NBG-460N
Page
User Guide Feedback
About This Users Guide
Intended Audience
Related Documentation
About This Users Guide
Syntax Conventions
Document Conventions
Dslam
Telephone Switch Router Modem
Icons Used in Figures
NBG-460N Computer Server
Safety Warnings
Safety Warnings NBG-460N User’s Guide
Contents Overview
Contents Overview NBG-460N User’s Guide
Table of Contents
Chapter Connection Wizard
Part II Network
WAN
177
Part IV Management
235
Part V Maintenance and Troubleshooting 261
Part VI Appendices and Index
Table of Contents NBG-460N User’s Guide
Part
Page
Overview
Getting to Know Your NBG-460N
Applications
NBG460N
Wireless Applications
Router Mode
LAN
3 AP + Bridge
AP Mode
AP + Bridge Application
Bridge
Bridge Application
Bridge Loop Two Bridges Connected to Hub
Router vs. AP vs. Bridge
Features Available in Router Mode vs. AP Mode
Feature Router AP Mode Bridge
Ways to Manage the NBG-460N
Front Panel LEDs
Power
Good Habits for Managing the NBG-460N
LEDs
Wlan
Wireless LAN Off Wireless LAN is not ready or has failed
This feature Off Device is in normal power mode
WAN
Getting to Know Your NBG-460N NBG-460N User’s Guide
WPS Button
WPS Button NBG-460N User’s Guide
Web Configurator Overview
Introducing the Web Configurator
Accessing the Web Configurator
Change Password Screen
Navigating the Web Configurator
Resetting the NBG-460N
Procedure to Use the Reset Button
Status Screen Icon Key
Status Screen in Router Mode
Icon Description
Dhcp
Label Description
Scheduler
Memory Usage
Wlan is disabled
When the line is disconnected
Is enabled and N/A when the Wlan is disabled
LAN
Navigation Panel
Screens Summary
Link TAB Function
Mgmt
NAT
Ddns
VPN
Logs View Log
Mode As a Router or a Access Point Language
Summary Any IP Table
Summary Bandwidth Management Monitor
Summary BW Mgmt Monitor
Summary Dhcp Table
Host Name field
Summary Packet Statistics
This is the security association index number
Summary VPN Monitor
Intervals field
Stop Click Stop to stop refreshing statistics
NBG-460N’s Wlan network
Summary Wireless Station Status
This is the index number of an associated wireless station
Association Time
Introducing the Web Configurator NBG-460N User’s Guide
Connection Wizard
Wizard Setup
System Name
Connection Wizard System Information
Underscores are accepted
Domain Name
Ssid
Connection Wizard Wireless LAN
Use the same Ssid in order to access the network
This option is only available if WPS is not enabled
Wizard Basic WEP Security
Basic WEP Security
HEX
Extend WPA-PSK or WPA2-PSK Security
WEP
Ascii
Do this
Connection Wizard Internet Configuration
Pre-Shared
Key
Pptp
Ethernet Connection
PPPoE Connection
Connection Description Type
Pptp Connection
ISP Parameter for Internet Access
Wizard Pptp Connection
ISP Parameters for Internet Access
Provided by your ISP
Your IP Address
WAN IP Address Assignment
Use fixed IP address
Private IP Address Ranges
IP Address and Subnet Mask
10.0.0.0 172.16.0.0 192.168.0.0
WAN IP and DNS Server Address Assignment
DNS Server Address Assignment
WAN IP Address Assignment
WAN MAC Address
Choose an IP address
Wizard WAN MAC Address
Connection Wizard Bandwidth management
Wizard Bandwidth Management
Connection Wizard Complete
Connection Wizard Complete
Connection Wizard NBG-460N User’s Guide
Tutorials
How to Connect to the Internet from an AP
Internet
Push Button Configuration
NBG460N
Example WPS Process PIN Method
Pre-Shared Key ThisismyWPA-PSKpre-sharedkey
SSIDExample3
Channel Security
WPA-PSK
Tutorial Status AP Mode
Configure Your Notebook
Connecting a Wireless Client to a Wireless Network
Link Status
Using AP + Bridge Mode and WDS
Configuring Your Bridge Mode Settings
Pre-Shared Key ThisismyWPA2-PSKpre-sharedkey
WPA2-PSK
Setting BOB’S NBG-460N JACK’S NBG-460N
Site-To-Site VPN Tunnel Settings
Site-To-Site VPN Tunnel Tutorial
Tutorial Property
Configuring Bob’s NBG-460N VPN Settings
Tutorial Authentication Method
Configuring Jack’s NBG-460N VPN Settings
