13-20 User’s Reference Guide
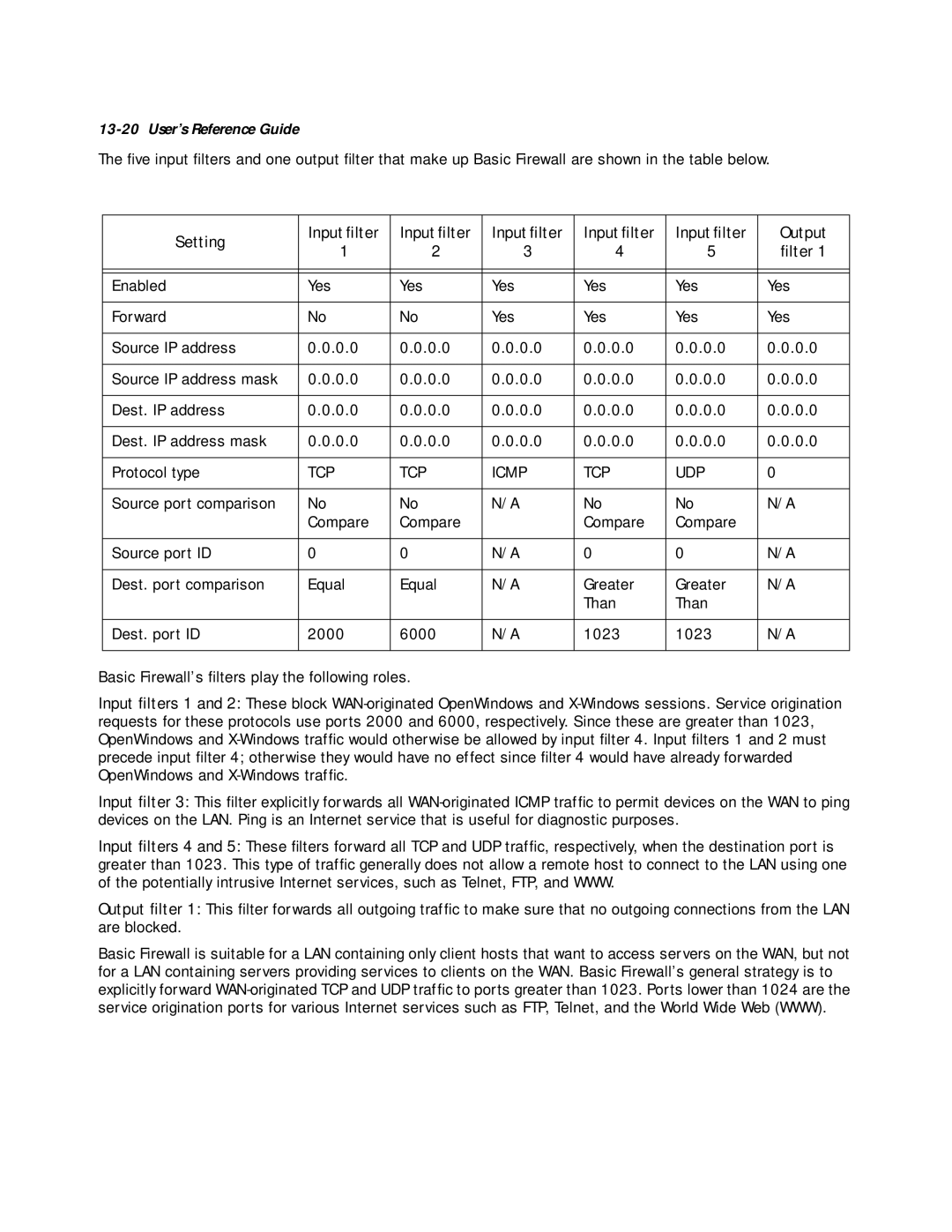
The five input filters and one output filter that make up Basic Firewall are shown in the table below.
Setting | Input filter | Input filter | Input filter | Input filter | Input filter | Output | |
1 | 2 | 3 | 4 | 5 | filter 1 | ||
| |||||||
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
Enabled | Yes | Yes | Yes | Yes | Yes | Yes | |
|
|
|
|
|
|
| |
Forward | No | No | Yes | Yes | Yes | Yes | |
|
|
|
|
|
|
| |
Source IP address | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | |
|
|
|
|
|
|
| |
Source IP address mask | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | |
|
|
|
|
|
|
| |
Dest. IP address | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | |
|
|
|
|
|
|
| |
Dest. IP address mask | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | 0.0.0.0 | |
|
|
|
|
|
|
| |
Protocol type | TCP | TCP | ICMP | TCP | UDP | 0 | |
|
|
|
|
|
|
| |
Source port comparison | No | No | N/A | No | No | N/A | |
| Compare | Compare |
| Compare | Compare |
| |
|
|
|
|
|
|
| |
Source port ID | 0 | 0 | N/A | 0 | 0 | N/A | |
|
|
|
|
|
|
| |
Dest. port comparison | Equal | Equal | N/A | Greater | Greater | N/A | |
|
|
|
| Than | Than |
| |
|
|
|
|
|
|
| |
Dest. port ID | 2000 | 6000 | N/A | 1023 | 1023 | N/A | |
|
|
|
|
|
|
|
Basic Firewall’s filters play the following roles.
Input filters 1 and 2: These block
Input filter 3: This filter explicitly forwards all
Input filters 4 and 5: These filters forward all TCP and UDP traffic, respectively, when the destination port is greater than 1023. This type of traffic generally does not allow a remote host to connect to the LAN using one of the potentially intrusive Internet services, such as Telnet, FTP, and WWW.
Output filter 1: This filter forwards all outgoing traffic to make sure that no outgoing connections from the LAN are blocked.
Basic Firewall is suitable for a LAN containing only client hosts that want to access servers on the WAN, but not for a LAN containing servers providing services to clients on the WAN. Basic Firewall’s general strategy is to explicitly forward