SANbox2-64 Fibre Channel Switch Installation Guide
Document Revision History
SANbox2-64 Fibre Channel Switch Installation Guide
Table of Contents
Section Planning
Section Installation
Devices Multiple Chassis Fabrics
Site Requirements Fabric Management Workstation
Section Diagnostics/Troubleshooting
Appendix a Specifications
Section Removal/Replacement
Command Syntax
Appendix B Command Line Interface
Glossary Index
Zone Command Zoneset Command 101 Zoning Command 104
Serial Port Pin Identification
Tables
Page
Intended Audience
Introduction
Related Materials
Sicherheitshinweise
Safety Notices
Federal Communications Commission FCC Class a Statement
Communications Statements
CE Statement
Bsmi Class a Statement
Vcci Class a Statement
Electrostatic Discharge Sensitivity Esds Precautions
Laser Safety Information
Zugängliche Teile
Accessible Parts
Pièces Accessibles
Preamble
General Public License
12.2
Introduction General Public License
Introduction General Public License
Introduction General Public License
No Warranty
How to Apply These Terms to Your New Programs
Copyright C yyyy name of author
Availability
Technical Support
Training
Contact Information
General Description
Chassis Hardware
SANbox2-64 64-Port Fibre Channel Switch
Slot and Fibre Channel Port Numbering
Chassis Controls and LEDs
Maintenance Button
Placing the Switch in Maintenance Mode
Resetting a Switch
Fan Fail LED Amber
Over Temperature LED Amber
Chassis LEDs
Fibre Channel Ports
Input Power LED Green
Heartbeat LED Amber
Small Form-Factor Pluggable SFP Transceivers
Port Status LED
Fabric Ports
Port Modes
Expansion Port
Ethernet Port
Ethernet Port
Serial Port
Pin Number Description
Serial Port Pin Identification
Power Supply Components
Power Supply Modules
10. Fans
Fans
Switch Management
Devices
Planning
Single Switch Fabric with Initiators and Targets
Dual Switch Fabric with Initiators and Targets
Domain ID, Principal Priority, and Domain ID Lock
Multiple Chassis Fabrics
Common Topologies
Distance
Performance
Latency
Bandwidth
Port-to-Port Transmission Combinations
Port-to-Port Latency
Device Access
Soft Zones
Access Control List Hard Zones
Virtual Private Fabric Hard Zones
User Account Security
Fabric Security
Device Security
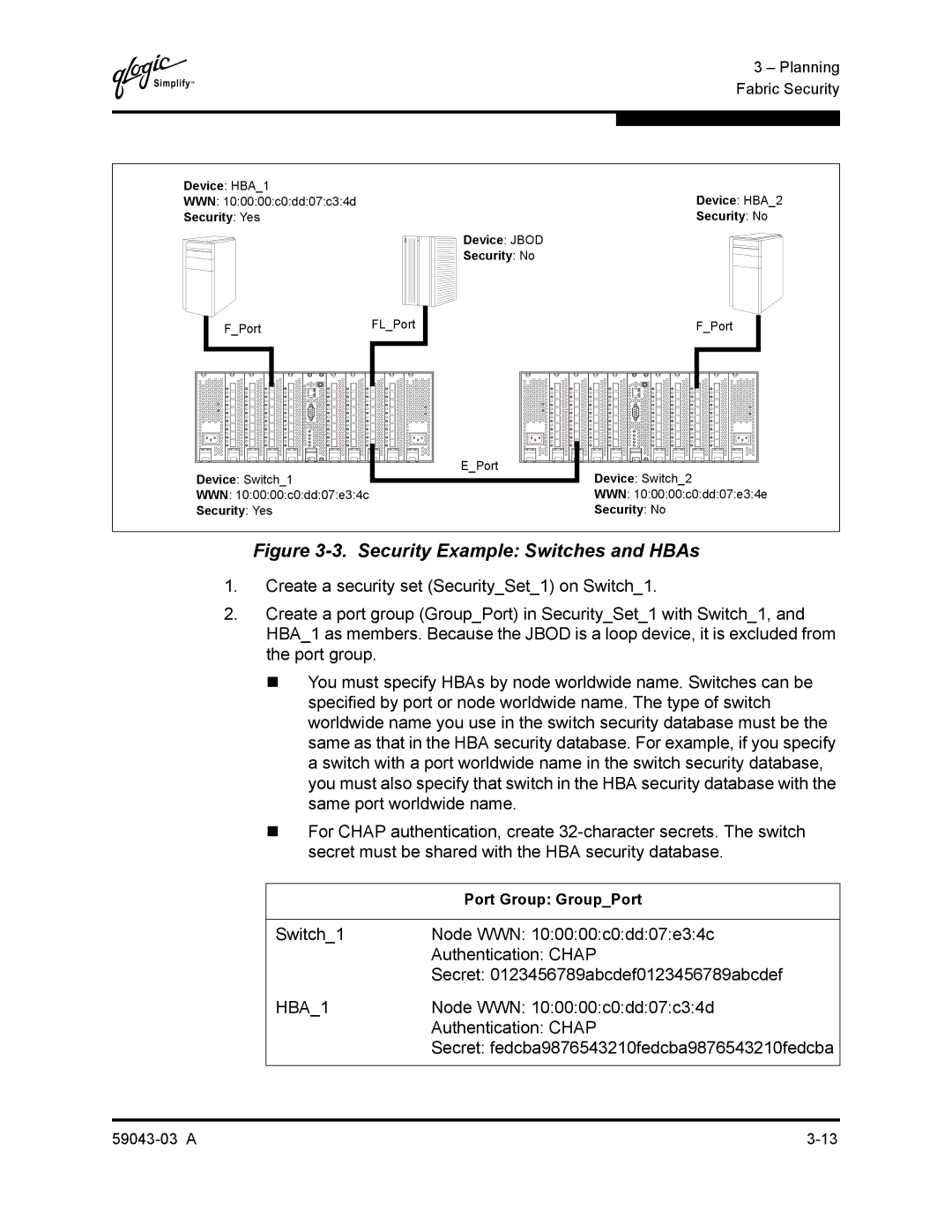
Security Example Switches and HBAs
Secret fedcba9876543210fedcba9876543210fedcba
Node WWN 100000c0dd07c34d
Node WWN 100000c0dd 07e34e
Create a security set SecuritySet2 on Switch2
Security Example Host Authentication
MS Group Group1
Fabric Management
Fabric Services
Planning Fabric Management 59043-03 a
Site Requirements
Switch Power Requirements
Fabric Management Workstation
Management Workstation Requirements
Environmental Conditions
Installing a Switch
Avertissement
Mount the Switch
„ If the switch is mounted in a closed or multi-unit rack
Locked prior to applying power to the switch
Assembly, make sure that the operating temperature inside
Rack for service access and ventilation
SANbox2-64 Rail Kit
Connect the Switch to AC Power
Install SFP Transceivers
Avertissement
Appendix a Specifications
Ethernet and Serial Cable Connections
Connect the Management Workstation to the Switch
Serial Connection
Ethernet Connection
Enter the following command at the Solaris prompt
