|
|
|
|
|
| Templates and Alerts |
|
|
|
|
|
| Race Condition Template |
Table |
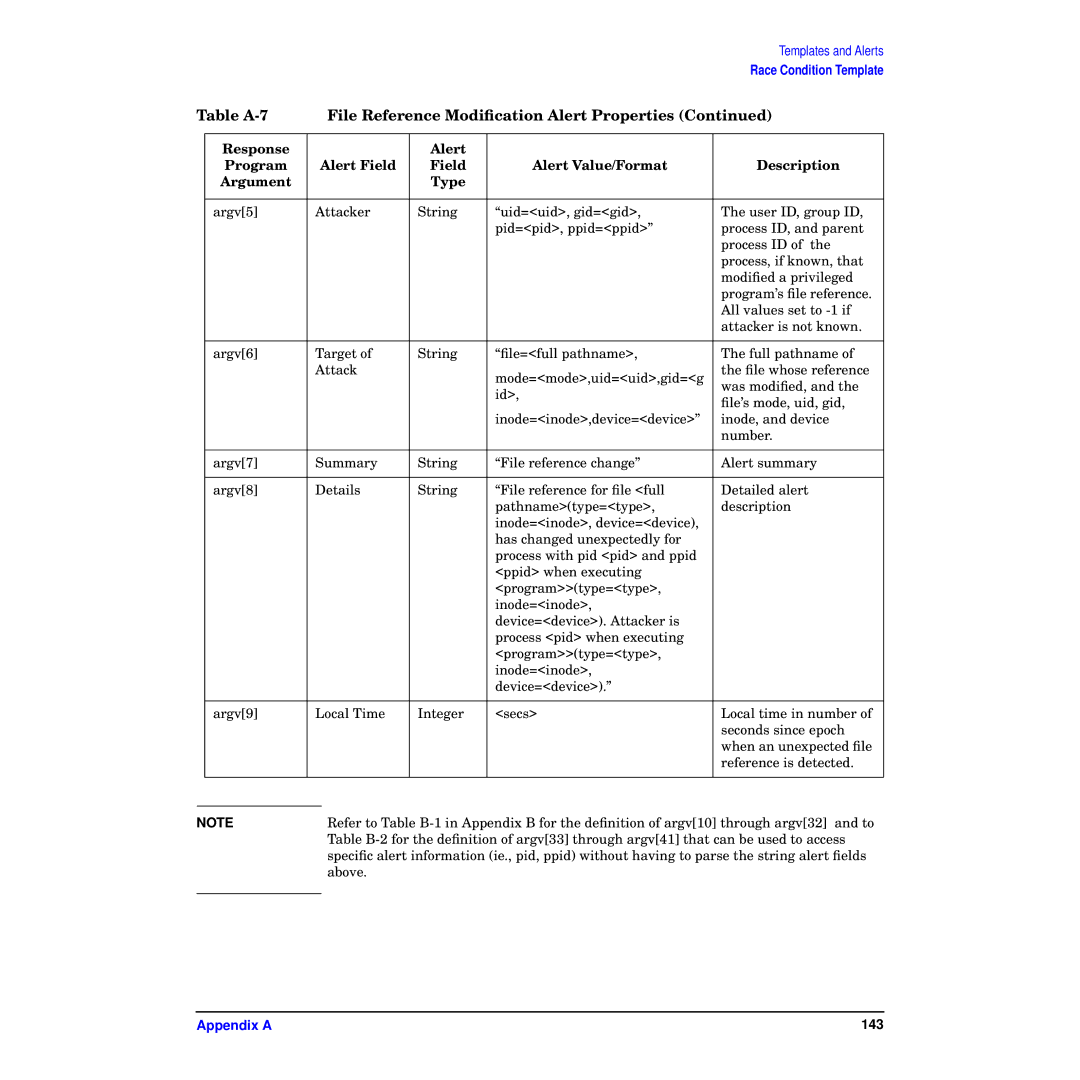
| File Reference Modification Alert Properties (Continued) | ||||
|
|
|
|
|
|
|
| Response |
|
| Alert |
|
|
| Program | Alert Field | Field | Alert Value/Format | Description | |
| Argument |
|
| Type |
|
|
|
|
|
|
|
| |
| argv[5] | Attacker | String | “uid=<uid>, gid=<gid>, | The user ID, group ID, | |
|
|
|
|
| pid=<pid>, ppid=<ppid>” | process ID, and parent |
|
|
|
|
|
| process ID of the |
|
|
|
|
|
| process, if known, that |
|
|
|
|
|
| modified a privileged |
|
|
|
|
|
| program’s file reference. |
|
|
|
|
|
| All values set to |
|
|
|
|
|
| attacker is not known. |
|
|
|
|
|
| |
| argv[6] | Target of | String | “file=<full pathname>, | The full pathname of | |
|
| Attack |
| mode=<mode>,uid=<uid>,gid=<g | the file whose reference | |
|
|
|
|
| was modified, and the | |
|
|
|
|
| id>, | |
|
|
|
|
| file’s mode, uid, gid, | |
|
|
|
|
|
| |
|
|
|
|
| inode=<inode>,device=<device>” | inode, and device |
|
|
|
|
|
| number. |
|
|
|
|
|
| |
| argv[7] | Summary | String | “File reference change” | Alert summary | |
|
|
|
|
|
| |
| argv[8] | Details | String | “File reference for file <full | Detailed alert | |
|
|
|
|
| pathname>(type=<type>, | description |
|
|
|
|
| inode=<inode>, device=<device), |
|
|
|
|
|
| has changed unexpectedly for |
|
|
|
|
|
| process with pid <pid> and ppid |
|
|
|
|
|
| <ppid> when executing |
|
|
|
|
|
| <program>>(type=<type>, |
|
|
|
|
|
| inode=<inode>, |
|
|
|
|
|
| device=<device>). Attacker is |
|
|
|
|
|
| process <pid> when executing |
|
|
|
|
|
| <program>>(type=<type>, |
|
|
|
|
|
| inode=<inode>, |
|
|
|
|
|
| device=<device>).” |
|
|
|
|
|
|
| |
| argv[9] | Local Time | Integer | <secs> | Local time in number of | |
|
|
|
|
|
| seconds since epoch |
|
|
|
|
|
| when an unexpected file |
|
|
|
|
|
| reference is detected. |
|
|
|
|
|
|
|
|
|
| Refer to Table | |||
NOTE |
| |||||
|
|
| Table | |||
|
|
| specific alert information (ie., pid, ppid) without having to parse the string alert fields | |||
|
|
| above. |
|
|
|
|
|
|
|
|
|
|
Appendix A | 143 |