Advanced Configuration |
|
Radius Profiles
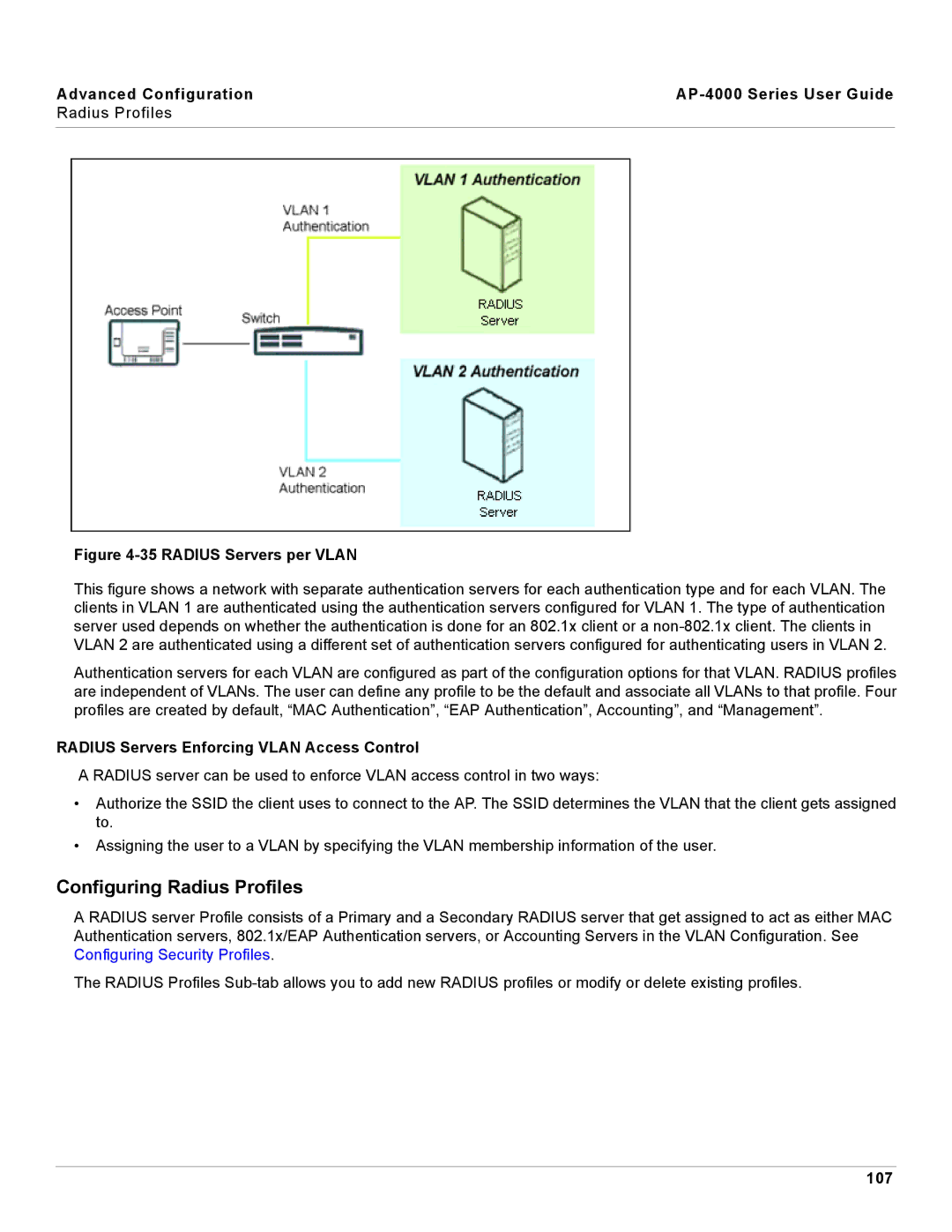
Figure 4-35 RADIUS Servers per VLAN
This figure shows a network with separate authentication servers for each authentication type and for each VLAN. The clients in VLAN 1 are authenticated using the authentication servers configured for VLAN 1. The type of authentication server used depends on whether the authentication is done for an 802.1x client or a
Authentication servers for each VLAN are configured as part of the configuration options for that VLAN. RADIUS profiles are independent of VLANs. The user can define any profile to be the default and associate all VLANs to that profile. Four profiles are created by default, “MAC Authentication”, “EAP Authentication”, Accounting”, and “Management”.
RADIUS Servers Enforcing VLAN Access Control
A RADIUS server can be used to enforce VLAN access control in two ways:
•Authorize the SSID the client uses to connect to the AP. The SSID determines the VLAN that the client gets assigned to.
•Assigning the user to a VLAN by specifying the VLAN membership information of the user.
Configuring Radius Profiles
A RADIUS server Profile consists of a Primary and a Secondary RADIUS server that get assigned to act as either MAC Authentication servers, 802.1x/EAP Authentication servers, or Accounting Servers in the VLAN Configuration. See Configuring Security Profiles.
The RADIUS Profiles