MES-2110
Page
Intended Audience
About This Users Guide
Customer Support
Syntax Conventions
Document Conventions
Telephone Router
MES-2110 Computer Server
Dslam
Firewall
Safety Warnings
Safety Warnings MES-2110 User’s Guide
Contents Overview
Contents Overview MES-2110 User’s Guide
Table of Contents
Chapter System Details
10.1
Igmp
137
Chapter Command Line Interface 179
Index 229
Table of Contents MES-2110 User’s Guide
Introduction
Overview
Backbone Application
Backbone Application
Bridging Example
Ieee 802.1Q Vlan Application Examples
High Performance Switching Example
Metro Ethernet
Shared Server Using Vlan Example
Metro Ethernet
Ways to Manage the MES-2110
Good Habits for Managing the MES-2110
Hardware Installation and Connection
Installation Scenarios
Desktop Installation Procedure
Mounting the MES-2110 on a Rack
Rack-mounted Installation Requirements
Attaching the Mounting Brackets
Attaching the Mounting Brackets to the MES-2110
Mounting the MES-2110 on a Rack
Mounting the MES-2110 on a Rack
Front Panel
Hardware Overview
Label Description
Console Port
Gigabit Ethernet Ports
Front Panel Connections
Mini-GBIC Slots
Default Ethernet Negotiation Settings
Transceiver Installation
Removing the Fiber Optic Cables
Power Connections Overview
DC Power Connection
AC Power Connection
LED Color Statu Description
Powering on the MES-2110
LEDs
LED Descriptions
Mbps Ethernet network
Green Blinking
Igmp Snooping
Tutorials
Set Igmp Query Mode to Auto
Radius Configuration
Tutorials
Tutorials
Based802.1q before proceeding
MVR Configuration
Setting Value
MVR Tutorial Values
Open the Configuration Igmp Menu MVR screen
Tutorials
Vlan ID Priority
For Pri-Overide, select Enable
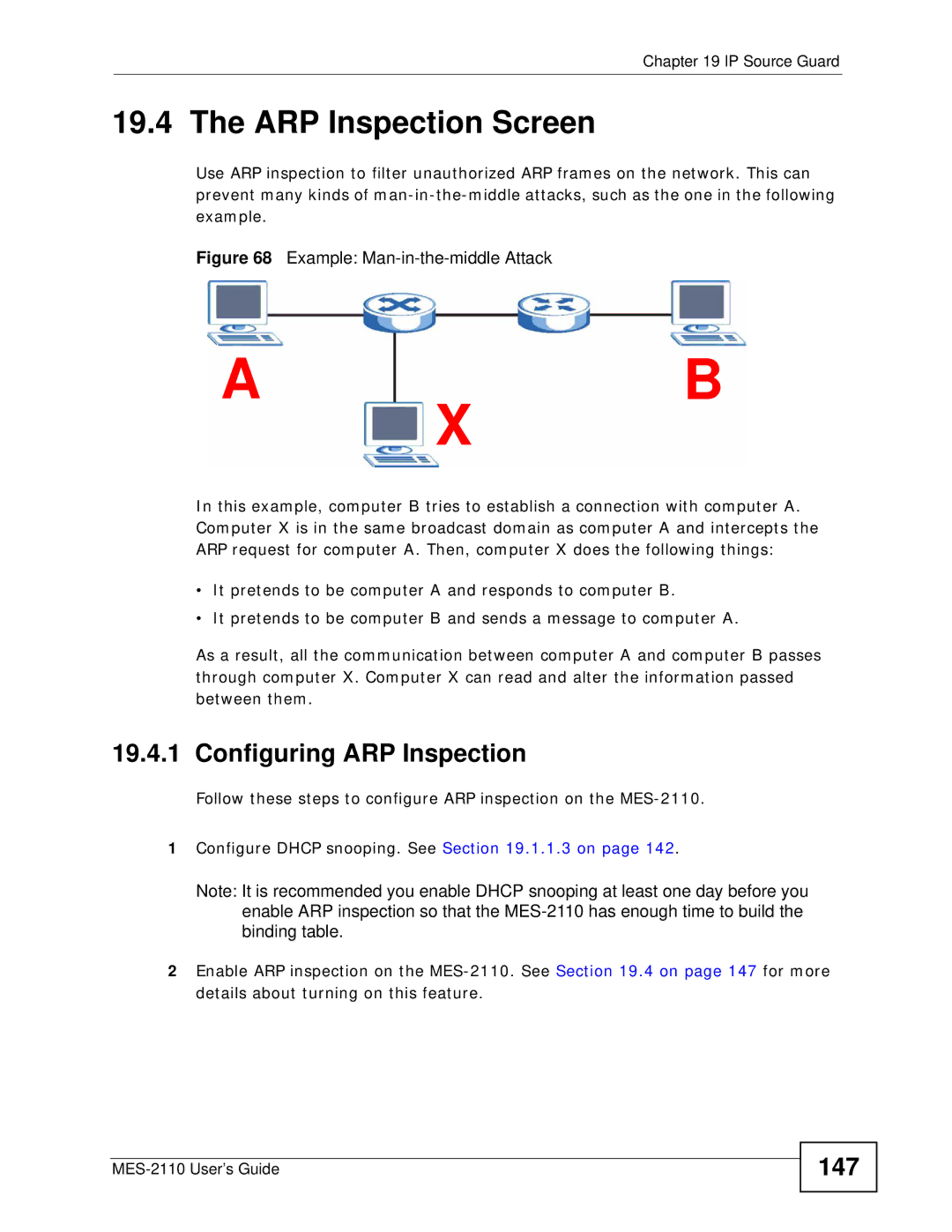
Untrusted ARP Inspection
Set Action to Enable and Dhcp Snooping Vlan Mode to All-VLAN
Outgoing Traffic Bandwidth
Frame Tagging Example
Frame Tagging
To configure frame tagging
Tutorials MES-2110 User’s Guide
Web Configurator
System Login
Introduction
Web Configurator Login
Main Screen
Web Configurator Main Screen
Navigation Panel Sub-links Overview
System Details Configuration Mgmt Config System Restart Menu
Sntp
Web Configurator Screen Sub-links Details
System Details Configuration Mgmt Config Restart Menu
Snmp
Navigation Panel Links
Link Description
Dhcp
ARP
Saving Your Configuration
Set Up the Administrative Password
Made on the MES-2110 and restart the MES-2110
Switch Lockout
Resetting the MES-2110
Reload the Configuration File
Resetting the MES-2110 Via the Console Port
System Information Screen
System Details
Board Information Screen
Undo Click this to restore your last saved settings Apply
Dhcp Configuration Screen
Address, subnet mask and a default gateway IP address
