Cisco BTS 10200 Softswitch Operations and Maintenance Guide
Americas Headquarters
Cisco BTS 10200 Softswitch Operations and Maintenance Guide
N T E N T S
Introduction
Using Show and Change Commmands
IUA Measurements
FIM/XML B-1
Viii
Introduction
Organization
Issue Date Status Reason for Change
Document Change History
Preface Introduction
Xii
Meeting Power Requirements
Starting BTS Hardware
Starting BTS Software
Shutting Down BTS Hardware
Log in as root
Starting and Shutting Down the BTS Starting BTS Software
OL-16000-07
Logging into the EMS Using CLI
Username Permission
Supply a default password
Task Sample Command
Managing Users
Differ from the users login name and any combination
Changing a user’s password
Password must
Login name
CLI FTP Corba Snmp
Managing Commands
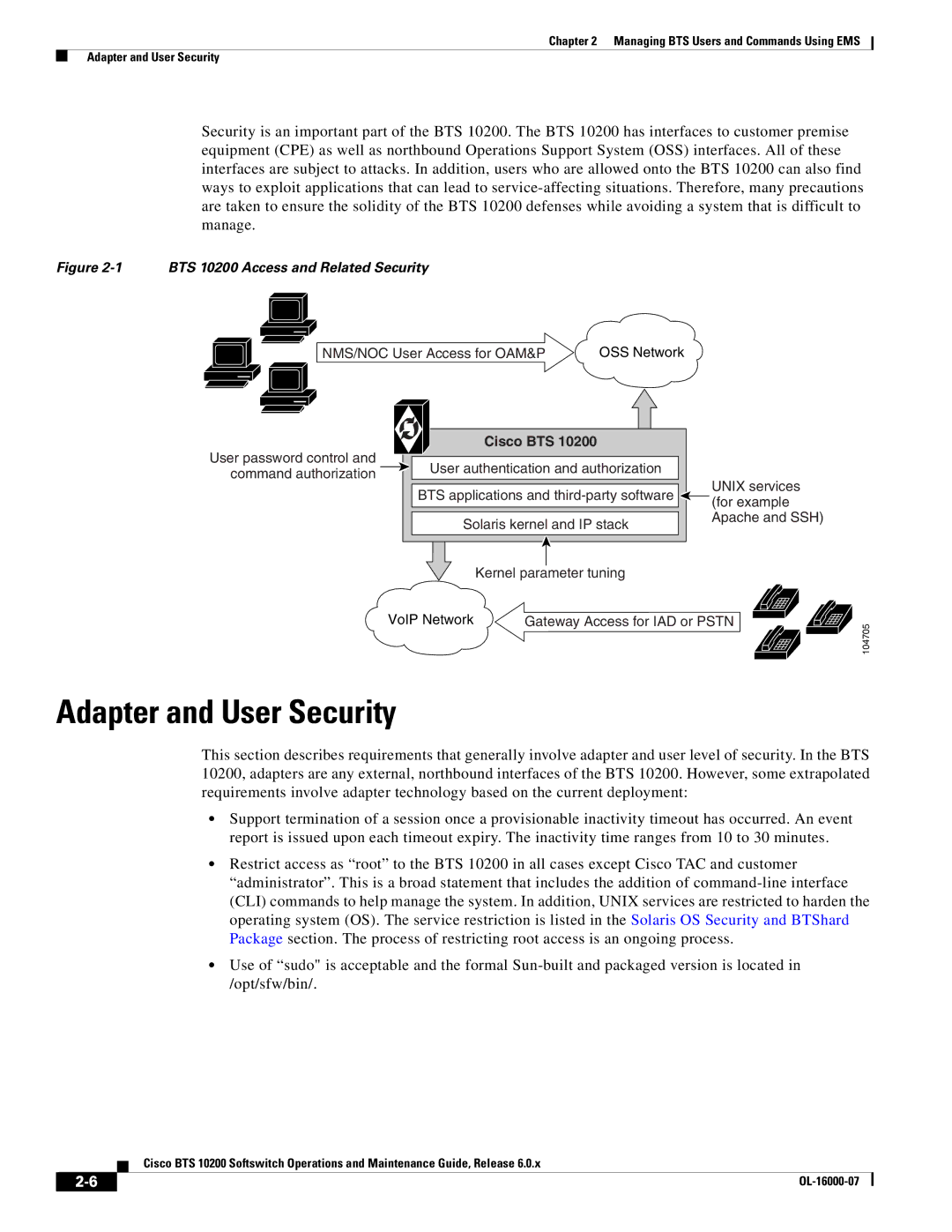
Adapter and User Security
Cisco BTS
Solaris OS Security and BTShard Package
Ipignoreredirect=1
Ipforwarddirectedbroadcasts=0
Ipforwardsrcrouted=0
Ipireflushinterval=60000
Iprespondtotimestampbroadcast=0
Iprespondtoechobroadcast=1
Iprespondtotimestamp=0
Ipsendredirects=0
Operator Interface
S88sendmail S93cacheos.finish S99dtlogin
Noun Verb Options Description
Authentication, Authorization and Accounting Support
Vulnerabilities in H.323 Message Processing
User Security Account Management
Sun Microsystems Configurations
Pluggable Authentication Module Support
Package Description Type Status
SUNWdfb Dumb Frame Buffer device drivers
SUNWfruid FRU ID prtfru Command and libfru library
SUNWfruip FRU ID Platform Data module and Access
SUNWensqr Ensoniq ES1370/1371/1373 Audio device driver
Solaris OS Patches
Trace Normal Forms TNF Support
Security CE Patch
XML Libraries
Device GLM Patch
Security BadTrap Patch
Managing BTS Users and Commands Using EMS Solaris OS Patches
Detecting and Preventing BTS Congestion
This chapter includes overall BTS maintenance strategies
Monitoring BTS Hardware
Checking BTS System Health
Tasks Frequency
Using BTS System-Health Reports
Checking the OS Log of Each Host Machine
Checking BTS System Time
For more history edit the /var/adm/messages file
CA/FS Side a
Checking Disk Mirroring on Each Host Machine
CA/FS Side B
EMS Side a
Log in as root to EMS side a using telnet
Log in as root to EMS side B using telnet
EMS Side B
Auditing Databases and Tables
Verify the return result matches the following
Exporting Provisioned Data
Termination record points to an invalid mgw
############################## ##### Add featureserver #####
Limitations
Data Groups Matching Data from the DN2SUBSCRIBER Table
Administrative did DNs
Changed Number administrative DNs
Monitoring and Backing Up the BTS Exporting Provisioned Data