Install SANbox Manager
SANsurfer Management Suite Disk Linux Installation
SANsurfer Management Suite Disk Windows Installation
Enter the following command
SANsurfer Management Suite Disk Solaris Installation
SANbox2 Installation Disk Windows Installation
Configure the Switch
SANbox2 Installation Disk Linux Installation
SANbox2 Installation Disk Solaris Installation
Cable Devices to the Switch
Configure the Ports
Using SANbox Manager to Install Firmware
Install Firmware
Enter the following command to install the new firmware
Using the CLI to Install Firmware
To start an admin session, enter the following
Close the FTP session
Using FTP and the CLI to Install Firmware
Powering Down a Switch
Normal all pass
Post Diagnostics
Heartbeat LED Blink Patterns
Fatal Error Blink Pattern
Maintenance Mode Pattern
Configuration File System Error Blink Pattern
To recreate the configuration file, do the following
Ftp Ftp switchname
Reset the switch and close the Telnet session
Enter the following account name and password userimages
Restore the configuration file
Port Status LED Indications
Logging Error
EPort Isolation
Excessive Port Errors
Diagnostics/Troubleshooting Post Diagnostics
Chassis and Power Supply LEDs
Chassis Diagnostics
Fan Fail LED is Illuminated
Over Temperature LED is Illuminated
Input Power LED Is Extinguished
Power Supply Fault LED is Illuminated
Output Power LED Is Extinguished
Recovering a Switch
Maintenance Image Unpack
Maintenance Exit
Maintenance Reset Password File
Maintenance Reset Network Config
Maintenance Copy Log Files
Maintenance Remove Switch Config
Maintenance Set Active Image
Maintenance Show Firmware Versions
Diagnostics/Troubleshooting Recovering a Switch 59043-03 a
SFP Transceivers
Marginal Operating Configurations
Removing the CPU Module
CPU Module
Removal/Replacement CPU Module
Removing the CPU Module
Installing the CPU Module
Ftp put imagefile
Removal/Replacement CPU Module
Choose the Replace task
Blades
Disconnect all cables from the selected I/O blade
Choose the slot number 6 for example
Removing an I/O Blade
To install a new I/O blade, enter y
Removal/Replacement I/O Blades
CC Blade Slots
Cross-Connect Blades
Removing a CC Blade
Switch Cover Removal
Installing a CC Blade
Installing a CC Blade
Avertissement
Removing a Power Supply Module
Removing a Power Supply Module
Installing a Power Supply Module
Removing a Fan
Removing a Fan
Installing a Fan
Installing a Fan
Fabric Specifications
Maintainability
Electrical
Dimensions
Environmental
Regulatory Certifications
Shortwave Laser SFP 1G/2G multi-mode
Longwave Laser SFP 1G/2G single-mode
Page
Logging On to a Switch
Command Line Interface
Table B-1. Command-Line Completion
Command Syntax
Table B-2. Commands Listed by Authority Level
Commands
Authority
Admin Command
Syntax
Keywords
Syntax alias
Alias Command
Rename aliasold aliasnew
Members alias
Remove alias memberlist
Syntax config
Config Command
Keywords activate config
Edit config
Archive function are not compatible with the Config Restore
Restore
Command
Save config
# ftp symbolicname or ipaddress
Keywords MMDDhhmmCCYY
Date Command
Syntax date
Fallback
Fallback Command
Syntax group
Group Command
Keywords add group
Table B-3. Group Member Attributes
Create group type