IP address from a Dhcp server if Dhcp client is enabled
System Details Dhcp Config Apply
Port Configuration Screen
Configuration
Auto
Truncated in some Web Configurator screens
Manage the MES-2110 via that port
Duplex This indicates the port’s duplex mode Half or Full
Disabled
Port Status Screen
This shows whether auto-negotiation is On or Off
Rmon Status Screen
RX+TX
Configuration Rmon Status
Loop Detection
Switch in Loop State
Loop detection Probe Frame
Loop Detection Screen
Down this port
Snmp traps when it shuts down a port via the loop detection
Feature
Enabled, the MES-2110 sends probe frames from this port to
Loop Detection MES-2110 User’s Guide
Jumbo Frame Configuration Screen
Jumbo Frame
Frame Size
Jumbo Frame MES-2110 User’s Guide
802.1x
Ieee 802.1x Authentication
Guest Vlan
Ieee 802.1x Authentication Process
10.2 802.1x Global Configuration Screen
Port Number 1812 Server
10.3 802.1x Radius Server Configuration Screen
MES-2110. The key is not sent over the network
Server UDP
Before configuring it on each port
10.4 802.1x Port Configuration Screen
Guest Vlan
Reauthenticat
Clients for port access
10.5 802.1x Radius Server Configuration Screen
Radius vs. TACACS+
Technical Reference
Radius and TACACS+
Supported Radius Attributes
Attributes Used for Authenticating Privilege Access
Attributes Used for Authentication
Radius Attributes Exec Events via Telnet/SSH
Attribute Start INTERIM-UPDATE Stop
Attributes Used for Accounting
Radius Attributes Exec Events via Console
Radius Attributes-Exec Events via
Attributes Used for Accounting Ieee 802.1x Events
802.1x MES-2110 User’s Guide
Link Recommended Allowed Speed Value Range
Bridge
STP Terminology
STP Path Costs
Path 16Mbps 40 to Cost 100Mbps 10 to 1Gbps 10Gbps
How STP Works
Port Description State
Bridge Configuration Screen
STP Port States
STP Port States
Tunnel port receives Bridge Protocol Data Units Bpdu
Rstp System Configuration Screen
Are done configuring
You select Rstp 802.1W in the Ring Protocol field
List box
Same priority, the switch with the lowest MAC address will
Determines Hello Time, Max Age and Forwarding Delay
Root Bridge Information
Network. The allowed range is 6 to 40 seconds
Allowed range is 4 to 30 seconds
As a general rule
Selected from among the MES-2110 ports attached to
Spanning Tree Port Configuration
255 and the default value is
Cost 1~65535 Enter the port’s path cost
P2P
CFI Vlan ID
Introduction to Ieee 802.1Q Tagged VLANs
Tpid
User Priority
Vlan
Forwarding Tagged and Untagged Frames
Ieee 802.1Q Vlan Terminology
Vlan Term Description Parameter
Vlan Type Screen
Port-Based Vlan Screen
Vlan Type Use this to set the MES-2110 to Port-Based or Tag