DN=0-9xxx status=assigned
DN=xxxx status=assigned
DN=xxxx status=ported-out
DN=0-9xxx status=ported-out
Ndc=npa ec=nxx DN=0-90-90-90-9 status=CN
Ndc=npa ec=nxx ADMIN-DN=Y and status=PORTED-OUT
Backing Up the Software Image
Ndc=npa ec=nxx DN=0-90-9xx status=DISC X
Checking Shared Memory
Full Database Auditing
From CA/FS Side a
From CA/FS Side B
Result match the following
Backing Up the CA/FS
Pre-Provisioning Checklist
Backing Up the Full BTS
Opt/OptiCall/CAxxx/bin/logs
Backing up the EMS/BDMS
Where xxx is the instance number Back up the system, enter
From the active EMS switch over all platforms, enter
Unmount the NFS server, enter
Backing up the EMS Database
Using FTP to Setup File Transfer
Optional Enable the oraarchbackup.ksh process
Oracleorainst1675 Mar 10 1542 idrsa
Using Sftp to Setup File Transfer
Opt/oraback EMS systems Opt/backup Remote FTP system
# su oracle # /opt/BTSossh/bin/ssh-keygen -t rsa
Monitoring and Backing Up the BTS Exporting Provisioned Data
Crontab -e
Archiving Your Database
Oraoragrp394 Mar 10 1648 idrsa.pub
Mount 10.89.183.253/opt/archive /mnt
Unmount the NFS server. Enter umount /mnt
Examining Heap Usage
Checking the DNS Server
To check the DNS server, do this for all nodes
Log in as root on the active CA Enter more /etc/resolv.conf
Log Archive Facility LAF
Secure Transfer of Files
Enter nslookup
Provisioning LAF
Other Capabilities
Enabling LAF Process
Setup Non-Interactive SSH Login to External Archive Server
Execute cd /opt/BTSossh/bin Execute ssh-keygen -t rsa
Moving Core Files
LAF Alarm Information
After editing, close the file, and run S96StaticRoutes
Parameter Condition
Operating the BTS
Managing Subscribers
Vmwi
Changing Delete the changed-number entry Subscribers
Announcements
Changing Change the subscriber DN to the new DN Subscribers
Table is not updated with the changed number information
Use the show subscriber command to verify the new DN
DNs
Query call-trace subscriberDN/FQDN/NPA-NXX-****/aaln/*@
Viewing Calls
Report call-trace-summary
Status Viewing component
Using Status and Control Commands
Viewing BTS system
Use status application for more detailed information
EMS, BDMS, CA Activestandby Standbyactive
OOS
Subscriber-related
Using Show and Change Commmands
Using Erac Commands
Usage statistics
Tasks Descriptions Examples
Distance Command the subscriber ID field or the new
Viewing speed This command returns a list of all speed dial
Dial settings by Telephone numbers by the specified DN or
Subscriber or This command the subscriber id field or
Managing Transactions
ACTIVETARGET=Y STATUS=PENDING
Scheduling Commands
FTP, Corba
Commands
Commands Changing scheduled
Viewing scheduled
Managing External Resources
