Using Filters for Security Purposes
Example 3: Restricting Access to Authorized Users
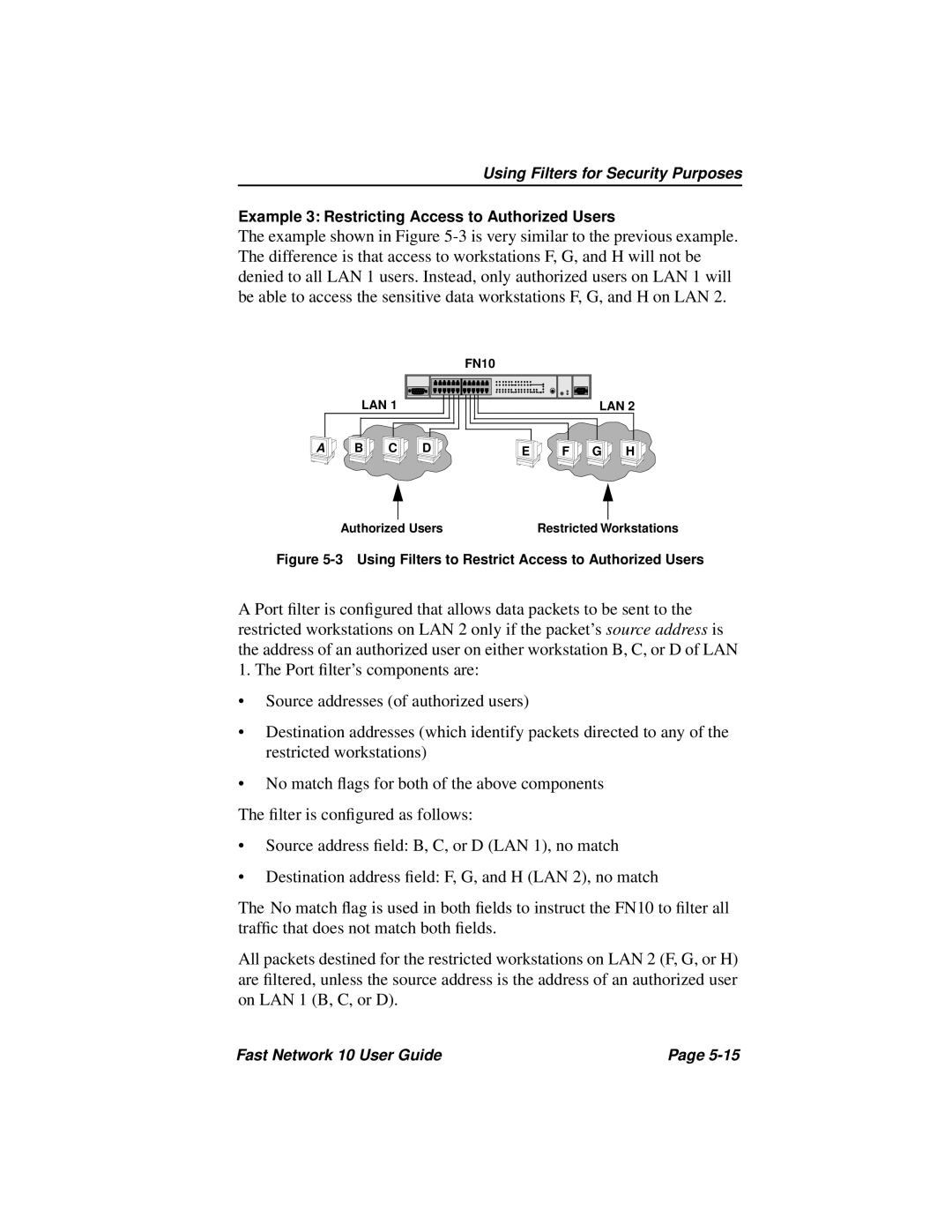
The example shown in Figure
FN10
LAN 1
A | B | C | D |
LAN 2
E | F | G | H |
Authorized Users | Restricted Workstations |
Figure 5-3 Using Filters to Restrict Access to Authorized Users
A Port filter is configured that allows data packets to be sent to the restricted workstations on LAN 2 only if the packet’s source address is the address of an authorized user on either workstation B, C, or D of LAN
1. The Port filter’s components are:
•Source addresses (of authorized users)
•Destination addresses (which identify packets directed to any of the restricted workstations)
•No match flags for both of the above components
The filter is configured as follows:
•Source address field: B, C, or D (LAN 1), no match
•Destination address field: F, G, and H (LAN 2), no match
The No match flag is used in both fields to instruct the FN10 to filter all traffic that does not match both fields.
All packets destined for the restricted workstations on LAN 2 (F, G, or H) are filtered, unless the source address is the address of an authorized user on LAN 1 (B, C, or D).
Fast Network 10 User Guide | Page |