MVP-8400i
AMX Limited Warranty and Disclaimer
FCC Information
Page
Table of Contents
Upgrading MVP Firmware
Programming 101
Panel Calibration 159
181
Page
MVP-8400i Touch Panel
Overview
MVP-8400i Specifications FG5965-04
Specifications
Memory factory default
Power Modes
Battery Duration
Per battery
FG2255-07
Included Accessories
Certifications
Other AMX Equipment
Power Voltage
Installing MVP-BP Batteries
MVP-BP Specifications
MVP-BP Specifications
If you are only using one battery, use Battery Slot #1
Compact Flash Card Security
Installing the NXA-CFSP Compact Flash Card
Accessing the MVP’s Internal Components
Optional Compact Flash Upgrades
Installing the Compact Flash Upgrade Card
Removing the Installed Card
Care When Handling the Card
Page
802.11b Wireless Interface Card
Specifications
802.11b Wireless Interface Card Specifications
NXA-WC80211GCF 802.11g Wireless Interface Card
NXA-WC80211GCF Specifications
RF Frequency Ranges
Wireless LAN Security
Radio Technology
Receiver Sensitivity
Firmware Requirements
Installing the 802.11g Card and Antenna
Access the MVP’s Internal Components
Preparing the MVP’s Rear Housing
Installing the Mounting Template
Installing the NXA-WC80211GCF
Closing and Securing the MVP Enclosure
Outer housing latch attachment locations
Wireless Interface Cards
Accessing the Setup and Protected Setup Pages
Modero Setup and System Settings
Wireless Settings Page Wireless Access Overview
Setting the Panel’s Device Number
Hot Swapping
Configuring a Wireless Network Access
Configure the Panel’s Wireless IP Settings
Wireless communication using a Dhcp Address
Using the Site Survey tool
Wireless communication using a Static IP Address
Site Survey
Configure the Card’s Wireless Security Settings
MVP connection IP info Wireless Card security settings
Required Information
Automatically set Ssid
Select Wireless Settings
Manually set Ssid
Locate the Wireless Security section FIG
These WEP Key identifier values must match for both devices
WEP Key # Keyboard
Select System Settings
Choose a Master Connection Mode
System Settings page USB Connection
USB driver installation popup window
Configure a Virtual NetLinx Master using NetLinx Studio
Assigning Communication Settings for a Virtual Master
Connection Modes
Mode Description Procedures
Ethernet
Master Connection to a Virtual Master via Ethernet
Configuring Communications
Ethernet
G4 Web Control
Using G4 Web Control to Interact with a G4 Panel
Configuring Communications
Using your NetLinx Master to control the G4 panel
Web Control VNC installation and Password entry screens
Configuring Communications
Upgrading MVP Firmware
Configure the panel for a USB Connection Type
Upgrading the Modero Firmware via the USB port
Prepare Studio for communication via the USB port
Default Modero panel value is
Confirm and Upgrade the firmware via the USB port
Using USB for a Virtual Master transfer
Prepare the Docking Station for firmware transfer via USB
Upgrading the Docking Station Firmware via USB
Batteries
Upgrade the Docking Station firmware via USB
Device and System values
Upgrading MVP Firmware
Navigation Buttons
Setup Pages
Connection Status
Setup Pages
Setup
Display Timeout