Viewing BTS System-Wide Status
EMS
Fsain
Fsptc
Bdms
Managing Trunk Groups and Trunks
Target-state=ins mode=forced
Reset trunk-termination tgn-id=13 cic=1-6
Control trunk-termination tgn-id=17 cic=1-23
Equip trunk-termination tgn-id=13 cic=all
Diag isdn-trunk-termination test=TAB
Diag ss7-trunk-termination test=TAB
Diag ss7-trunk-termination test=RETURN
Diag isdn-trunk-termination test=RETURN
State/Token
Uneqp ANY Ueqp Idle Manually OOS Lblk Manually Main Maint
Status
Specific to the command
Command Entered Response Possible Conditions
Control
Command Entered Response Possible Conditions
Command Entered Response Possible Conditions
OL-16000-07
Command Entered Response Possible Conditions
Checking subscriber
Managing Subscriber Terminations
Status in detail
MNT-Maintenance mode
INS-In-service
OOS-Out of service
Forces Maint state, do this before testing
Subscriber is down, the subscriber cannot be added
Graceful mode only, this appears when a command is executed
Operation is INS going OSS or INS going Maint
An assigned resource is not valid supported. For example, a
Command Entered Response Possible Conditions
Managing Gateways
Viewing media gateway test
Testing media gateways
Changing media gateways
Menus
Status sip-reg-contact
Graceful mode only. Appears when a command is executed
Managing Other External Resources
Aor-id=4695551885@SYS44CA146.boston3.com
Viewing subsystems status
Shows all Cmts Aggr-ID
Viewing subsystems
Changing subsystem status
CLIshow billing-acct-addr
Learning External Resource Dependencies
Yyyymmdd-hhmmss-sequence-number-S
State Definition
Unreachable
Unknown
Active
Ctrans
Faulty
Mtrans
Reserved
Source Token
SL = Ueqp Pins SL
TRK = OOS TGP = OOS
OL-16000-07
Provisioning the GigE Interface
GigE Support
Prerequisites
Shut No shut
Ca102 dladm show-dev
OL-16000-07
Using BTS Measurements
Using Measurements
Siptotalsuccessincomingmsg
Learning the Measurement Types
Isdn Measurements
Isdnalertingrx
Isdncallproceedtx
Isdnocsetuprejected
Isdncallproceedrx
Isdncongcntltx
Isdnsetuprx
Isdnsetupackrx
Isdnsetupacktx
Isdnsetuptx
Call Processing Measurements
Callpinterlaaband
CALLPH323TERMATTMP
CALLPH323TERMFAIL
Callpinterlaattmp
Ported Callplnpunallocnum N
Callplnpsndmisrouted
Ported Callplnpsndmisrouted
Ogap
Succ Callpnasadminreboot
Callpmodemmediasetup
Fail Callpmodemmediasetup
Callpnasadminreset
Callpolm ACCEPTMCL0
Callpohddialtonetimeo
Callpolm Accept
Callpolm ACCEPTMCL1
Callpsiporigfail
Callpsiporigcallnota
Callpsiporigendusrbu
Callpsiporigsucc
Callptddmediasetupsu
CALLPT38FAXMEDIASETUP
Succ Callptddmediasetupfai
CALLPSS7TERMATTMP
Mgcp Adapter Measurements
DQoS Measurements
SIP Measurements
Sisackrx
Siscancelrx
