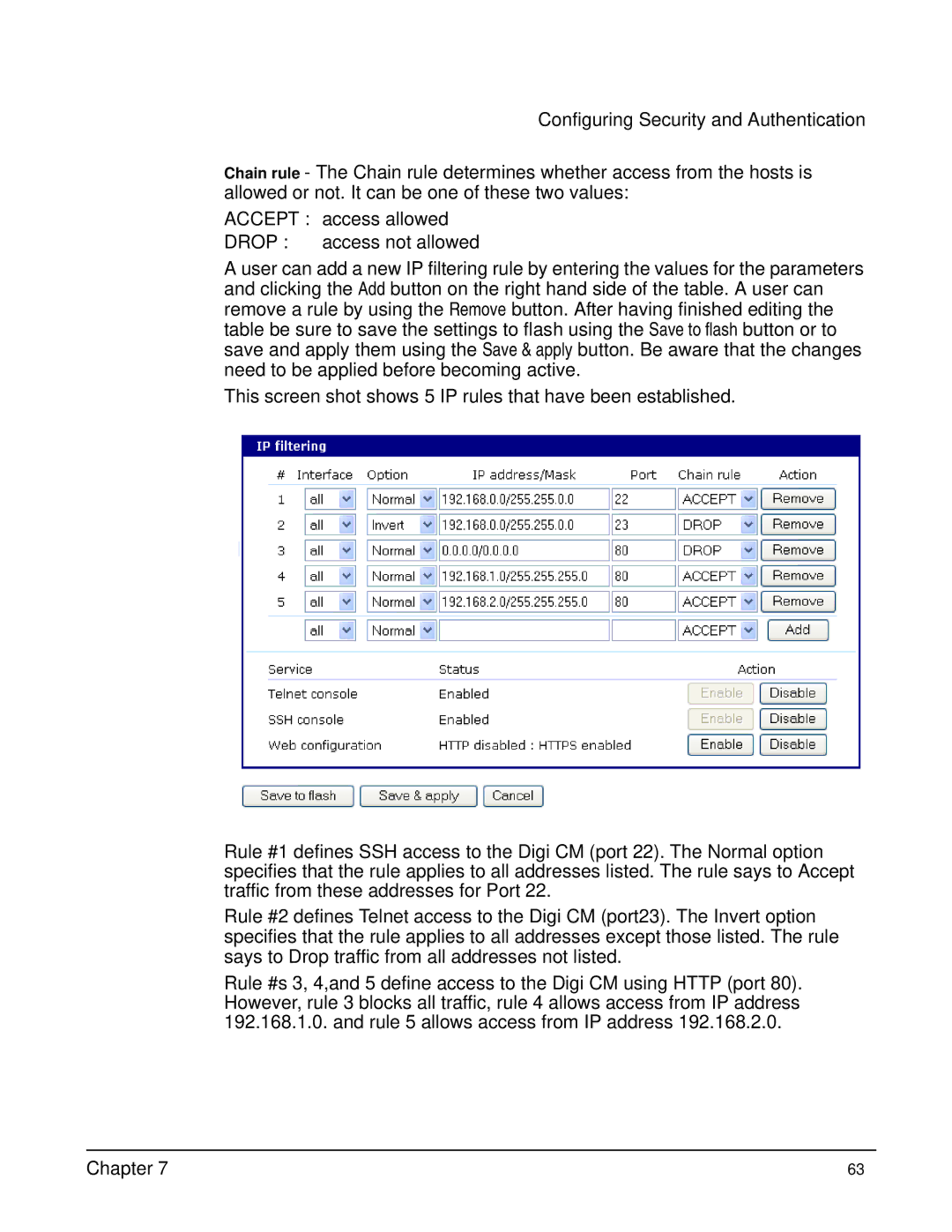
This screen shot shows 5 IP rules that have been established.
Rule #1 defines SSH access to the Digi CM (port 22). The Normal option specifies that the rule applies to all addresses listed. The rule says to Accept traffic from these addresses for Port 22.
Rule #2 defines Telnet access to the Digi CM (port23). The Invert option specifies that the rule applies to all addresses except those listed. The rule says to Drop traffic from all addresses not listed.
Rule #s 3, 4,and 5 define access to the Digi CM using HTTP (port 80). However, rule 3 blocks all traffic, rule 4 allows access from IP address 192.168.1.0. and rule 5 allows access from IP address 192.168.2.0.
Chapter 7 | 63 |