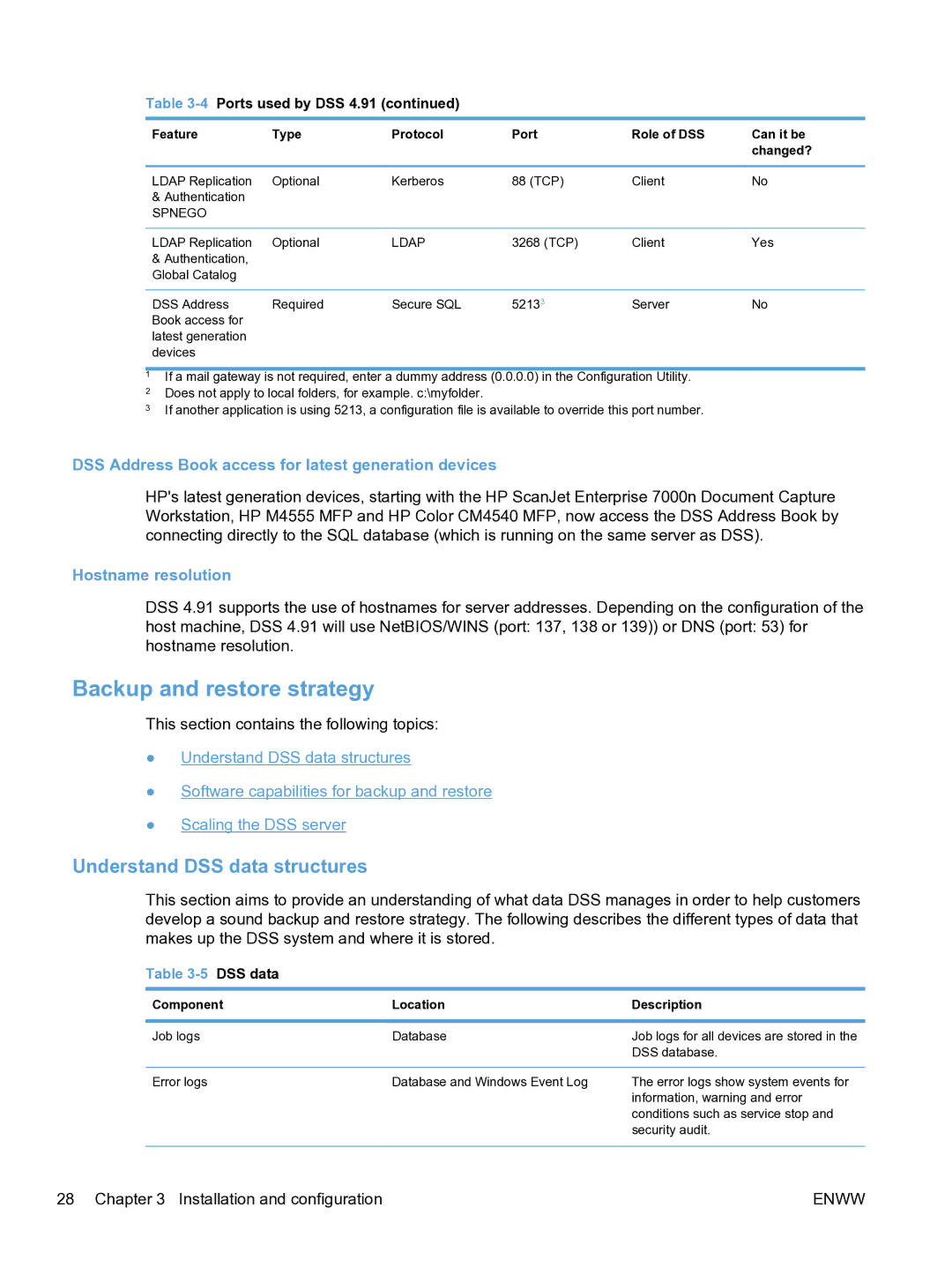
Table 3-4 Ports used by DSS 4.91 (continued)
Feature | Type | Protocol | Port | Role of DSS | Can it be |
|
|
|
|
| changed? |
|
|
|
|
|
|
LDAP Replication | Optional | Kerberos | 88 (TCP) | Client | No |
& Authentication |
|
|
|
|
|
SPNEGO |
|
|
|
|
|
|
|
|
|
|
|
LDAP Replication | Optional | LDAP | 3268 (TCP) | Client | Yes |
& Authentication, |
|
|
|
|
|
Global Catalog |
|
|
|
|
|
|
|
|
|
|
|
DSS Address | Required | Secure SQL | 52133 | Server | No |
Book access for |
|
|
|
|
|
latest generation |
|
|
|
|
|
devices |
|
|
|
|
|
1If a mail gateway is not required, enter a dummy address (0.0.0.0) in the Configuration Utility.
2Does not apply to local folders, for example. c:\myfolder.
3If another application is using 5213, a configuration file is available to override this port number.
DSS Address Book access for latest generation devices
HP's latest generation devices, starting with the HP ScanJet Enterprise 7000n Document Capture Workstation, HP M4555 MFP and HP Color CM4540 MFP, now access the DSS Address Book by connecting directly to the SQL database (which is running on the same server as DSS).
Hostname resolution
DSS 4.91 supports the use of hostnames for server addresses. Depending on the configuration of the host machine, DSS 4.91 will use NetBIOS/WINS (port: 137, 138 or 139)) or DNS (port: 53) for hostname resolution.
Backup and restore strategy
This section contains the following topics:
●Understand DSS data structures
●Software capabilities for backup and restore
●Scaling the DSS server
Understand DSS data structures
This section aims to provide an understanding of what data DSS manages in order to help customers develop a sound backup and restore strategy. The following describes the different types of data that makes up the DSS system and where it is stored.
Table 3-5 DSS data
Component | Location | Description |
|
|
|
Job logs | Database | Job logs for all devices are stored in the |
|
| DSS database. |
|
|
|
Error logs | Database and Windows Event Log | The error logs show system events for |
|
| information, warning and error |
|
| conditions such as service stop and |
|
| security audit. |
|
|
|
28 Chapter 3 Installation and configuration | ENWW |