Siscanceltx
Sisacktx
Sisupdaterx
SIST1TIMEREXPIRED
SIST2TIMERREACHED
Sisupdatetx
Service Interaction Manager Measurements
Pots Local FS Measurements
Potsccwrejectnorsrc
Potsccwlength
Potsccwrejectbyccw
Potscfbactattmp
Potscfuactrefused
Potscfuactanswered
Potscfuactattmp
Potscfuactsecond
Potscwrejectnorsrc
Potscwattmp
Potscwnotanswered
Potscwrejecteinteract
Potsextcnamquerysucc
Potsocbinvalidpassword
Potsextcnamquery
Potsmdcattmp
Potsracfrefuse
Potsracfpinrejectnorsrc
Potsracfpinunchange
Potsracfrejectnorsrc
Pots Application Server Measurements
Pots Miscellaneous FS Measurements
Potshotvdeactsucc
Potsvmaccess
Potshotvattmp
Potshotvinterrogsucc
Pots Class of Service FS Measurements
Pots Screen List Editing FS Measurements
Pots Customer Originated Trace FS Measurements
Potsacdeactattmp
Potsacdelayedproc
Potsacactattmp
Potsacdeactbysystem
Potsarinterlataattmp
Potsardelayedproc
Potsarimmediateproc
Potsaroverflow
Pots Call Forwarding Combination Measurements
AIN Services FS Measurements
AINSVCLOC8XXFAILAPP
AINSVCLOC8XXANIBLOCK
AINSVCLOC8XXDNISSUCC
AINSVCLOC8XXIIBLOCK
Sccp Protocol Measurements
Sccptotallongudatasvcrx
Sccptotallocalmsg
Sccptotallongudatarx
Sccptotallongudatasvctx
Tcap Protocol Measurements
Tcapdupinvokeidtx
Tcapdialogconfirmrx
Tcapdupinvokeidrx
Tcapendmsgrx
Tcapoperationconfirmrx
Tcapopenconfirmrx
Tcapopenindrx
Tcapoperationindrx
Rsprx Tcapunexpectlink
Tcapunexpectlink
Operrx Tcapunexpectlinkopertx
Rsptx Tcapunexpectrerx
SUA Measurements
Suaroutingcontexterr
Suasincelastresetassoc
Suaprotocolerr
Suasconrx
M3UA Protocol Measurements
M3UASCONRX
M3UASINCELASTRESETASSOC
M3UAROUTINGCONTEXTERR
M3UASCONTX
Sctp Measurements
Sctpinvalidstreamerrrx
Sctpinvalidparamerrrx
Sctpinvalidstream
Sctpinvalidveriftag
Sctpunresolvaddrerrrx
Sctpunrecogchunkerrrx
Sctpunrecogparamerrrx
SCTPV6ADDRPARAMRX
IUA Measurements
Measurement Description
Iuanomemoryerr
Iuamsgothererr
Iuamsgtypeerr
Iuanotifyrx
Isup MeasurementsI
Isupcpgtx
Isupcottx
Isupcpgrx
Isupcqmrx
Isupidrrx
Isupiamrx
Isupiamtx
Isupidrtx
Kong Chile Australia Israel ETSIv2 Hungary
Hong
China
Poland
Message Measurements Applicable to Isup Variants
UBL Ucic
Isup Ansi Measurements
Sgacvttx
Sgacvrtx
Sgacvtrx
Sgaexmrx
Sgaublrx
Sgaubarx
Sgaubatx
Sgaubltx
Isup Poland Measurements
Isup France Measurements
Isup ITU-China Measurements
Sgaoprrx
Sgaconrx
Sgacontx
Sgaoprtx
Description
Isup ITU-Mexico Measurements
Sgagrarx
Isup ITU-HongKong Measurements
Sganrmtx
Sganrmrx
NRM messages sent on the reporting trunk group
Audit Measurements
SIP Interface Adapter Measurements
Siamwinotifytx
Siatotalsesstimerfail
Siamwinotifyrx
Siamwinotifytxfail
Call Detail Block Measurements
Billingtotalpcs
Billingtotalop