Copy groupsource groupdestination
Edit group member
Table B-4. Group Member Attributes
Following is an example of the Group List command
Following is an example of the Group Edit command
Members group
Remove group members
Following is an example of the Group Members command
Pending firmware and disrupts traffic
Hardreset Command
Hardreset
Keywords command
Help Command
Syntax help command keyword
Authority None
Following is an example of the Help Set Beacon command
Authority None Syntax history
History Command
Hotreset
Hotreset Command
Fabric is in the diagnostic operational state
This command clears the event log and all counters
Hotswap
Hotswap Command
To replace? 1,2,3,4,6,7,8,9 1
Cleanup
Image Command
Image
Fetch accountname ipaddress filesource filedestination
Lip Command
Changes a user account’s password
Passwd Command
Passwd accountname
Accountname
Authority None Syntax Ping
Ping Command
Ipaddress
Keywords ipaddress
Following is an example of the Ps command
Ps Command
Syntax Examples
Displays current system process information
Syntax quit, exit, or logout
Quit Command
Closes the Telnet session
Config configname
Reset Command
Table B-5. Switch Configuration Defaults
Switch
System
Zoning
Mfstov
Table B-6. Port Configuration Defaults
Table B-8. Zoning Configuration Defaults
Table B-7. Alarm Threshold Configuration Defaults
Table B-9. Snmp Configuration Defaults
Table B-11. Security Configuration Defaults
Table B-10. System Configuration Defaults
Keywords active
Security Command
Clear
Edit
History
Following is an example of the Security History command
Limits
Save
Following is an example of the Security List command
Following is an example of the Security Limits command
Securityset Command
Groups securityset
Delete securityset
Remove securityset group
Rename securitysetold securitysetnew
Syntax set
Set Command
Switch state
Setup option
Log option
Pagebreak state
Table B-12. Set Config Port Parameters
Set Config Command
Keywords blade slotnumber
Port portnumber
Send Arbff True instead of IDLEs
Table B-12. Set Config Port Parameters
Table B-13. Security Configuration Parameters
Table B-14. Set Config Switch Parameters
Threshold
Table B-15. Set Config Threshold Parameters
Memory. Refer to FC-SW-2 Compliant
Table B-16. Set Config Zoning Parameters
Arbff
Following is an example of the Set Config Port command
Following is an example of the Set Config Switch command
Following is and example of the Set Config Security command
Following is an example of the Set Config Threshold command
This
Following is an example of the Set Config Zoning command
Set log
Set Log Command
Archive
Component list
Port portlist
Level level
Stop
Start
Stops logging of events
Level keyword to Info at the same time
Set Port Command
Snmp configuration and one system configuration
Set Setup Command
Set setup
Table B-17. Snmp Configuration Settings
Table B-18. System Configuration Settings
SANbox2 admin # set setup snmp
Trap1Severity See
SANbox2 admin # set setup system
Following is an example of the Set Setup System command
Alarm
Show Command
Keywords about
Blade
Ns option
Fdmi nodewwn
Log option
Panel
Pagebreak
Perf option
Table B-19. Show Port Parameters
LIP Alpd Alps
Slot slotnumber
Post log
Support
Steering domainid