Connected to this port
Port-Based Vlan Configuration
Then you cannot access the web configurator from a computer
100
101
Tag-Based Vlan Screens
Vlan Stacking
Vlan Stacking Example
102
Vlan Stacking Port Roles
Type Priority
Vlan Tag Format
103
Vlan Tag Format
802.1Q Frame
Frame Format
104
Single and Double Tagged 802.11Q Frame Format
Vlan Stacking Configuration Screen
105
SP Tpid
Spvid
106
Tag-Based Port Information Screen
107
Pvid
Select whether you want to Add or Modify a Vlan ID
Tag-Based Port Configuration Screen
Enter the Vlan ID from 1-4094 that you want to configure
108
109
Management Vlan Screen
Unless your current access belongs to the new Vlan
110
Management Vlan This is the current management Vlan
Bandwidth Control Setup
Bandwidth Control
111
112
Broadcast Storm Control Setup
Broadcast Storm Control
113
Storm Control Configuration
114
Storm Control Status
Port Mirroring Setup
Port Mirroring
115
Volatile memory when you are done configuring
116
Select the monitor port number from the list
Link Aggregation
Dynamic Link Aggregation
117
Link Aggregation ID
Link Aggregation ID Local Switch
Link Aggregation ID Peer Switch
Static Trunking Example
119
Link Aggregation Setting
Link Aggregation Control Protocol
120
Lacp
Lacp Link Status
121
MAC
122
IP Multicast Addresses
Igmp Snooping
123
Igmp Configuration
Igmp Snooping and VLANs
124
Igmp Vlan
125
126
Igmp Vlan Query Mode
Igmp Status
MVR Overview
127
Types of MVR Ports
MVR Modes
How MVR Works 128
129
General MVR Configuration
Disable to turn this feature off
130
Select Dynamic to send Igmp reports to all MVR source ports
131
MVR Group Configuration
MVR Group Status
Group Configuration
132
Drop-down list box
133
MVR Configuration Example
134
135
MVR Group Configuration Example
136
Relay Agent Information
Dhcp Relay Configuration
Dhcp Relay Agent Information
137
To a Dhcp server
Dhcp Relay Configuration
138
Bytes This is the Vlan that the port belongs to
Option82 Information
139
140
141
IP Source Guard
142
Dhcp Snooping Overview
143
Dhcp Snooping Configuration
Dhcp requests will not succeed
144
Mode VLANs or specific VLANs to Dhcp servers Dhcp Snooping
Dhcp Binding Table
145
Ddhhmm
146
Configuring ARP Inspection
ARP Inspection Screen
147
Addresses permanently
148
149
150
151
MAC
152
MAC Table Status Screen
153
Undo Click this to load your last saved settings Apply
MES-2110 or static manually configured
Lock MAC Address Learning Screen
To activate MAC address learning on the port
MAC Filter Configuration Screen
154
Port This is the port number Lock
155
Aged out. MAC address aging out time can be set in the MAC
MAC Limit Configuration Screen
Addresses may access port 2 at any one time. a sixth device