Billingtotalopassist
Billingtotalpolice
Event Messaging Measurements
Dynamic QoS Measurements
Pcmm Measurements
Snmp Protocol Measurements
Trunk Group Usage Measurements
Trkgrpoutgattmp
Trkgrpoutboundfail
Trkgrpoutboundsucc
Trkgrpoutgbusytrk
Trkgrpueqptrkusage
Trkgrptotalinstrk
Trkgrptotaloostrk
Trkgrptotaloverflow
Announcement Measurements
Protocol Measurements
H323INPROGRESSRX
H323ALERTTX
H323ALERTFAIL
H323INPROGRESSTX
H323PASSTHROURX
H323NOTIFYTX
H323NOTIFYFAIL
H323PASSTHROUTX
H323URJRX
H323OCSETUPREJECTED
H323UCFTX
H323URJTX
AIN Tools Measurements
Call Tools Measurements
PCT Tools Measurements
Network I/O Usage Measurements
CPU Usage Measurements
Memory Usage Measurements
Disk Usage Measurements
Diskusagetotalused
Diskusagetotalavailable
Blocks on file system
Used blocks
System Load Usage Measurements
Disk I/O Usage Measurements
Diameter Message Counters
Single Number Reach Counters
Counter Label Counter Context
Managing User Access to the Snmp Agent
Viewing Snmp Trap Reports
Task Operation
Debug Info Minor Major Critical
MGW
Viewing and Managing BTS Components
GET/GETNEXT
SGP
SET
Enabling NMS to Query/Poll Solaris Snmp Agent
Querying the Snmp Agent
IPCELL-TC
Output appears as given below
Snmpwalk -c public -p 13230 prica07 system
OL-16000-07
Tones per Feature
Feature Tone Conditions That Initiate Tone1
CW Type
CW Tone
Cidcw
Stutter Tone
CFNA-ACT
CFU-ACT Stutter Tone
CFU-DEACT Confirmation Tone
CFNA-DEACT
Cidb Cids COS Confirmation Tone
Cndb Dial Tone
Cnab
COS Confirmation Tone
MDN Alerting Pattern
DPU Stutter Tone
Drcw Alerting Pattern
MWI MWI Tone
SC2D-ACT
Tone Frequencies and Cadences
SC1D-ACT Stutter Tone
Vmwi Stutter Tone
Tone Frequency Hz Description
OL-16000-07
Understanding the Configurable FIM/XML Feature
FIM/XML
Tool Requirements
Advantages of the FIM/XML Tool
Writing an External FIM/XML File
Defining Features
Elements in the External FIM/XML File
Lists the attributes in the Define Element
Define Element
Precedence-Exception Element
Required Description
Inhibit Me Element
Inhibit Others Element
Response Profile Element
Error
Installing the FIM/XML File Using the Offline FIM/XML Tool
Fcp-features feature name=E911 inhibition-allowed=false
Java -jar fimxml.jar param1 param2 param3 param4
Install fimxml filename=absolutepath
Run the following Java application
Opt/OptiCall/etc/fimxml/FSPTC235/FIMXMLRules.xml
Parameters
Features Defined in FIM/XML and Shared iFC
FIM/XML File and Shared iFC File
Shared iFC
Provisioning iFC
Defining a New feature as the Originating Feature
Feature Configuration
Defining a VSC
Subscriber-Service-Profile
Feature Restrictions and Limitations
Service-Id
Subscriber-Sip-Trigger-Profile
OL-16000-07