Topology
Users
Following is an example of the Show Chassis command
Following is an example of the Show Panel command
Following is an example of the Show Domains command
Following is an example of the Show Fabric command
Following is an example of the Show NS local domain command
Following is an example of the Show Fdmi command
Following is an example of the Show Fdmi WWN command
Following is an example of the Show Interface command
Following is an example of the Show NS domainID command
Following is an example of the Show NS portID command
LIPF8F7
Following is an example of the Show Port command
Following is an example of the Show Slot command
Following is an example of the Show Topology command
Following is an example of the Show Switch command
Command Line Interface Show Command
Following is an example of the Show Version command
Blade slotnumber
Show Config Command
Show config
Following is an example of the Show Config Threshold command
Following is an example of the Show Config Switch command
Following is an example of the Show Config Zoning command
Keywords component
Show Log Command
Following is an example of the Show Log command
Following is an example of the Show Log Options command
Show Perf Command
Following is an example of the Show Perf Byte command
Errors portnumber
Mfg
Show Setup Command
Show setup
Following is an example of the Show Setup Snmp command
Following is an example of the Show Setup System command
Shutdown
Shutdown Command
Power from the switch
Test
Test Command
Port portnumber testtype
Status
Test port x internal
Command Line Interface Test Command
Authority None Syntax uptime
Uptime Command
Examples The following is an example of the Uptime command
Keywords accounts
User Command
Add
Delete accountname
Following is an example of the User Edit command
Following is an example of the User Add command
Following is an example of the User List command
Following is an example of the User Delete command
Whoami
Whoami Command
Following is an example of the Whoami command
Syntax zone
Zone Command
Remove zone memberlist
Members zone
Rename zoneold zonenew
Type zone zonetype
Following is an example of the Zone Members command
Following is an example of the Zone Zonesets command
Syntax zoneset
Zoneset Command
Remove zoneset zonelist
Following is an example of the Zoneset List command
Rename zonesetold zonesetnew
Zones zoneset
Following is an example of the Zoneset Zones command
Opens a Zoning Edit session
Zoning Command
Following is an example of the Zoning Limits command
E2JBOD2
Following is an example of the Zoning List command
59043-03 a 107
Command Line Interface Zoning Command 108 59043-03 a
Administrative State
Access Control List Zone
BootP
Class 2 Service
Configured Zone Sets
Class 3 Service
Default Visibility
Fabric Management Switch
Inter-Switch Link
Input Power LED
Maintenance Button
Maintenance Mode
Over Temperature LED
Output Power LED
Power On Self Test Post
Principal Switch
Virtual Private Fabric Zone
User Account Security
Worldwide Name WWN
Zone
Page
Numerics
Index
Index-2 59043-03 a
59043-03 a Index-3
Index-4 59043-03 a
59043-03 a Index-5
Index-6 59043-03 a
59043-03 a Index-7

![]() E_Port
E_Port ![]()
![]()
![]()
![]()
![]()
![]() Device: Switch_1
Device: Switch_1