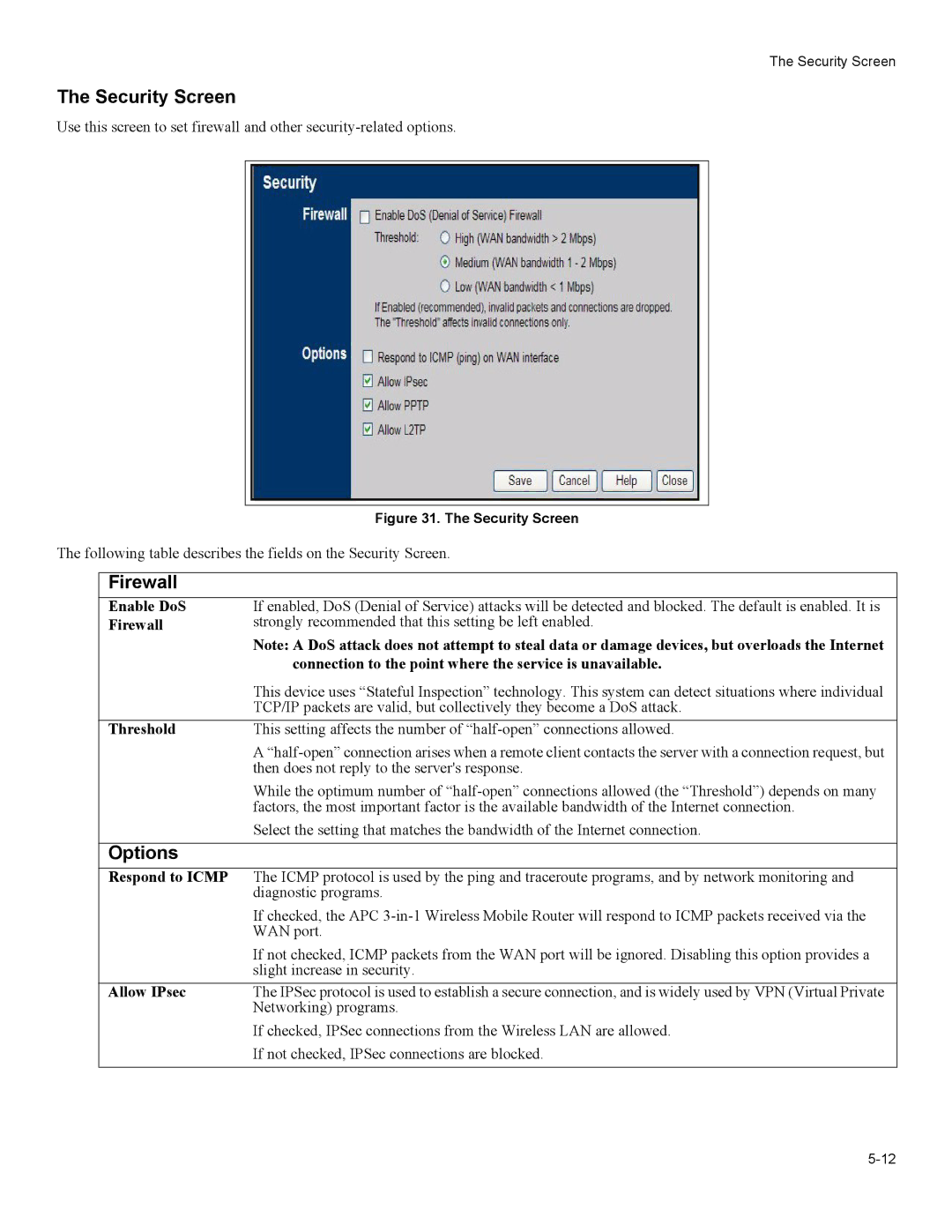
The Security Screen
The Security Screen
Use this screen to set firewall and other
|
| Figure 31. The Security Screen |
The following table describes the fields on the Security Screen. | ||
|
|
|
| Firewall |
|
| Enable DoS | If enabled, DoS (Denial of Service) attacks will be detected and blocked. The default is enabled. It is |
| Firewall | strongly recommended that this setting be left enabled. |
|
| Note: A DoS attack does not attempt to steal data or damage devices, but overloads the Internet |
|
| connection to the point where the service is unavailable. |
|
| This device uses “Stateful Inspection” technology. This system can detect situations where individual |
|
| TCP/IP packets are valid, but collectively they become a DoS attack. |
| Threshold | This setting affects the number of |
|
| A |
|
| then does not reply to the server's response. |
|
| While the optimum number of |
|
| factors, the most important factor is the available bandwidth of the Internet connection. |
|
| Select the setting that matches the bandwidth of the Internet connection. |
|
|
|
| Options |
|
| Respond to ICMP | The ICMP protocol is used by the ping and traceroute programs, and by network monitoring and |
|
| diagnostic programs. |
|
| If checked, the APC |
|
| WAN port. |
|
| If not checked, ICMP packets from the WAN port will be ignored. Disabling this option provides a |
|
| slight increase in security. |
| Allow IPsec | The IPSec protocol is used to establish a secure connection, and is widely used by VPN (Virtual Private |
|
| Networking) programs. |
|
| If checked, IPSec connections from the Wireless LAN are allowed. |
|
| If not checked, IPSec connections are blocked. |
|
|
|