Tutorial Property
Tutorial Authentication Method
Pinging Jack’s Local IP Address
Checking the VPN Connection
Bandwidth Management for your Network
Configuring Bandwidth Management by Application
Configuring Bandwidth Allocation by IP or IP Range
Configuring Bandwidth Management by Custom Application
Fields Services Real Audio Rtsp VDO Live FTP
Refer to Appedix F on the Bandwidth Mgnt
Setting your NBG-460N to AP Mode
AP Mode
Status Screen
Status AP Mode
Schedules
Display Network Wireless LAN WPS screen
System Setting Configuration Mode
This shows the LAN port’s Dhcp role Client or None
Or connected
Menu AP Mode
Mask or to get the LAN IP address from a Dhcp server
Maintenance System General
Setting Logs View Log
Reset the factory defaults to your NBG-460N
LAN Settings
Configuring Your Settings
Sys OP General
Table below describes the labels in the screen
Wlan and Maintenance Settings
Logging in to the Web Configurator in AP Mode
Network
Page
Example of a Wireless Network
Wireless LAN
What You Can Do
Wireless Security Overview
What You Should Know
Ssid
Weakest Stronges t
Types of Encryption for Each Type of Authentication
No Authentication Radius Server
100
Printable 7-bit Ascii characters for the wireless LAN
General Wireless LAN Screen
101
Select Static WEP , WPA-PSK , WPA , WPA2-PSK or WPA2 to add
No Security
102
WPA-PSK and WPA2-PSK are available in this field
103
WEP Encryption
104
Select 64-bit WEP or 128-bit WEP to enable data encryption
WEP keys and displays them in the Key fields below
Hex
105
AP or peer computer
Correct WEP key
Priority
Server, the reauthentication timer on the Radius server has
Security Mode field
106
107
4 WPA/WPA2
108
Server, the reauthentication timer on the Radius server
Has priority
109
MAC Filter Screen
MAC
110
RTS/CTS
Wireless LAN Advanced Screen
Quality of Service QoS Screen
111
You want to apply WMM QoS
112
On page 123 for more information
WMM QoS Policy
Configuration screen
Application Priority Configuration
113
Mail
114
User-Defined
115
WPS Screen
Push Button
WPS Station Screen
Scheduling Screen
116
Day
117
Whole day
Following times fields
118
WDS Screen
Between the NBG-460N and any wireless clients
Security Mode Static WEP
119
ASCII/HEX
120
121
Security Mode WPA2-PSK
Technical Reference
Roaming
Roaming Example
122
123
Quality of Service
WMM QoS Priorities
WiFi Protected Setup
IPod Touch Web Configurator
124
125
Login Screen
126
System Status
WAN connection is not working
127
MBM
128
Port Forwarding
WPS in Progress
129
Rule is turned on
130
Turn the rule OFF
Accessing the iPod Touch Web Configurator
Accessing the iPod Touch Web Configurator
131
132
LAN and WAN
133
What You Need To Know
Configuring Your Internet Connection
134
135
Multicast
WAN MAC Address
136
Iptv STB Port
192.168.1.20
137
You have one STB
You have two STBs
Auto-Bridge
NetBIOS over TCP/IP
138
Ethernet Encapsulation
Internet Connection
139
WAN MAC
140
Address
Defined changes to None after you click Apply
Select Clone the computers MAC address IP Address and enter
Setting or upload a different ROM file
PPPoE Encapsulation
141
142
All of the LANs computers will have access
Different ROM file
143
DNS Servers First DNS
Computer’s
144
Pptp Encapsulation
Pptp connection
145
146
Advanced WAN Screen
Select Clone the computers MAC address IP Address
Select Igmp V-1,IGMP V-2 or None
147
148
When the NBG-460N gets a WAN IP address that is not
To be in Router Mode for the Iptv STB port to work
Igmp
149
LAN
150
IP Pool Setup
LAN IP Screen
LAN TCP/IP
151
LAN IP Alias
LAN TCP/IP
IP address that you assign. Unless you are implementing
Any IP Setup
Advanced LAN Screen
152
153
LANs, WANs and the ZyXEL Device
154
Any IP
155
156
157
Dhcp
Dhcp Advanced Screen
Dhcp General Screen
158
Must have their DNS server addresses manually configured
Select the Enable Dhcp Server check box. When you clear
159
Select DNS Relay to have the NBG-460N act as a DNS proxy.