156
QoS Base Configuration Screen
QoS
157
158
Configuring the Base Configuration Screen
159
160
802.1p Priority Table
Number This is the Ieee 802.1p priority level Priority
Tag Priority Table
IP Dscp Priority Table
161
162
Configuration QoS Menu IP Dscp Priority
163
Priority Override Configuration Screen
164
Mgmt Config and System Restart Menu
Serial Port Configuration Screen
165
166
Snmp Configuration Screens
IP Trap Manager Screen
Snmp Commands
Command Description
Snmp Communities Screen
Sntp Screen
168
Traps to
169
170
Alarms and Logs
Syslog
171
172
User Configuration Screen
Characters using characters found on a standard keyboard
User Password
Cable Test Screen
173
PHY RX/TX
Host DoS Protection
174
Test
Port Abnormal Traffic Detection Screen
175
Fields below
176
Upgrading the Firmware
177
Managing the Configuration File
178
Restarting the System
Logging
Command Line Interface
Setting Default Value
Console Port Management
180
Using Shortcuts and Getting Help
Command / Keys Description
Saving Changes
Logging Out
Command Modes
Exit Command
Basic Commands
182
Basic Commands
Privileged Command Mode
Privileged Commands
183
184
Permanently save any changes you
Make while using the MES-2110
Command line interface
185
Ancillary Trigger Description
Configuration Mode
Configuration Mode Commands
186
187
188
189
190
Address over Telnet
191
192
193
Igmp Snooping Example
194
Radius Configuration Example
195
MVR Mode
MVR-Configuration Mode Commands
This command to work
196
MVR Command Example
Vlan Mode
Vlan Mode Commands
197
Interface Mode
Vlan ID Priority Example
198
199
Interface Mode Commands
200
201
Second tag to pass through it
202
Port, the port must allow frames
Bytes 1522 bytes + 4 bytes for
203
Sets the service provider Vlan ID of the current Ports
Untrusted ARP Inspection Example
Outgoing Traffic Bandwidth Limit Example
204
Frame Tagging Examples
205
206
Troubleshooting
Power, Hardware Connections, and LEDs
207
208
MES-2110 Access and Login
Advanced Suggestions
209
Pop-up Windows, JavaScript and Java Permissions
210
211
MES-2110 Configuration and Console
212
My changes in the Web Configurator keep getting overwritten
213
214
215
Product Specifications
Hardware Specifications
Specification Description
Firmware Specifications
Feature Description
216
217
218
Standards Supported
Standard Description
Installing a Fuse
Removing a Fuse
219
220
221
Common Services
Commonly Used Services
222
Name Protocol Ports Description
223
224
Copyright
Certifications
225
FCC Warning CE Mark Warning
226
227
ZyXEL Limited Warranty
228
229
Index
230
TACACS+
MVR 127 configuration
Password 58 path cost 89, 93 port authentication
231
232
Weighted round robin scheduling