Panel Brightness
Timeout
Information
Inactivity Page Flip
Project Information
Project Information
IR User Def 2 Port
AMX IR 38K Port
AMX IR 455K Port
IR User Def 1 Port
Panel Information
Panel Information
Time & Date Setup
Date Display fields
Time & Date Setup
Time Date Refresh/Set
Time Display fields
Volume
Volume
Master Volume
Supported WAV Sample Rates
WAV files Supported sample rates
Panel Shutdown
Batteries
Batteries
Limit
Battery Status
Low Battery Warning
Device Number
Protected Setup Pages
Protected Setup
Navigation Buttons
Options
Protected Setup Navigation Buttons
System Recovery
Reboot Panel
G4 Web Control
Protected Setup Navigation Buttons
G4 Web Control Settings
G4 Web Control Timeout
G4 Web Control
Calibration
Calibration
Wireless Settings
Wireless Settings
IP Settings
Network Name Ssid WAP names
Access Point MAC
Wireless Security
Address
RF Link Info
Site Survey
Wireless Security
Wireless Security Support
802.11g Wi-Fi CF card
Open Clear Text Settings
Open Clear Text Settings
Save/Cancel
Static WEP Settings
Static WEP Settings
WEP 64 / WEP
WEP Keys
Default Key
Authentication
Generate Passphrase
Wireless Settings page WPA-PSK Settings
WPA-PSK Settings
EAP-LEAP Settings
WPA-PSK Settings
Password/Pass Phrase
EAP-LEAP Settings
Password
Identity
EAP-LEAP sample Cisco System Security
EAP-FAST Settings
Provisioning
EAP-FAST Settings
Anonymous Identity
Automatic PAC
EAP-PEAP Settings
Been Disabled
PAC File Location
Peap Version
EAP-PEAP Settings
Inner Authentication Type
Certificate Authority
EAP-TTLS Settings
EAP-TTLS Settings
Ssid Service Set Identifier
MSCHAPv2 default because its the most common
EAP-TLS Settings
EAP-TLS Settings
Client Certificate
Client certificate configuration
Client Certificate Configuration
Private Key password
Certificate Type Possible File Extensions
Configuration Field Name Certificate File Type Supported
Certificates and their Extensions
Certificate Types Supported by the Modero Firmware
System Settings
System Settings Page Elements
Master Connection
Ethernet Only disabled when USB is selected
Other Settings menu
Other Settings
Image Caching
Image Caching
Clear Cache
Image Cache Settings
Enable
Image Caching Page Elements
Checking image cache status
Setting the image cache
Password Setup
Clearing the image cache
User Access
SIP Settings
Password Setup
Panel Password
SIP Settings
Panel Logs
Tools
Panel Logs
Checking the Panel Connection Logs
Refreshing the Panel Connections Log
Clearing the Panel Connections Log
Panel Statistics
Panel Statistics
Checking the Panel Statistics
Refreshing the Panel Statistics
Clearing the Panel Statistics
Connection Utility
Connection Utility
Using the Connection Utility
@APG
Commands
Commands
Button Assignments
@PHE
@CPG
@DPG
@PDR
@PPG
@PHT
@PPA
@PPF
@PPT
@PPK
@PPM
@PPN
@PST
@PPX
@PSE
@PSP
Ppof
Ppog
Ppon
Index No Name Red Green Blue
Programming Numbers
RGB triplets and names for basic 88 colors
RGB Values for all 88 Basic Colors
108 MVP-8400i Modero Viewpoint Wireless Touch Panels
Default Font Styles and ID Numbers
Font styles and ID numbers
Font ID Font type Size
Border styles
Border styles and Programming numbers
Border Styles and Programming Numbers
