Automated Response
How Automated Response Works in
2.Your program is detached from a controlling terminal and runs as a background process. Standard output and standard error are both redirected to the error log file, as defined by the IDS_ERRORFILE configuration variable (the default is
/var/opt/ids/error.log.)
3.If you need to transmit your alert information to another system, you may need to set up your own secure communication process.
4.If your response program has its setuid or setgid bit set, it will run as that effective user or group. It is a good practice to restrict setuid and setgid programs to the absolute minimum necessary. See “Writing Privileged Response Programs” on page 190.
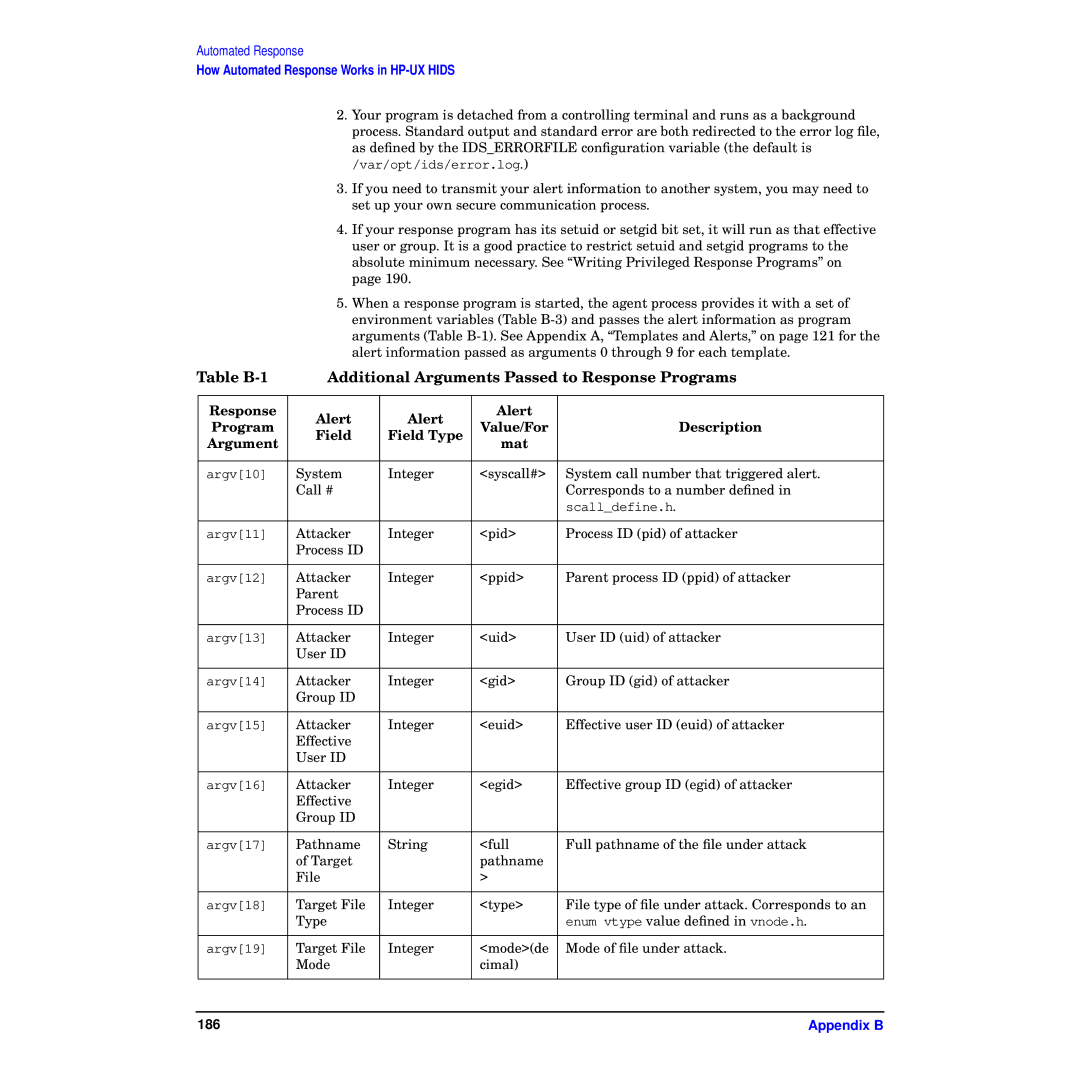
5.When a response program is started, the agent process provides it with a set of environment variables (Table
Table | Additional Arguments Passed to Response Programs | ||||
|
|
|
|
| |
Response | Alert | Alert | Alert |
| |
Program | Value/For | Description | |||
Field | Field Type | ||||
Argument | mat |
| |||
|
|
| |||
|
|
|
|
| |
argv[10] | System | Integer | <syscall#> | System call number that triggered alert. | |
| Call # |
|
| Corresponds to a number defined in | |
|
|
|
| scall_define.h. | |
|
|
|
|
| |
argv[11] | Attacker | Integer | <pid> | Process ID (pid) of attacker | |
| Process ID |
|
|
| |
|
|
|
|
| |
argv[12] | Attacker | Integer | <ppid> | Parent process ID (ppid) of attacker | |
| Parent |
|
|
| |
| Process ID |
|
|
| |
|
|
|
|
| |
argv[13] | Attacker | Integer | <uid> | User ID (uid) of attacker | |
| User ID |
|
|
| |
|
|
|
|
| |
argv[14] | Attacker | Integer | <gid> | Group ID (gid) of attacker | |
| Group ID |
|
|
| |
|
|
|
|
| |
argv[15] | Attacker | Integer | <euid> | Effective user ID (euid) of attacker | |
| Effective |
|
|
| |
| User ID |
|
|
| |
|
|
|
|
| |
argv[16] | Attacker | Integer | <egid> | Effective group ID (egid) of attacker | |
| Effective |
|
|
| |
| Group ID |
|
|
| |
|
|
|
|
| |
argv[17] | Pathname | String | <full | Full pathname of the file under attack | |
| of Target |
| pathname |
| |
| File |
| > |
| |
|
|
|
|
| |
argv[18] | Target File | Integer | <type> | File type of file under attack. Corresponds to an | |
| Type |
|
| enum vtype value defined in vnode.h. | |
|
|
|
|
| |
argv[19] | Target File | Integer | <mode>(de | Mode of file under attack. | |
| Mode |
| cimal) |
| |
|
|
|
|
| |
186 | Appendix B |