NBG-460Ns system DNS server configured in the WAN Internet
Client List Screen
160
Them
161
This is the index number of the host computer
Host names. After you click Apply, the MAC address and IP
162
163
Network Address Translation NAT
General NAT Screen
Enable Network
Select the check box to enable NAT
Default Server Setup
165
NAT Application Screen
166
167
Wake On LAN is enabled
Fields under Add Application Rule
Game List Example
Configuring Servers Behind Port Forwarding Example
168
169
NAT Advanced Screen
170
Users may not be able to access the Internet
Can establish through the NBG-460N
Traffic to a server on the WAN
LAN that requested the service
Trigger Port Forwarding Example
171
172
Two Points To Remember About Trigger Ports
DynDNS Wildcard
Dynamic DNS
173
Dynamic DNS Screen
Enable Dynamic Select this check box to use dynamic DNS
174
WAN IP address
175
176
177
Part
178
179
Firewall
Triangle Routes
About the NBG-460N Firewall
180
181
Triangle Routes and IP Alias
General Firewall Screen
Services Screen
182
Icmp
183
Add Firewall Rule screen
184
Single IP is selected as the Address Type
Add Firewall Rule Screen
185
Pool
186
Click Clear All to empty the Blocked Services
Address Type
187
188
Content Filtering Profiles
Content Filtering
189
Days and Times
Restrict Web Features
190
Keyword Blocking URL Checking
191
Filter Screen
Allowed
192
Cookies
Web Proxy
Not affected
Which content filtering will be enforced
Schedule Screen
193
Full Path URL Checking
Customizing Keyword Blocking URL Checking
194
Domain Name or IP Address URL Checking
195
IPSec VPN
196
IKE SA IKE Phase 1 Overview
Local Network and Remote Network
IPSec SA IKE Phase 2 Overview
197
IP Addresses of the NBG-460N and Remote IPSec Router
198
General Screen
199
VPN Rule Setup Basic
200
Feature to work
201
Enabled
Secure Gateway Address field set to
202
203
Your computer in the Local Content field. The NBG-460N
With dynamic WAN IP addresses
Address field refer to the Secure Gateway Address field
204
205
VPN Rule Setup Advanced
206
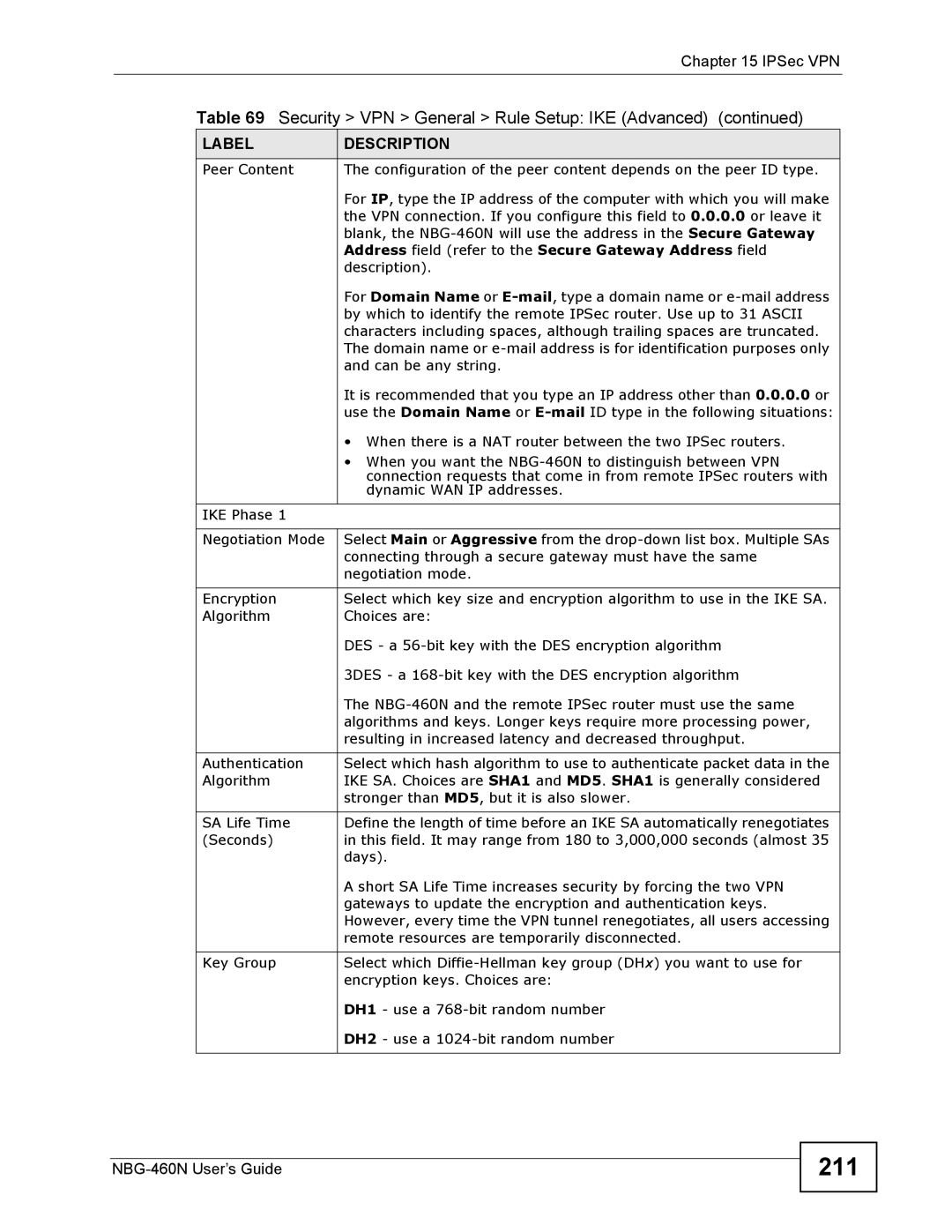
Security VPN General Rule Setup IKE Advanced
207
Select No to disable it
208
209
210
211
212
213
VPN Rule Setup Manual
Each IPSec SA. It is more secure but takes more time
214
Security VPN General Rule Setup Manual
215
216
Secure
217
SPI
218
SA Monitor Screen
Trailing spaces are truncated
IKE SA Proposal
VPN and Remote Management
219
220
Diffie-Hellman DH Key Exchange
Remote Ipsec Router
Authentication
VPN Example Matching ID Type and Content
221
VPN Example Mismatching ID Type and Content
Negotiation Mode
222
223
15.6.6 VPN, NAT, and NAT Traversal
Encapsulation
IPSec Protocol
224
SA Life Time
IPSec SA Proposal and Perfect Forward Secrecy
Additional IPSec VPN Topics
225
226
Encryption and Authentication Algorithms
Private DNS Server
Private DNS Server Example
227
228
229
Management
230
231
Static Route
Lanwan
232
IP Static Route Screen
233
Static Route Setup Screen
234
Chat, Email
Bandwidth Management
235
FTP
236
General Configuration Screen