TPD4 Border Styles by Name
MVP-8400i Modero Viewpoint Wireless Touch Panels 111
ANI
Button Commands
Button Commands
Sendcommand Panel,ANI-500,1,25,100
APF
BAT
BAU
BCB
BCF
BCT
Entry is required
BDO
BFB
BIM
BMC
BLN
BMF-vt addr range,button states range,data
BMF
Cont
BNC
BMI
BML
BMP
BOP
BNN
BNP
BNT
BOR
BOS
BPP
BSO
BRD
BSF
BSM
BVP
BSP
BVL
BVN
DPF
BWW
CPF
DLD
FON
GDI
GIV
GRU
GLH
GLL
GRD
GSN
ICO
IRM
JSI
JSB
SHO
JST
MBT
MDC
TEC
TEF
TXT
MVP Strings to Master
MVP Panel Lock Passcode commands
MVP Panel Lock Passcode Commands
Miscellaneous MVP Strings back to the Master
LPS
Text Effects Names
Text Effects
LPR
Defineevent
Button Query Commands
?BCB
Button Query Commands
Send Command Panel,?BCB-529,1
Custom Event Fields
?BCT
?BCF
?BOP
?BMP
?BWW
?BRD
?ICO
?FON
?JSI
?JSB
?TEC
?JST
?TEF-vt addr range,button states range
Send Command Panel,?TEF-529,1
Send Command Panel,?TXT-529,1
?TEF
Panel Runtime Operations
Panel Runtime Operation Commands
Brit
@AKP
@AKR
Beep
@PKP
Setup
@EKP
Pkeyp
@SWK
@SOU
@SSL
@SST
Wake
Tpageon
Tpageoff
@VKB
KPS
Input Commands
Input Commands
CAL
MPS
TPS
VKS
Embedded codes
Embedded Codes
Decimal numbers Hexidecimal values Virtual keystroke
Panel Setup Commands
Panel Setup Commands
ICM-SPEAKERLEVEL
Cfsm
CEX
ICM-MUTEMIC
PWD
ICM-MICLEVEL
MUT
@PWD
Dynamic Image Commands
Dynamic Image Commands
RAF-resource name,data
Panel Intercom Commands
Panel Intercom Commands
SIP Commands
SIP Commands
PHN-ANSWER
PHN-PRIVACY
PHN-REDIAL
Transferred
?PHN-PRIVACY
PHN-DTMF
PHN-HANGUP
PHN-HOLD
Calibrating the MVP Panels
Panel Calibration
Touch Panel Calibration Screens
Testing your Calibration
If Calibration Is Not Working
Page
Example
Text Formatting Codes for Bargraphs/Joysticks
Bargraph Text Code Inputs
Formatting Code Operations
Character Masking Rule
Text Area Input Masking
Input mask character types
Character Types
Input mask literals
Input mask ranges
Input mask next field characters
Input mask operations
Input mask output examples
Output Examples
Common Name Input Mask
Sequence Panel Information
URL Resources
Special escape sequences
Escape Sequences
Page
Overview of Wireless Technology
Appendix B Wireless Technology
802.1x
Terminology
Tkip
WPA2
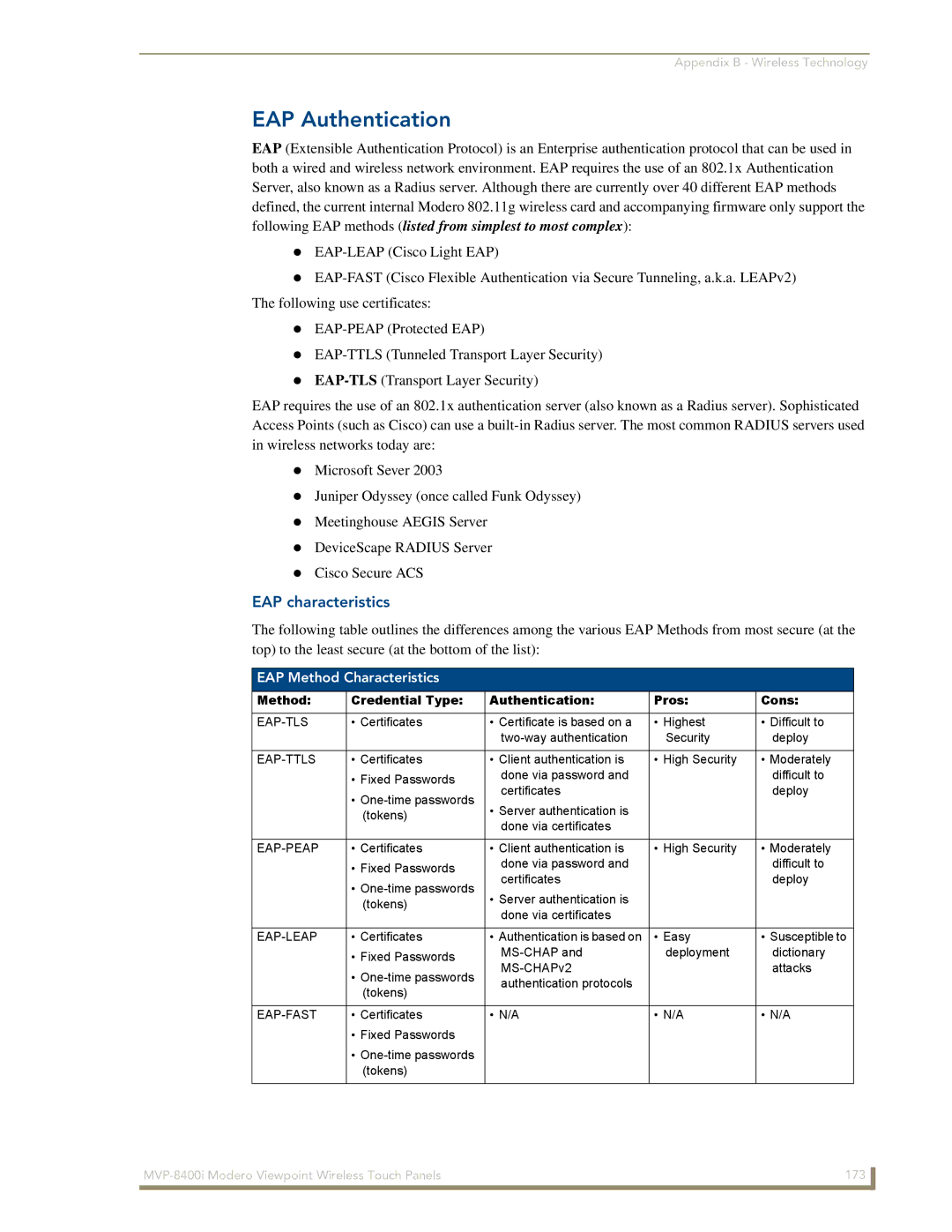
Method Credential Type Authentication Pros Cons
EAP Authentication
EAP characteristics
EAP Method Characteristics
LAN
EAP communication overview
Configuring your G4 Touch Panel for USB Communication
Setup the Panel and PC for USB Communication
AMX Certificate Upload Utility
Confirm the Installation of the USB Driver on the PC
How to Upload a Certificate File
178 MVP-8400i Modero Viewpoint Wireless Touch Panels
Appendix C Troubleshooting
USB Properties windows Windows Device Manager
Checking AMX Usblan device connections via NetLinx Studio
Panel Not in Listed As a Connected Device
USB Driver
Connection Status
Panel Doesn’t Respond To Touches
Batteries Will Not Hold Or Take a Charge
NetLinx Studio Only Detects One Of My Connected Masters
Modero Panel Isn’t Appearing In The Online Tree Tab
MVP Can’t Obtain a Dhcp Address
My WEP Doesn’t Seem To Be Working
Only One Modero Panel In My System Shows Up
Panel Fails to Charge in MVP-WDS
Page
Page
It’s Your World Take Control