Overview
Authentication Process
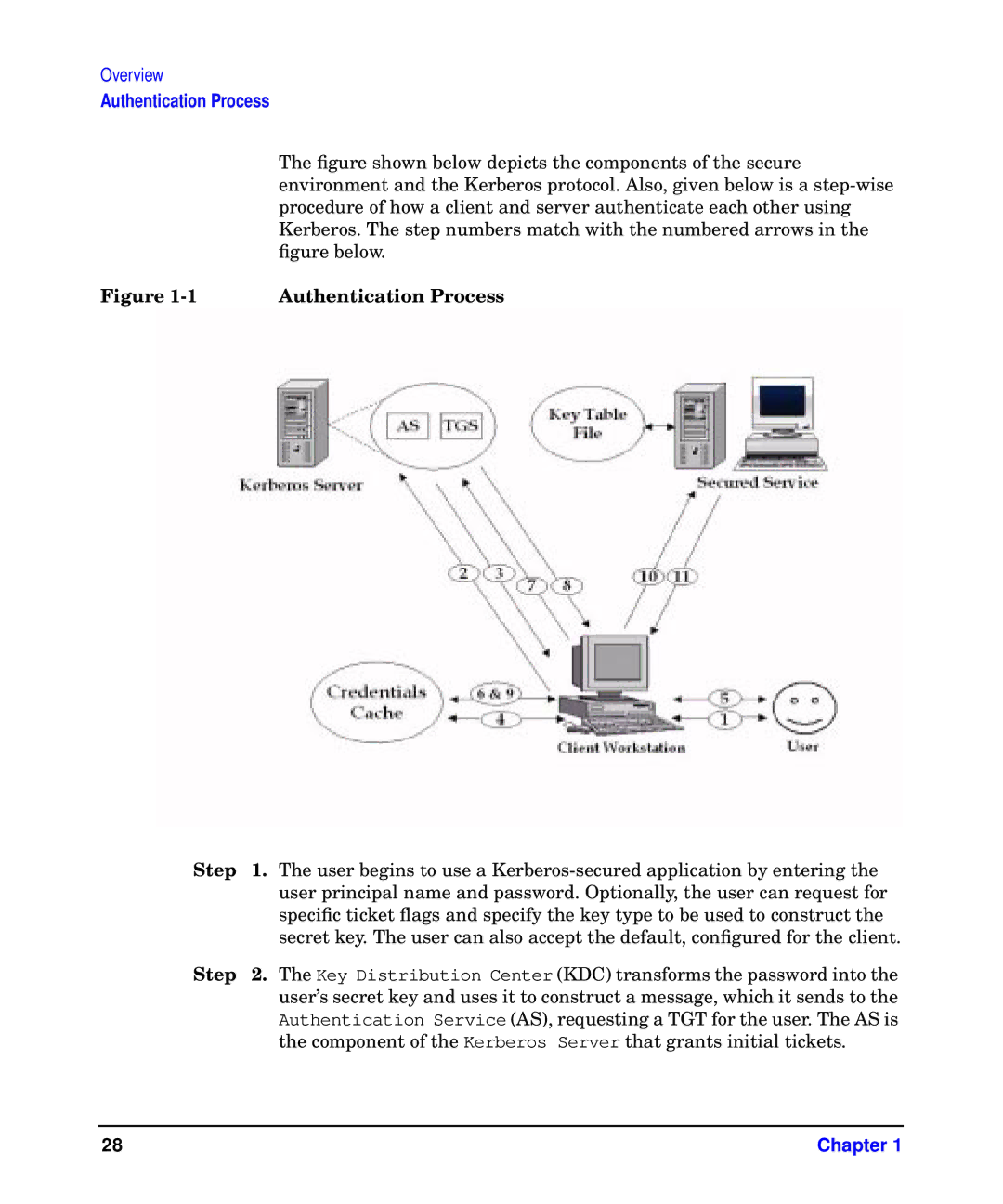
| The figure shown below depicts the components of the secure |
| environment and the Kerberos protocol. Also, given below is a |
| procedure of how a client and server authenticate each other using |
| Kerberos. The step numbers match with the numbered arrows in the |
| figure below. |
Figure | Authentication Process |
Step | 1. | The user begins to use a |
|
| user principal name and password. Optionally, the user can request for |
|
| specific ticket flags and specify the key type to be used to construct the |
|
| secret key. The user can also accept the default, configured for the client. |
Step | 2. | The Key Distribution Center (KDC) transforms the password into the |
|
| user’s secret key and uses it to construct a message, which it sends to the |
|
| Authentication Service (AS), requesting a TGT for the user. The AS is |
|
| the component of the Kerberos Server that grants initial tickets. |
28 | Chapter 1 |