Management check box
237
Mbps
Wlan Bandwidth
Advanced Configuration
238
Connected to the WAN port has an upstream speed of 10 Mbps
Low
239
To Wlan
Rule Configuration with the Pre-defined Service
240
Wlan to WAN
241
Rule Configuration User Defined Service Rule Configuration
242
Monitor Screen
Technical References
Predefined Bandwidth Management Services
Media Bandwidth Management Setup Services
Service Description
Class Type Priority
Default Bandwidth Management Classes and Priorities
Bandwidth Management Priority with Default Classes
244
245
Bandwidth Management Priorities
Bandwidth Management Priorities
246
247
Remote Management
248
System Timeout
Remote Management Limitations
Remote Management and NAT
Remote management
Specify to access the NBG-460N using this service
WWW Screen
249
FTP Screen
Telnet Screen
250
251
DNS Screen
You specify to send DNS queries to the NBG-460N
252
NAT Traversal
Universal Plug-and-Play UPnP
253
254
UPnP Screen
255
Using UPnP in Windows XP Example
Network Connections
256
257
Internet Connection Properties Advanced Settings
258
Web Configurator Easy Access
Network Connections My Network Places
259
Network Connections My Network Places Properties Example
260
261
Maintenance Troubleshooting
262
System General Screen
System
263
264
265
Time Setting Screen
Select User Defined Time Server Address and enter the IP
266
267
268
269
Logs
Display
Log categories that you selected in the Log Settings
View Log Screen
270
271
Log Settings
Time and date
272
Mail Log Settings Mail Server
Messages will not be sent via e-mail
Sent via e-mail
273
Smtp
LOG Message Description
System Maintenance Logs
Log Descriptions
274
275
System Error Logs
Firewall Attack Alerts screen
Access Control Logs
TCP Reset Logs
276
Packet Filter Logs
277
Icmp Logs
278
279
Content Filtering Logs
UPnP packets can pass through the firewall
Attack Logs
280
IPSec Logs
281
IKE Logs
282
283
284
PKI Logs
285
802.1X Logs
Type Code Description
ACL Setting Notes
286
Packet Direction Description
Icmp Notes
287
Syslog Logs
RFC-2408 Isakmp Payload Types
288
LOG Display Payload Type
Firmware Upload Screen
Tools
289
290
Maintenance Tools Firmware
Network Temporarily Disconnected
Upload Error Message
Maintenance Restore Configuration
Configuration Screen
Backup Configuration
Restore Configuration
293
Configuration Restore Successful
Restart Screen
Back to Factory Defaults
294
295
Indicate either Ready or MAC Address error
Wake On LAN
Green
296
Maintenance Tools Green
297
Configuration Mode
298
Advanced Configuration Options
Category Link TAB
299
Sys Op Mode
Router
300
301
Maintenance Sys OP Mode General
Firewall or bandwidth management
302
Language Screen
Language
303
304
Power, Hardware Connections, and LEDs
Troubleshooting
305
306
NBG-460N Access and Login
Advanced Suggestions
307
308
Internet Access
Internet connection is slow or intermittent
309
310
Resetting the NBG-460N to Its Factory Defaults
311
Wireless Router/AP Troubleshooting
312
Advanced Features
PWR, LAN1-4, WAN, WLAN, WPS
