|
|
|
|
| Templates and Alerts |
|
|
|
|
| Race Condition Template |
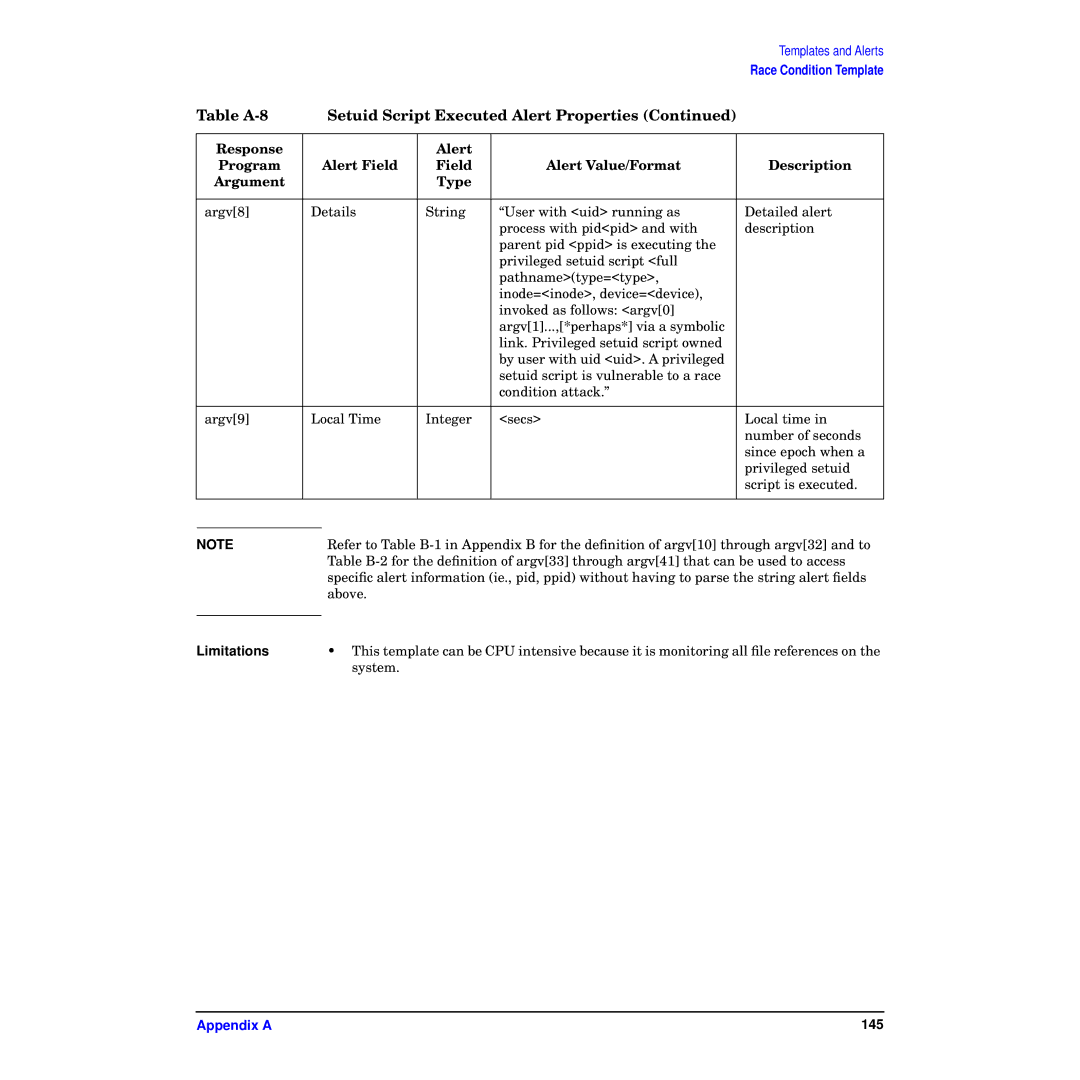
Table |
| Setuid Script Executed Alert Properties (Continued) |
| ||
|
|
|
|
|
|
Response |
|
| Alert |
|
|
Program |
| Alert Field | Field | Alert Value/Format | Description |
Argument |
|
| Type |
|
|
|
|
|
|
| |
argv[8] | Details | String | “User with <uid> running as | Detailed alert | |
|
|
|
| process with pid<pid> and with | description |
|
|
|
| parent pid <ppid> is executing the |
|
|
|
|
| privileged setuid script <full |
|
|
|
|
| pathname>(type=<type>, |
|
|
|
|
| inode=<inode>, device=<device), |
|
|
|
|
| invoked as follows: <argv[0] |
|
|
|
|
| argv[1]...,[*perhaps*] via a symbolic |
|
|
|
|
| link. Privileged setuid script owned |
|
|
|
|
| by user with uid <uid>. A privileged |
|
|
|
|
| setuid script is vulnerable to a race |
|
|
|
|
| condition attack.” |
|
|
|
|
|
| |
argv[9] | Local Time | Integer | <secs> | Local time in | |
|
|
|
|
| number of seconds |
|
|
|
|
| since epoch when a |
|
|
|
|
| privileged setuid |
|
|
|
|
| script is executed. |
|
|
|
|
|
|
|
| Refer to Table | |||
NOTE |
| ||||
|
| Table | |||
|
| specific alert information (ie., pid, ppid) without having to parse the string alert fields | |||
|
| above. |
|
|
|
|
| • This template can be CPU intensive because it is monitoring all file references on the | |||
Limitations |
| ||||
|
| system. |
|
|
|
Appendix A | 145 |