Templates and Alerts
Creation of
| Creation of |
The vulnerability | A world writable file is one that any user of the system can modify. In many cases, the |
addressed by this | files owned by the system users (such as root, bin, sys, adm) are used to control the |
template | configuration and operation of the system. Allowing regular users to modify these files |
| exposes the system to attacks. A world writable directory containing system files allows |
| an attacker to replace these files. |
How this template | The World Writable (WW) template detects the creation of a world writable file owned by |
addresses the | a privileged user. Specifically, the template monitors for the following, where a file can be |
vulnerability | a regular file, directory, or special file: |
| • Creation of a file that has the world writable bit set and owned by a privileged user. |
| • Modification of the file permissions that enables the world writable bit for an |
| existing file owned by a privileged user. |
| • Changing the ownership of an existing world writable file to be owned by a |
| privileged user. |
| • Renaming of a world writable file owned by a privileged user whose old pathname |
| was in the template’s pathnames_to_not_watch property and whose new pathname |
| is not in the pathnames_to_not_watch property. |
How this template This template supports the following properties: is configured
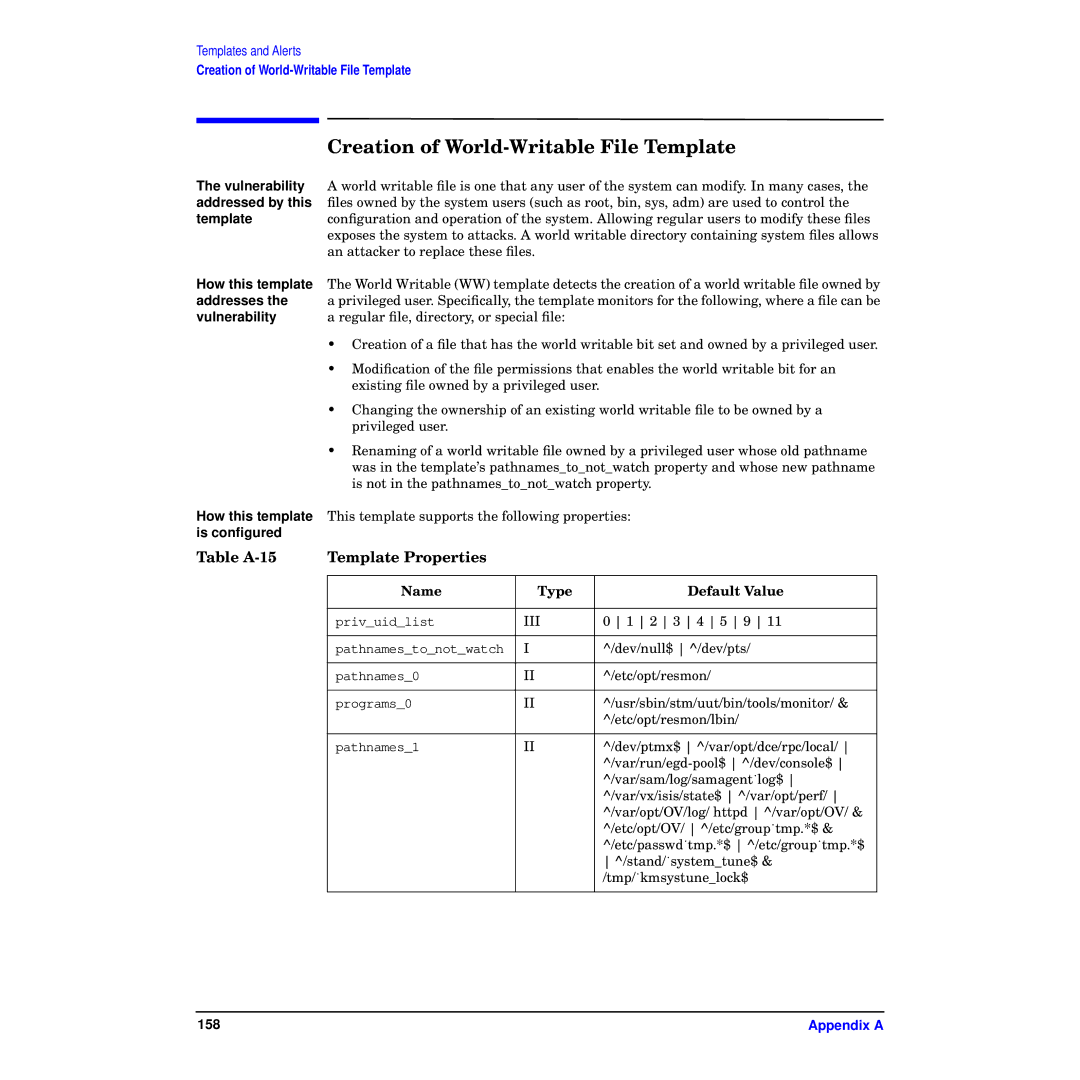
Table | Template Properties |
|
|
|
|
|
|
| Name | Type | Default Value |
|
|
|
|
| priv_uid_list | III | 0 1 2 3 4 5 9 11 |
|
|
|
|
| pathnames_to_not_watch | I | ^/dev/null$ ^/dev/pts/ |
|
|
|
|
| pathnames_0 | II | ^/etc/opt/resmon/ |
|
|
|
|
| programs_0 | II | ^/usr/sbin/stm/uut/bin/tools/monitor/ & |
|
|
| ^/etc/opt/resmon/lbin/ |
|
|
|
|
| pathnames_1 | II | ^/dev/ptmx$ ^/var/opt/dce/rpc/local/ |
|
|
| |
|
|
| ^/var/sam/log/samagent˙log$ |
|
|
| ^/var/vx/isis/state$ ^/var/opt/perf/ |
|
|
| ^/var/opt/OV/log/ httpd ^/var/opt/OV/ & |
|
|
| ^/etc/opt/OV/ ^/etc/group˙tmp.*$ & |
|
|
| ^/etc/passwd˙tmp.*$ ^/etc/group˙tmp.*$ |
|
|
| ^/stand/˙system_tune$ & |
|
|
| /tmp/˙kmsystune_lock$ |
|
|
|
|
158 | Appendix A |