Product Specifications and Wall- Mounting Instructions
Hardware Features
313
314
Firmware Features
Such as microwave ovens, wireless phones
Bluetooth enabled devices, and other wireless LANs
315
Standards Supported
Feature Specifications
Feature Specification
316
317
Wall-mounting Instructions
Protocol MBM Media Bandwidth Management
Masonry Plug and M4 Tap Screw
318
319
Appendices Index
320
Internet Explorer Pop-up Blockers
Disable pop-up Blockers
321
322
Enable pop-up Blockers with Exceptions
323
Select Settings…to open the Pop-up Blocker Settings screen
324
JavaScripts
Internet Options Security
325
326
Java Permissions
Java Sun
327
Java Sun
328
Structure
Introduction to IP Addresses
329
1ST 2ND 3RD 4TH Octet
Subnet Masks
330
Subnet Mask Identifying Network Number
Binary 1ST 2ND 3RD 4TH Decimal Octet
331
Network Size
Subnet Masks
Alternative Subnet Mask Notation
Notation
332
Maximum Host Numbers
333
Subnetting
334
Example Four Subnets
IP/SUBNET Mask Network Number Last Octet BIT Value
335
Subnet Planning
Example Eight Subnets
336
NO. Borrowed Subnet Mask NO. Hosts PER Host Bits Subnets
Configuring IP Addresses
337
16-bit Network Number Subnet Planning
Private IP Addresses
338
339
Setting up Your Computer’s IP Address
Windows 95/98/Me
Installing Components
340
341
Configuring
342
Verifying Settings
343
Windows 2000/NT/XP
Windows XP Control Panel
344
Windows XP Local Area Connection Properties
345
Windows XP Internet Protocol TCP/IP Properties
346
Windows XP Advanced TCP/IP Properties
347
348
349
Macintosh OS 8/9
Macintosh OS 8/9 TCP/IP
350
351
Macintosh OS
Linux
Using the K Desktop Environment KDE
352
Red Hat 9.0 KDE Ethernet Device General
353
354
Using Configuration Files
Red Hat 9.0 DNS Settings in resolv.conf
Red Hat 9.0 Static IP Address Setting in ifconfig-eth0
356
Verifying Settings
Ad-hoc Wireless LAN Configuration
Wireless LAN Topologies
357
358
Basic Service Set
359
Channel
RTS/CTS
360
361
Ieee 802.11g Wireless LAN
Fragmentation Threshold
Preamble Type
Data Rate Modulation Mbps
Ieee
362
Ieee 802.11g
EAP-MD5 Message-Digest Algorithm
Types of Authentication
363
Types of Radius Messages
Peap Protected EAP
EAP-TTLS Tunneled Transport Layer Service
364
EAP-TLS Transport Layer Security
Encryption
Comparison of EAP Authentication Types
WPA2
365
366
User Authentication
27.0.3 WPA2 with Radius Application Example
27.0.2 WPA2-PSK Application Example
367
368
Wireless Security Relational Matrix
Authentication Encryptio Enter METHOD/ KEY
Security Parameters Summary
369
Services
370
Examples of Services
Name Protocol Ports Description
371
372
Disclaimer
Copyright
Certifications
373
FCC Radiation Exposure Statement
374
375
ZyXEL Limited Warranty
Viewing Certifications
Registration
376
CTS Clear to Send
Index
377
Classes and priorities
Essid
378
Encapsulating Security Payload. See ESP
Language Link type 40
379
IKE SA
Ethernet PPPoE. see also PPP over Ethernet
MAC
380
Mbssid
381
QoS QoS priorities Quality of Service QoS
Radius
382
Wireless security 98 overview
Xbox Live ZyNOS 39
383
384